Posts for December 2015
The evolution of data storage
Even just 15 years ago, many people could not have imagined that there would quickly come a time when we would be able to carry around libraries of images, songs, movies and TV box sets in our pockets.
Crude MP3 players at the turn of the century were capable of holding a handful of tracks within their bulky build - but the development of pocket-size hard drives and players has been swift and comprehensive.
Now, many of us take it for granted that we can carry all our important files and documents with us wherever we go - to the point where we're often guilty of never backing up these files.
Comprehensive data storage devices have become incredibly commonplace in our lives - with many people reluctant to leave their home without their mobile phone stuffed full of pictures, songs and movies.
And data storage tools are likely to only improve and develop in the future; soon enough we'll have access to a global archive of every piece of information and media right at our fingertips (we're close already).
But just how much can our everyday data storage devices hold? How much storage do you need if you want to carry every James Bond film with you at all times?
Our infographic explores how data storage has evolved over the years, from the early computer systems developed just after WWII to the almost limitless cloud storage facilities of today.
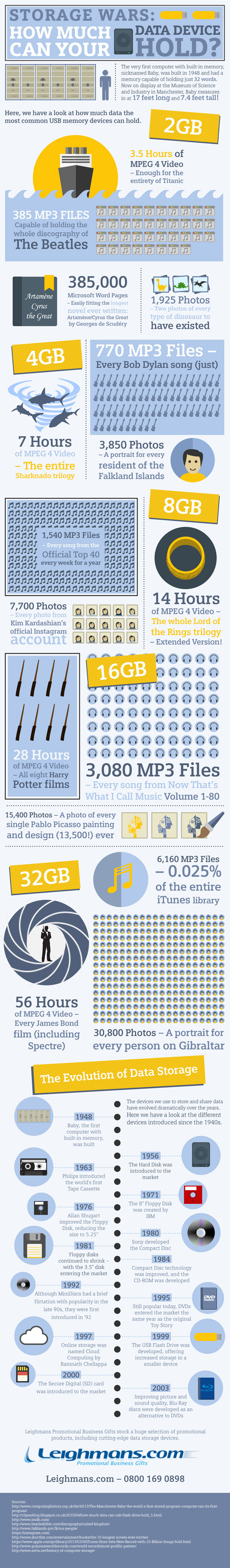
Copyright © 2015 Leighmans.
Ten things you could have learnt from our blog in 2015
 This year marked the fifth birthday of IT Donut, which has been around since August 2010.
This year marked the fifth birthday of IT Donut, which has been around since August 2010.
In many ways, 2015 could have been any of the years since then. Another new iPhone hit the market. More companies lost more data to hackers. And UK broadband still isn't good enough.
As always, we've been here trying to cover the things you need to know about - in plain English. So, here are ten things you could have learnt from our blog in 2015.
1. Text messages are over 20 years old
The humble SMS message is proving remarkable resilient, even in the face of services like WhatsApp and Facebook Messenger.
In fact, they've been given something of a new lease of life by businesses, which increasingly use them for delivery updates and security authentications. (Plus annoying marketing messages.)
2. The Duchess of Cambridge can break your website
Back in February, fashion brand Madderson London was hit by the 'Kate effect' when the Duchess of Cambridge was pictured wearing one of the company's dresses.
The company's website crashed under an influx of visitors. And that must have been frustrating, given the opportunity for extra sales.
We won't all have the Duchess as customers, of course. But many different things can trigger a rush of website visitors. When each is a potential customer, you want to be sure your site holds up.
3. Google is serious about Microsoft Office
Google has offered its own equivalent to Microsoft Office for almost a decade. And for that entire decade, Microsoft Office has reigned supreme.
In March, we reported that this might be changing. After years of constant development, Google Apps for Work is mounting a fresh challenge.
The search giant reckons you can use its products seamlessly with Microsoft Office files. And it claims to be working hard to develop features that are genuinely useful.
Microsoft Office isn't going anywhere yet. But a bit of competition in this space is very welcome.
4. Mobilegeddon didn't break the internet
You must remember this one. Near the start of the year, Google warned website owners that it would be updating its ranking algorithm to show mobile-friendly websites higher in results lists.
As the date of the update approached, SEO pundits rushed to explain what you needed to do to retain your rankings.
With no overpriced SEO services to sell you, our advice was a bit more relaxed. 'Don't panic,' we said 'but do start thinking'. And yes, in 2016, having a mobile-friendly website will be more important than even.
5. Always check if it's down for everyone
If your website goes offline, you may well have cause to panic. If you sell online, downtime means lost sales.
Hold on though. Before you do start panicking, it's wise to make sure your website really is down. You can use Down for everyone, or just me?
And if it turns out your website is unavailable for everyone, we prepared four other tips to help you get back online quickly.
6. Your website visitors are impatient
Your website visitors don't like to wait. According to some research, 47% of people expect a page to load in under two seconds. 40% will leave a site that takes more than three seconds to load. And four out of five online visitors will click away if a video stalls while loading.
In other words, the performance of your website matters.
That's why Google started testing a 'slow to load' warning in its search results. And why we took a look at easy ways to test how fast your website loads.
7. Argos sales hit £1bn on mobile devices
I must admit, I have a soft spot for Argos. I once had a weekend job picking items in the stockroom and sending them down a conveyor belt where shoppers could collect them.
The retail giant somehow survived the wave of bankruptcies that hit during the financial crisis. Since then, it's attempted to stay competitive by updating its stores and introducing same-day delivery.
Impressively, Argos became the first UK retailer to generate over £1bn of mobile sales in a year, underlining how quickly m-commerce has been growing.
8. It's easy to create a disposable email address
If spam drives you crazy, perhaps a disposable email address could help keep you main inbox under control.
Services like Mailinator and 10 Minute Mail give you instant access to addresses that can receive messages, without putting you through the hassle of signing up for an account with a free email provider.
Disposable email addresses do exactly what you'd expect. You can use them in situations where you need a valid address, but you don't want to enter your own details.
9. There are legitimate uses for private browsing
You might know that most web browsers have a private browsing feature, so you can visit websites without leaving a trail in your history or having them store cookies on your computer.
It's easy to see how private mode might be used to hide your internet activities from other users of your computer. But did you know it has some uses in business, too?
We explain how it can help you test your website, sign in to multiple online accounts - and make public computers safer.
10. We're all failing on security
One of this Autumn's biggest tech news stories revealed that telecoms company TalkTalk had been hit by a cyber attack. Almost 157,000 people had their personal details hacked.
This is one in a long, depressing line of IT security breaches. We've been reporting them for years, and they just keep happening.
Their repetitive nature - along with some interesting new research - got us wondering if the drip, drip, drip of security breaches might be having a long-term impact on consumer trust.
Goodbye for 2015
So, that's IT Donut done for another year. Our team will be taking a well-earned break over Christmas before returning with new posts in January. In fact, there are some exciting things planned for the site next year, so make sure you keep an eye on this site.
However, I've decided to make this my last contribution to IT Donut. After five exciting years, it's time for me to move on. So, thanks for reading!
Should you be worried about mobile security?
 Mobile devices are everywhere in the workplace. Chances are, they're everywhere in your workplace too - no matter whether you like it or not. So, as every smart phone is a powerful computer in its own right, should you be thinking about mobile security?
Mobile devices are everywhere in the workplace. Chances are, they're everywhere in your workplace too - no matter whether you like it or not. So, as every smart phone is a powerful computer in its own right, should you be thinking about mobile security?
A change driven by BYOD
As mobile devices became more popular for personal use, the trend of 'bring your own device' (BYOD) started to emerge.
BYOD is when your employees use their personal mobile devices for work. For instance: checking their company email while out and about, or accessing your CRM software from their tablet.
Some companies have embraced BYOD, encouraged by the chance to increase productivity without spending a fortune on smart phones. Besides, businesses without a BYOD policy often find BYOD happens anyway, as staff members act on their own initiatives.
This added flexibility brings with new challenges for smaller companies. As an increasing number of devices are used to access company information, the number of opportunities for viruses, hackers and other threats increases, too.
Cyber-criminals target smaller companies
It's a mistake to think cyber-criminals won't be interested in your small company. As IT Donut has mentioned before, hackers often see smaller firms as attractive targets, because they have smaller IT security budgets.
What's more, cyber-criminals are increasingly choosing to focus on mobile devices. US statistics suggest that the amount of malicious software aimed at mobile devices has risen 185% in less than a year.
Why? Well, mobile devices are tempting because they're vulnerable. One survey found that over 80% of smaller businesses were not interested in information about managing the information security of mobile devices.
Mobile devices lack security
Mobile devices were conceived as consumer products. This means they have little security built in. As a result, it may be much easier to spread malware via mobile devices than via desktop computers.
And - of course - it's easy to lose a mobile device. When you leave your smart phone on the train or in a bar (or have it stolen), you don't just lose the device. You risk losing the data on it, too.
It's also wise to be aware of how employees' regard security while they are out of the office. For instance, is it easy for strangers to read company information over their shoulder while they're on a train?
Solving mobile device security
The worst thing your can do is bury your head in the sand. Mobile working is here and bigger than ever, so you must create a security strategy that incorporates these handheld powerhouses. You can ignore the cyber-criminals, but they might not ignore you.
Take some time to assess the specific risks your business faces. For instance, who uses mobile devices in your company? What do they use them for? What sort of data could you lose, and where might it end up?
You can then introduce a mobile usage strategy to secure those devices and manage these devices.
Importantly, make sure you have a way to disable and wipe each device if it is lost or stolen. Mobile device management (MDM) software can help you manage the security of devices centrally (and can sometimes even cover those owned by employees), so you might consider this as an option.
Furthermore, make sure mobile apps are checked for malware, and look at installing security software on your devices.
Importantly, don't forget the human factor. Make sure members of staff receive IT training so they understand the risks of mobile security and can help your business avoid issues.
For instance, reporting a lost device promptly can make a big difference as to whether data falls into the wrong hands.
Evaluate security software carefully
One of the challenges facing smaller companies concerned about mobile security is that software in this area tends to be aimed at bigger businesses. However, a good IT supplier should be able to identify software that fits your needs well.
In the current climate, it would be naive to ignore mobile security. However, with a little thought, there is nothing to stop you making BYOD work safely for your business - leading to a happier, more flexible and efficient workforce.
Copyright ©2015 Albie Attias, managing director of leading IT retailer, King of Servers. He specialises in helping businesses find the best solution for their IT and business needs.



