Blog posts tagged security
Should you be worried about mobile security?
 Mobile devices are everywhere in the workplace. Chances are, they're everywhere in your workplace too - no matter whether you like it or not. So, as every smart phone is a powerful computer in its own right, should you be thinking about mobile security?
Mobile devices are everywhere in the workplace. Chances are, they're everywhere in your workplace too - no matter whether you like it or not. So, as every smart phone is a powerful computer in its own right, should you be thinking about mobile security?
A change driven by BYOD
As mobile devices became more popular for personal use, the trend of 'bring your own device' (BYOD) started to emerge.
BYOD is when your employees use their personal mobile devices for work. For instance: checking their company email while out and about, or accessing your CRM software from their tablet.
Some companies have embraced BYOD, encouraged by the chance to increase productivity without spending a fortune on smart phones. Besides, businesses without a BYOD policy often find BYOD happens anyway, as staff members act on their own initiatives.
This added flexibility brings with new challenges for smaller companies. As an increasing number of devices are used to access company information, the number of opportunities for viruses, hackers and other threats increases, too.
Cyber-criminals target smaller companies
It's a mistake to think cyber-criminals won't be interested in your small company. As IT Donut has mentioned before, hackers often see smaller firms as attractive targets, because they have smaller IT security budgets.
What's more, cyber-criminals are increasingly choosing to focus on mobile devices. US statistics suggest that the amount of malicious software aimed at mobile devices has risen 185% in less than a year.
Why? Well, mobile devices are tempting because they're vulnerable. One survey found that over 80% of smaller businesses were not interested in information about managing the information security of mobile devices.
Mobile devices lack security
Mobile devices were conceived as consumer products. This means they have little security built in. As a result, it may be much easier to spread malware via mobile devices than via desktop computers.
And - of course - it's easy to lose a mobile device. When you leave your smart phone on the train or in a bar (or have it stolen), you don't just lose the device. You risk losing the data on it, too.
It's also wise to be aware of how employees' regard security while they are out of the office. For instance, is it easy for strangers to read company information over their shoulder while they're on a train?
Solving mobile device security
The worst thing your can do is bury your head in the sand. Mobile working is here and bigger than ever, so you must create a security strategy that incorporates these handheld powerhouses. You can ignore the cyber-criminals, but they might not ignore you.
Take some time to assess the specific risks your business faces. For instance, who uses mobile devices in your company? What do they use them for? What sort of data could you lose, and where might it end up?
You can then introduce a mobile usage strategy to secure those devices and manage these devices.
Importantly, make sure you have a way to disable and wipe each device if it is lost or stolen. Mobile device management (MDM) software can help you manage the security of devices centrally (and can sometimes even cover those owned by employees), so you might consider this as an option.
Furthermore, make sure mobile apps are checked for malware, and look at installing security software on your devices.
Importantly, don't forget the human factor. Make sure members of staff receive IT training so they understand the risks of mobile security and can help your business avoid issues.
For instance, reporting a lost device promptly can make a big difference as to whether data falls into the wrong hands.
Evaluate security software carefully
One of the challenges facing smaller companies concerned about mobile security is that software in this area tends to be aimed at bigger businesses. However, a good IT supplier should be able to identify software that fits your needs well.
In the current climate, it would be naive to ignore mobile security. However, with a little thought, there is nothing to stop you making BYOD work safely for your business - leading to a happier, more flexible and efficient workforce.
Copyright ©2015 Albie Attias, managing director of leading IT retailer, King of Servers. He specialises in helping businesses find the best solution for their IT and business needs.
The TalkTalk aftermath: are we all failing to deliver on security?
 At the end of last week, broadband and telecoms company TalkTalk announced it had been hit by a cyber attack. As a result, there was a chance sensitive customer data had been accessed.
At the end of last week, broadband and telecoms company TalkTalk announced it had been hit by a cyber attack. As a result, there was a chance sensitive customer data had been accessed.
This is just the latest in a string of high-profile attacks. From eBay and Kickstarter to Tesco and more, TalkTalk and its customers aren't alone in suffering at the hands of digital criminals.
Is security tight enough?
Clearly, the ultimate blame for these incidents lies with the attackers who set out to steal data. They're the real criminals in this scenario.
But at the same time, it's fair to say that some organisations are making it too easy for hackers to steal sensitive data. Although we don't yet have full details of the TalkTalk incident, other newsworthy breaches have involved below-par security measures.
Such is the frequency of these stories that you could be forgiven for shrugging each off as 'yet another cyber attack'. But as new research reveals a lack of trust in business, it would be unwise to ignore the cumulative impact of these incidents.
Low trust is higher than ever
Digital identity experts Intercede recently released some interesting research. It suggests people don't tend to trust businesses when it comes to protecting their personal information.
The survey questioned around 2,000 people aged 16-35. These people are often referred to as 'millenials', and tend to be comfortable using technology during their everyday lives.
It might therefore come as a surprise that the research found a significant proportion of these people have little trust in business to protect their personal information.
The research asked people to rate their trust in businesses from different sectors. When it comes to data security, 61% of respondents described their level of trust in social media platforms as 'none' or 'a little'. The figure was 38% for retailers and 19% for financial institutions.
Indeed, few people describe their level of trust as 'complete' - just 13% for their employers, and 4% for telecom operators.
Time to up our security game?
The same group of people was asked about how organisations share data. Many respondents said that their personal data should only be shared with companies they have specifically authorised.
Over 74% of people said that it was 'very important' or 'vital' that they should be able to specifically authorise how their location data is shared. 58% said the same for social media content and 57% for data on their purchasing preferences.
"Millennials are hungry for change," reckons Lubna Dajani, a communications technology expert and futurist. "Major data breaches happen every week and millennials, along with the rest of the general public, have found the trust they put in government institutions and businesses to protect their digital identities are being shaken."
"This is by no means an apathetic generation. If business and government leaders don't adopt better protocols now, millennials will soon rise up and demand it."
Is your business ready for the unexpected?
 Earlier this year, an underground fire in Holborn caused days of disruption for businesses based in that part of central London. As this event hit the news, it raised an important question for businesses: what plans do you have in place for the unexpected
Earlier this year, an underground fire in Holborn caused days of disruption for businesses based in that part of central London. As this event hit the news, it raised an important question for businesses: what plans do you have in place for the unexpected
The incident received widespread coverage and some estimates put the cost of disruption at £50m.
Some businesses were unable to enter their premises for days and employees had to leave their laptops and smart phones behind. Many staff were sent home and power outages hit telephone systems and servers.
When something like this happens, some disruption is inevitable. But if you prepare, you can minimise the problems you face.
Telecoms is key
It’s not just dramatic, newsworthy events that cause disruption. Inclement weather (snow, floods or heat), transport issues and more can all cause problems for your company.
It’s worth your company having a continuity plan in place so you have some idea of what to do if a crisis hits. There are several aspects to think about, but your telecoms form a key element.
If a problem was to affect your organisation, how would your customers get in touch and how would you continue to operate? Some surveys have shown that losing communications can cost a company thousands of pounds a day.
How to prepare for problems
Equinox provides telecoms services to UK businesses. Dave Millet, director there, recommends asking a few key questions:
- If your business uses a traditional phone system, have you investigated whether a call divert feature is available? This allows you to reroute calls during a crisis.
- If you use a voice over IP telephone system, you may be able to sign in to an online control panel to divert calls when your staff are working elsewhere. But do you know how?
- Similarly, some of these systems offer an ‘automatic failover’ feature, which re-routes calls for you in the event of a problem. Have you set this feature up?
- How is your company data backed up and where are the backup copies held? If you were unable to get into your premises, would you know how to access your data?
- Do you have a list of everyone you should call in a crisis? And are copies easily available? You might need to get hold of employees, telecoms providers, IT suppliers and more – all in a hurry.
It can be hard to know how much time and money to spend creating and testing business continuity procedures.
But a good way to start is to estimate the cost of a day’s lost business. If this figure is large, you can justify a greater investment in building resilience into your systems and procedures.
Being prepared means taking action now - not waiting until something happens. Hopefully you will never need to put your plans into practice. However, if you do, it could be the difference between survival and bankruptcy.
The biggest threats to your business
What are the real digital threats to your business? When you’re thinking about IT security, it can be hard to know where you to focus your time and energy. (Believe everything you read in the news and there are dangers lurking around every corner!) To help companies understand the real risks out there, recruitment firm Modis has created this infographics explaining business security issues. It is a little US-centric, but we still think it contains some helpful information.
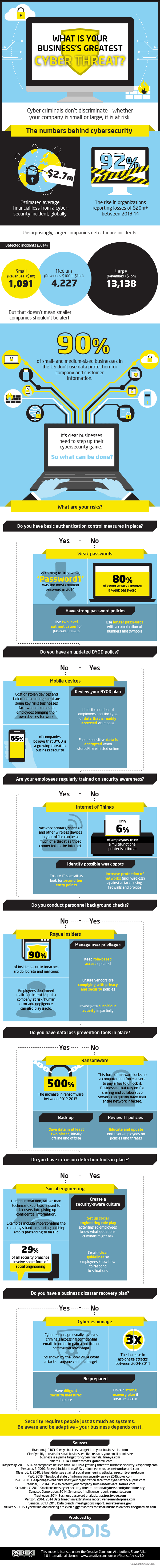
What’s Your Business’s Greatest Cyber Threat [Infographic] by the team at Modis
How to defend your business during the four stages of a cyber-attack
Every one and a half seconds, another organisation is hit by a cyber attack. There’s one now. And there. And there.
Are you prepared to defend your business?
Thousands of security breaches
Even a minor security breach can hit your business hard. And if you’re unlucky, it could cost you up to £65,000 to recover.
If you’ve not considered how you might cope in a crisis, your business and your data could be at risk.
The bad news? It’s easy for a hacker to launch a sneak attack. The good? Nearly all attacks are preventable.
To protect your company from a security breach, you need to understand the four stages of a typical attack. Then you can make sure you have the right security protocols in place.
Stage one: the crack in the wall
A major data breach usually begins with something small, like an employee falling for a phishing attack and opening a bad email attachment. The infamous Sony Pictures hack may have begun in this way.
To keep this from happening, make sure your employees have a grounding in basic security. Anything coming in to your company should only be accepted if employees know and trust the source.
If the crack in the wall has already appeared, delete any suspect files, disconnect any affected computers from your network and sweep the computer for any traces the file may have left behind.
Removing some malware can be notoriously tricky, so it’s a good idea to bring in your IT support company. A small amount of money spent now can help limit your future losses.
Stage two: information gathering
Once a hacker has gained access to your systems, they’re likely to start gathering valuable information.
For instance, that bad attachment could have installed keylogging software that can record every keystroke. This can give the hacker access to usernames and passwords, email addresses, credit card details and more.
As a preventative measure, make sure every computer in your business is running up-to-date anti-virus and security software.
If keylogging software is detected, reset all passwords in your business – even if you think they haven’t been compromised.
Stage three: the stolen password
Once a hacker has begun collecting your passwords, they can use them to get much deeper into your systems.
To prevent one stolen password giving the hacker an all-access pass to your data, set up permissions and controls so each person in your business can only access the resources they need.
For instance, there’s probably no need for your sales team to have access to the full company accounts.
Stage four: disaster
Once hackers have access to your company’s servers, your data is at their mercy. They can easily steal sensitive information and even wipe it completely, causing irreparable damage.
To prevent disaster, you can use real-time audit reporting to detect suspicious activity. Your policy should be to disconnect first and ask questions later.
If your data does get wiped, be prepared with off-site backups that are updated regularly. Having your data stolen is terrible, but losing it altogether could kill your business.
Most cyber attacks are easily preventable, and common intrusions usually take several days to complete.
By putting these simple security measures in place and knowing how to prevent hackers from seizing control of your data at every stage in the process, you can sleep more easily at
night.
Copyright © 2015 Kris Lahiri, co-founder and the VP Operations and Chief Security Officer of Egnyte
Government suppliers now have to be more secure
 From the beginning of October, many businesses that supply the government must conform to its new Cyber Essentials standards.
From the beginning of October, many businesses that supply the government must conform to its new Cyber Essentials standards.
The new rules apply if you’re bidding for government contracts that involve handling sensitive or personal information, or providing certain technical products or services.
Cyber Essentials is a pair of new ‘kitemarks’ for cyber security. There are two levels:
- Cyber Essentials, which requires you to complete a questionnaire that gets reviewed by an external certifying body.
- Cyber Essentials Plus, which will see your IT systems actually tested for security issues and weaknesses.
These standards are designed to provide a good foundation in security. In a world where many organisations still don’t give enough thought to how they handle information, they aim to drive up basic security, ultimately keeping sensitive data safer from hackers and other threats.
Once your business has achieved one of the two Cyber Essentials levels, you’ll be awarded a certificate and gain the right to show the relevant Cyber Essentials badge on your marketing materials.
It’s still early days, but in time, it’s hoped these logos could become recognisable, reassuring potential customers that your business takes data security seriously.
In any case, it’s probably fair to say that these two standards formalise what would be a prudent approach to security in any case.
“Cyber Essentials is genuinely the minimum level of cyber security that every organisation should have in place,” confirms Alan Calder, founder of IT Governance.
So, no matter whether or not you’re planning to bid for government work, getting accredited could be a good way to give your security precautions a once-over.
If you’re interested in achieving one of the Cyber Essentials standards, you can learn more from the Cyber Essentials website.
The Hitchhiker's Guide to Hacking
 Security company Norton has created a Hitchhiker’s Guide to Hacking web page. And as a confirmed fan of Hitchhiker’s Guide to the Galaxy, I can’t quite decide what to think of this.
Security company Norton has created a Hitchhiker’s Guide to Hacking web page. And as a confirmed fan of Hitchhiker’s Guide to the Galaxy, I can’t quite decide what to think of this.
On one hand, it’s been put together with real care. The information is detailed and someone has spent significant time on the design.
Unlike many such infographics, it’s not been knocked together in five minutes by someone who has a basic knowledge of Microsoft Paint. (Actually, most of the information is text-based, but the illustrations are nicely done.)
But on the other hand, we’re talking about the Hitchhiker’s Guide to the Galaxy, probably one of the world’s best-loved modern stories. Is it right for Norton to use its instantly recognisable identity as part of a PR campaign?
Maybe it’s best for you to decide for yourself. You can check out the Hitchhiker’s Guide to Hacking here. It’s worth a look, if only for the depth of information it contains.
Google plans to reward sites that are secure

Google's busy making changes to its ranking algorithm again. This time, the search giant has decided that websites which use a secure connection as standard should get a boost in search results.
Historically, secure connections have only been used to transfer sensitive information, like credit card details. The secure, encrypted connection is signified by https:// at the beginning of the website address, and a small padlock shown somewhere in your web browser.
The argument for more security
There's a good argument for using secure connections more widely. Perhaps most significantly, they're an effective way to prevent 'man in the middle' attacks. These occur when an attacker intercepts data as it travels between a user's computer and a web server.
When a website uses a secure connection, attackers may still be able to intercept the data. But because it's encrypted, they won't be able to understand it.
As well as protecting data from attackers, this change may also represent something of a shift in attitudes around security.
Between Edward Snowden's revelations and the data breaches that hit the headlines month after month, awareness is slowly growing about the need to protect data online.
A significant impact
Jason Hart, VP at SafeNet, reckons this change by Google will have a significant impact on how organisations secure their websites:
"Every company wants to rank favourably on Google, so it’s in their best interest to ensure web pages are encrypted."
And although using encryption can hit website performance, these days the affect is negligible. "There are now high speed encryption technologies available that mean cost and speed need no longer be an issue," continues Jason.
"So there really is no excuse for any data to be transmitted or stored in plain text."
No need to panic ... yet
If your website doesn't currently use a secure connection, there's no need to panic. At present, the same is true for the majority of websites.
In its blog post summarising the changes, Google also confirmed that, initially, security will have a very small influence on search rankings. However, it may become a more significant factor in time, so it's a good idea to think about how to add a secure connection to your website.
To secure your website, you need an SSL certificate. The SSL stands for secure sockets layer. SSL certificates are available from most web hosting companies, and are sometimes included with web hosting services.
However, setting up an SSL certification can sometimes be tricky. If you're ready to make your site more secure, you might want to consult your web developer or IT supplier.
Although you don't need to act now, this latest move by Google definitely means it's worth finding out what it will take to make your website more secure.
Now Microsoft says weak passwords can be good
 If there’s one piece of IT security advice that’s generally not up for debate, it’s that you need to use strong passwords.
If there’s one piece of IT security advice that’s generally not up for debate, it’s that you need to use strong passwords.
Some of the most common passwords are things like ‘password’ and ‘123456’. Hackers can guess these in minutes, so it’s a really bad idea to use them.
The usual advice is to use passwords that:
- Aren’t dictionary words
- Contain a mix of upper and lower case letters
- Contain numbers and symbols
- Are as long as possible
For instance, a password like ‘YY6^nUCFT/g}k3Cb’ is going to be hard for hackers to guess. You can get advice about choosing strong passwords here.
Don’t use strong passwords?
But now Microsoft researchers have recommended (PDF link) we use and reuse weak passwords on low-risk websites that don’t hold valuable information.
The theory goes something like this: by not having to struggle to remember complicated passwords for every single website, we can focus more of our efforts on creating and memorising strong passwords on the websites that really matter.
Why this is bad advice
On the face of it this sort of makes sense, but it starts falling apart when you try to actually put it into practice. Here’s why:
- It’s hard to know which website accounts are most important. Even some innocuous websites hold sensitive data like your date of birth. It’s not uncommon for hackers to piece together the information they need for identity theft from several different website accounts.
- Memorising strong passwords is too hard anyway. Regardless of what Microsoft says, your average website user doesn’t have the time nor inclination to memorise passwords like ‘YY6^nUCFT/g}k3Cb’ — even if they only need to do so for a few websites. It’s simply asking too much.
- It makes the world of passwords more confusing. The message that strong passwords are important is easy to understand. Being told it’s sometimes ok to use weak passwords dilutes that message — particularly when there’s no solid definition of what constitutes a ‘low risk’ website.
Although Microsoft’s intentions are good, research like this risks causing more problems than it solves.
As other security experts have argued, you’re probably better off using a password manager to create strong passwords and keep track of them all.
Blog by John McGarvey, IT Donut editor
How managed security software can keep you safe
 Earlier this year, hundreds of thousands of websites were affected by the heartbleed security flaw.
Earlier this year, hundreds of thousands of websites were affected by the heartbleed security flaw.
Heartbleed was a massive headache, but also acted as a reminder that large-scale security breaches can — and do — happen.
It’s not just down to IT staff and security experts to take action. Business owners have a role to play, too.
There are many things you can do to protect your business from online threats. The security section of IT Donut is an excellent place to start.
One of the most important things to think about is anti-virus and security software. These programs scan your computers for viruses, spyware and other malware. They also monitor your network for suspicious activity, and can identify and remove email threats.
Just a single piece of malware can leave your systems wide open, paving the way for hackers to enter and steal your data. Security software is a key countermeasure.
Finding the right security software
It’s easy to realise that you need security software. But there’s a bewildering choice of options, making it actually quite hard to pick one that meets your needs and budget.
And even when you’ve chosen your security software, just having it isn’t enough. In order for it to be effective, it needs to be:
- Installed on every computer and server you have
- Kept up to date, with details of all the latest threats
- Turned on and set to perform regular scans
If you don’t meet these three requirements, your company will be at risk of a malware attack and data breach.
What do your users do?
Got all that sorted? Great. The next things you have to worry about are user habits.
Security software is only effective if it’s running on all your computers at all times. Unfortunately, it can sometimes slow computers down, block other software or force you to wait while it performs a scan.
For these reasons, you might find that your employees close the security software on their computers, disable the scanning functions, cancel updates — or change settings in some other way that makes the software less effective.
It’s easy to get overwhelmed by the job of making sure your security software is running properly and checking your employees haven’t interfered with its settings.
And that’s where managed anti-virus and security software comes in.
What is managed security software?
Managed security software works much the same as other security packages. It helps keep your systems secure and free of malware.
The main difference is that the software is managed by someone else. This is usually done by an IT provider (like your IT support company), but can be done by someone in your business, if you have the expertise in-house.
Whoever manages the security software takes responsibility for ensuring the solution is installed on every system and is always kept up to date.
Usually, software on individual computers and servers will be managed from a central control panel. For instance, changes to settings and updates can be rolled out across all computers automatically.
This is great for many smaller businesses because it means they don’t need to worry about the installation or day-to-day management of security software.
If you adopt managed security software, it can give you the benefit of knowing your systems and data stored are secure, without having to get into the ins and outs of checking every computer and every setting yourself.
- How to choose security and anti-virus software
- Security software FAQ
- How to perform an IT security risk assessment
(c) Mirus IT, provider of managed security software to smaller companies.
Five low-tech ways to keep your business IT safe

A flooded office in Windsor, Feb 2014. Image: Steve Mann / Shutterstock.com
IT security experts talk a lot about avoiding viruses and spyware. In the wake of the GOZeuS malware issue, you can't move for advice on how to avoid phishing.
But although a lot of IT security advice tends to focus on issues like these, there are many less high-tech threats to your business IT.
For instance, according to research from Inhance Technology, over 20% of people are more worried about being mugged for their smart phone or tablet than they were a year ago.
So, in the race to keep your devices free of viruses and your servers locked down from hackers, are you neglecting the more basic precautions?
As a reminder, here are five ways to protect your servers, computers and mobile devices from the low-tech threats that can damage your business:
- Label everything. Sticky labels aren't going to deter many criminals. But they might help get items back if they get lost, or if the police recover them. Keep a record of the serial number for every piece of hardware too. Learn more about asset tracking.
- Don't be obvious. When you issue mobile devices to staff, encourage them to carry them discreetly. For instance, don't give staff laptop bags that scream 'steal me'. Instead, keep laptops inside foam sleeves that can be carried in ordinary bags.
- Lock things up. Don't leave laptops or other portable equipment lying around in your office. Operate a locked-drawer policy, requiring employees to lock away laptops or any other valuable devices when they go home for the evening.
- Keep servers off the ground. It's not just businesses on flood plains that should be wary of water. Burst pipes can cause damage anywhere. To minimise risks to servers, keep them off the ground and — ideally — locate them on or above the first floor.
- Be wary of public places. Make sure employees don't work on confidential documents or have sensitive phone calls in public places. The last thing you want is for a competitor to overhear your plans on the 1846 train home. (Yes, it does happen.)
Have you been caught out by any low-tech security issues? Leave a comment to let us know.
Is your password on this lady's dress?

You should never use something like 'password', '123456' or your name as your password. Not for anything. Most people know this, yet plenty of us still do it.
Now artist Lorrie Cranor has come up with an original way to highlight rubbish passwords. She's had them printed on a dress.
Yes, she really has. No, this isn't a joke.
As Lorrie explains over on her blog, she used Wordle to create a word cloud of the most popular passwords revealed by the RockYou hack, then rearranged the resulting words before having them printed onto fabric.
She subsequently made this into a striking dress. The larger the word, the more common the password.
As way to start conversations about IT security, we suspect this is hard to beat. And given the coverage it has received, it's done a good job of raising the profile of poor passwords.
Now we just have to stop using them.
Is Bitcoin the answer to your business security woes?
 There’s a lot of debate surrounding Bitcoin, and for good reason. This unregulated electronic currency is not backed by a central bank and its value fluctuates wildly.
There’s a lot of debate surrounding Bitcoin, and for good reason. This unregulated electronic currency is not backed by a central bank and its value fluctuates wildly.
The Internal Revenue Service (the US equivalent of HMRC) recently decided to treat Bitcoin as property (not a currency). This could have a major impact on the volume of transactions conducted using Bitcoin.
However, while Bitcoin itself is controversial, the encryption technology behind it could be the future of digital security.
How Bitcoin security works
Bitcoin uses an accepted security concept called asymmetric key encryption. When you download a Bitcoin wallet — in which you store your Bitcoins — you’re assigned two encryption keys.
There’s a public encryption key, which you give to anyone from whom you want to receive Bitcoin payments.
Then there’s a private key. This is mathematically linked to your public key, and is used to decrypt information encrypted with your public key.
In practice, this means anyone who wants to pay you can encrypt the transaction using your public key. But only you can decrypt it to receive the money, because only you have the private key.
Bitcoin encryption for email and the cloud
Some email providers use a similar system called Pretty Good Privacy (PGP) encryption to send emails securely.
However, as PGP stores your private encryption key on an email server, hackers (or the government) could potentially intercept and decrypt your messages.
A more secure option is to encrypt emails using a Bitcoin key before you send them through your provider’s servers.
You can apply this same concept to data stored in the cloud. If you encrypt it with a Bitcoin key, your information will stay safe even if someone hacks into your cloud provider.
The risks of Bitcoin encryption
While these security measures do offer extra protection, the risks of Bitcoin encryption lie in the human element.
If you don't secure your virtual Bitcoin wallet, you can fall victim to theft. Really, keeping your wallet offline and protecting it with a password is the only straightforward way to secure it.
And you should always remember that encryption is a double-edged sword. If you ever lose your password, your data is lost forever.
The future of Bitcoin
While some governments have banned or restricted its use as a currency, Bitcoin is gaining support among some businesses. There’s even a Bitcoin cash machine in East London.
The supply of Bitcoins is limited and their volatility means the cost of security can easily surpass the value of what you’re protecting.
But perhaps the true value of Bitcoin lies in its potential to educate more people about using encryption to secure information.
In this digital age, information is currency. You should protect yours just as you would protect your money.
- How to protect your laptop with encryption
- SSL encryption for your website
- Protecting data on USB drives
Tim Maliyil is the CEO and Data Security Architect for AlertBoot.
What Apple's security flaw can teach your business
 The Heartbleed security flaw — discovered in April — affected more than 60% of web servers. As a result, some experts considered it to be the most dangerous security flaw on the web.
The Heartbleed security flaw — discovered in April — affected more than 60% of web servers. As a result, some experts considered it to be the most dangerous security flaw on the web.
However, it’s not the first big security issue in history. And it certainly won’t be the last.
For instance, Apple endured a similar situation earlier this year. Its ‘goto fail’ bug exploited a vulnerability similar to Heartbleed, but Apple handled it well enough that it didn’t achieve the same level of news coverage.
So, what can your business learn from Apple’s goto fail debacle?
1. Accept that software flaws occur
Quite simply, flawless software is a myth. Writing computer code is difficult and modern software is complex. The greater the complexity, the greater the risk of security flaws.
Although goto fail was the result of sloppy code in Apple’s operating system, Heartbleed’s vulnerability runs deeper. Either way, these breaches demonstrate that even tech giants with a lot to lose can’t make their software invulnerable.
2. Constantly monitor your software
Once you’ve accepted the risk, be more vigilant about the software you use.
The code behind Apple’s operating system framework is reviewed more often than iTunes updates its terms and conditions. Yet the flaw existed for 18 months before it was revealed. Heartbleed went undetected for two years.
Unless you want your security flaws to be discovered by a rival — or worse — stay vigilant.
3. Lock down your data and be paranoid
Be careful what you download, what you click, and what access you grant applications and websites. You become a target whenever you share private or financial information.
Pay attention to the cloud services you use, the software developers you work with, and everyone else involved in your technology. You should be in control of what they can and can’t see.
Use two-step verification where possible, encrypt data and closely monitor the security of websites you use. Most importantly: question every inconsistency.
4. Use credit monitoring
Identity thieves are known for using basic consumer data (name and address history) to open financial accounts in another person’s name. It can happen to businesses, too.
Run credit reports and regularly check the registered details of your company to catch misuse of your information.
5. Consistently check for updates
In 2011, Sony missed a software update. Within a month, customer data was leaked online. It damaged the company’s reputation and cost a lot of time and money to fix.
When Apple corrected its software flaw, it immediately released an update. But you have to actually install it to fix the problem in your business.
Every operating system and most other software can automatically check for updates regularly. Make sure yours does.
6. Act immediately
Apple admitted its flaw and immediately implemented a fix. Yet when US retailer Target suffered a major breach in 2013, it kept things quiet and attempted to fix the issue behind the scenes.
In the long run, Apple’s vulnerability was a slight inconvenience felt by very few. Target’s affected millions and cost the company more than $1bn.
The internet is like a medieval fortress. You’re only as safe as the walls around you. By running frequent security audits, properly training employees and extensively testing software, you’re building a solid castle to keep data safe.
- The £65,000 security breach
- Using security software to protect your business
- The last rites of traditional IT security?
Daniel Riedel is CEO of New Context.
GOZeuS and CryptoLocker: why you have a week to protect yourself
 Don't panic, but you have a week left to protect yourself and your business from an online threat called GoZeuS. That's according to official Government advice, no less.
Don't panic, but you have a week left to protect yourself and your business from an online threat called GoZeuS. That's according to official Government advice, no less.
So, what are GOZeuS and CryptoLocker? And why is the next week a critical period?
Disrupting the efforts of online criminals
You might not realise it, but there are battles happening online at this very moment.
On one side, hackers and online criminals are constantly finding new ways to steal data, pinch money and cause harm. On the other, security companies and government agencies are working to disrupt these criminal activities.
Recently, a group of organisations led by the FBI announced a significant victory. Experts have significantly disrupted the GOZeuS and CryptoLocker malware, which have been stealing people's data and holding their computers to ransom.
GOZeuS and CryptoLocker explained
GOZeuS is a piece of malicious software that can infect your PC, just like a virus. You can catch it from opening an infected email or visiting a dodgy website. It's estimated that around 15,000 computers in the UK are affected by it.
Once GOZeuS is on your computer, it attempts to hunt out valuable data that it can steal. Names, addresses, bank details, passwords ... the usual stuff.
If it doesn't find enough information to be profitable, GOZeuS may activate CryptoLocker. This devious malware encrypts your computer, locking it down so you can't access any of your own data.
You may then see a message demanding you pay a ransom (typically £300 — £500) in order to regain access. Nice, eh?
Why do the next seven days matter?
Although GOZeuS and CryptoLocker are still out there, the network of infected computers has been significantly weakened. It's currently harder for infected computers to communicate with each other.
This means now is a really good time to strengthen your online security. To draw on a somewhat overused analogy, it's better to fix the roof while the sun's shining rather than waiting for the next storm.
According to official advice, the next week is the best time to make sure your defences are in order.
So, in the next few days, why not set aside an hour to review your security procedures?
- Scan your computer for GOZeuS. Free tools to do this are available from Symantec, F-Secure and other providers.
- Check your security software. Is it running on all computers and servers? Is it up to date?
- Do a full scan of your computer, too. Run a one-off deep scan using your current security software.
- Make sure your software is up-to-date. Visit Windows Update and turn on automatic updates.
Finally, you might receive an email or letter from your internet service provider warning your computer is infected. If so, don't dismiss it. As part of the work to disrupt GOZeuS, official bodies gained access to records on criminal servers and have been able to identify infected computers.
However, to be sure this isn't a fake phishing email, use the links above to go directly to GOZeuS removal tools, rather than clicking any links in the message. And call your ISP for confirmation if you have any concerns.
You can get more advice about GOZeuS on the Get Safe Online website.
Free IT policy templates now available

IT policies give your business shelter
Do you know what your staff are looking at online? Are you confident you're taking proper care of customer data? Is uncontrolled social media use rife in your company?
When you're running a business, sometimes keeping a grip on technology can feel like a losing battle.
Many business owners already suffer from too-much-to-do-too-little-time syndrome. Throw in tech-savvy employees running wild using their own tablets and software, and it's tempting to just let them get on with it.
Tempting, yes. Wise? No.
Policies to keep IT under control
No matter how much freedom you give your staff, it's important to retain some control over how technology is used in your business. Because when you have control, you can be confident.
You can be confident staff aren't wasting time. You can be confident you comply with data protection laws. And you can be confident you have a proper structure within which your business technology operates.
Your IT policies help establish this structure. They describe how technology should be used in your business, so your employees know what is and isn't allowed.
In short: they protect your company and your staff.
Get started with IT policies
Your IT policies don't need to run to hundreds of pages or contain complicated legalese. They just need to cover the essentials and be easily understood by your employees.
In fact, short and sweet beats long and detailed every time. IT policies should be documents your employees can read, understand and put into practice.
To help you create key IT policies for your business, we've created some free templates. Download them today and use them however you like in your company:
- Data protection policy
- Internet use policy
- Email use policy
- Social media policy
- Website privacy policy
You're welcome to just fill in the gaps, or copy the text to use as the basis for your own policies. Just keep in mind that every business is different, so it's best to get all your IT policies double-checked by a lawyer before you put them into place.
A friendly IT supplier might be willing to help too, especially if they already provide IT support for your company.
Four ways to fight back against cybercrime
 According to the government, cybercrime costs the UK economy around £27 billion each year.
According to the government, cybercrime costs the UK economy around £27 billion each year.
If your business suffers even a tiny fraction of that loss, it would be devastating. So, how so you make your company less of a target?
By fighting back against cybercrime. That’s how.
1. Use security software and keep it updated
Use decent security software on all your company computers and servers. If you’re in any doubt about what you need, ask your IT supplier.
Importantly, make sure your security software updates itself. This is the only way to stay safe from emerging threats.
Learn more about choosing security software >>
Do an IT security audit
A professional IT security audit is worth every penny. When an expert examines your IT setup, they’ll identify where you’re most vulnerable to attack.
Armed with this crucial information, you can create extra security measures and write a solid security policy.
Check hardware and physical security
IT security is not just about software. Any equipment that connects to the outside world (like your router) should be modern and made by a reputable manufacturer.
At the same time, check your premises for weak points. For example, if you keep your backup tapes in a safe, change the combination regularly. Consider installing CCTV too.
Beware of social engineering
Social engineering sounds creepy, but it refers to the way cybercriminals may try and con your people, rather than attacking your computers.
Make sure your employees look out for cold callers and unusual visitors. People who are good at social engineering tend to have the gift of the bag. It’s surprisingly easy to reveal a username or password to them.
Staff should also know how to handle ‘digital cold calls’, like phishing attempts.
Whatever you do, don’t neglect your people. One of the most effective precautions you can take is to make sure your staff know how to handle data safely and spot criminal behaviour.
- How to choose security and anti-virus software
- Case study: how we coped when our business was hacked
- Five common IT security mistakes
Ryan Farmer is a marketing manager at Acumin. Follow them on Twitter: @acumin.
Is responsive web design the future?
 With mobile devices still increasing in popularity, it’s never been more important for your website to cater for mobile users.
With mobile devices still increasing in popularity, it’s never been more important for your website to cater for mobile users.
As Ofcom said nearly three years ago, we are a ‘nation addicted to smartphones’. While sales of traditional PCs are gradually declining, smart phones and tablets are on the up.
If you’ve never done anything about your mobile presence, the time for action is now. There are many factors to consider.
Different devices have varying screen sizes, resolutions and processing power. There’s a choice of platforms, too — like iOS, Android and Windows.
It would be virtually impossible to create a different version of your website tailored to each individual device. However, you can use responsive web design instead.
What is responsive web design?
Responsive web design is a way of making sure your website provides a universally good experience for visitors, regardless of what device they use.
It’s the ‘one size fits all’ approach to web design. When you create a responsive website, the various elements (images, content, navigation and so on) shift and change with the screen size.
You’ll soon understand if you see a responsive website in action. Go and visit Time Magazine on your computer, then resize your web browser window. As the size of the window changes, the content moves around to fit.
This means responsive sites work well on both large monitors and tiny smart phones.
The benefits of responsive web design
So, responsive web design sounds good. But is there evidence to say it’s worth investing time and money in?
Many companies that have moved to a responsive web design have experienced growth in conversion rates, creating a sales uplift from mobile traffic. We are yet to see the full impact mobile devices will have on online behavior. However, they’re certainly here to stay.
This means it’s vital to consider taking a responsive approach with any new or redesigned websites.
Some businesses have a much higher proportion of mobile visitors than others. But as mobile devices become even more common, you really should think about the responsive web.
- How responsive web design can net you more customers
- Many of the UK’s top retailers lack responsive sites
- What we can all learn from Microsoft’s homepage
Blog by Adrian Case of Akita Systems, providing IT support and consultancy to the South East of England since 1996.
Watch out for that free Wi-Fi
 Free Wi-Fi seems like one of the great perks of the 21st century. In pubs and cafes in towns and cities across the UK, you can get online for nowt.
Free Wi-Fi seems like one of the great perks of the 21st century. In pubs and cafes in towns and cities across the UK, you can get online for nowt.
But now Europol — the EU’s law enforcement agency — is warning that using free Wi-Fi could be much riskier than we’ve realised.
In short, each time you connect to a public network, you could be playing a kind of Russian roulette with the data you send over the airwaves.
The rogue Wi-Fi network problem
Cybercriminals and hackers have spotted that we’re hooked on the convenience of free Wi-Fi. What’s more, they know most of us are accustomed to connecting without giving a thought to security. And they’re taking advantage.
A typical attack is for a hacker to set up a rogue network. They give it the same name and password (if applicable) as a legitimate network nearby.
For instance, a criminal might set up ‘John’s Café Wi-Fi’ near to John’s Café. When an unsuspecting punter connects, the attacker can intercept all the data that gets sent and received.
Sensitive files and information sent by email, personal data entered into website forms … it’s all there for them to harvest and use.
This isn’t a particularly clever or novel trick. But it works. Next time you’re connecting to a network in a public place, can you be sure it is what you think it is?
How to stay safe from Wi-Fi attacks
It can be difficult to be 100% sure that you’re safe when you use public Wi-Fi. And so the best way to protect your data is to not send or receive sensitive or private data while using it.
That’s easier said than done. One of the most popular uses for Wi-Fi is catching up on email, which can contain all kinds of data that’s valuable to hackers.
However, it’s definitely a good idea to think twice before entering your online banking details or other sensitive login details.
Being on a secure website (indicated by https:// and a padlock in your web browser) does offer some protection, but hackers can still use a technique called sslstrip to intercept your data if they really want.
The safest option is to connect via a virtual private network (VPN), which creates a secure tunnel through which your data passes. You can purchase VPN access from companies like Hotspot Shield — there’s a good explanation and some reviews of VPNs over on the PC Advisor website.
What you need to know about the Heartbleed security issue
 If you missed the news last week, experts have discovered a flaw in popular encryption software OpenSSL.
If you missed the news last week, experts have discovered a flaw in popular encryption software OpenSSL.
This is a big deal because OpenSSL protects hundreds of thousands of websites, including big names like Google, YouTube, Tumblr and Yahoo.
The issue is called Heartbleed. Although OpenSSL is meant to protect data transferred between a website and person using it, Heartbleed may allow hackers to access that data.
Time to panic?
Heartbleed is a high-profile story because so many websites use OpenSSL. But there's been a lot of confusion over what we should do about it.
Some websites have advised you to change all your passwords. Others have suggested that's counterproductive until every website has been fixed. So, we've investigated what businesses need to be concerned about.
First off, let's get one thing clear: Heartbleed is a real issue. You should definitely spend a few minutes thinking about how it might affect your business.
There are two aspects you need to be aware of:
- If you run a website that uses encryption (like an online shop) you should check to see if it's affected by Heartbleed.
- You should also consider whether any websites you use have been compromised.
Check if you're affected
Does your website use a secure connection (where a padlock appears in the browser)? If so, it's vital you check which encryption technology it uses.
If you're not used to getting into the nuts and bolts of your website, speak to your web developer or to the company that supplies your SSL service (usually your web hosting firm).
You can also pop your website address into this Heartbleed checker, which will let you know if your site is affected.
If you get the all-clear, that's great — you don't need to worry. But if your site does have the Heartbleed vulnerability, you should get it fixed — pronto.
This means updating to the latest version of OpenSSL, which doesn't suffer from Heartbleed. Your web hosting company or web developer should be able to do this for you.
In the meantime, consider deactivating the secure parts of your website. Better safe than sorry, after all.
Check the websites you use
Experts reckon around 500,000 websites are affected by Heartbleed. There's a good chance some of them are services you use regularly.
Changing passwords is the way to go here. But you need to make sure the problem is fixed before you change a password on a particular website. Otherwise, you risk exposing your new password too.
Most major websites will have fixed their systems by now. Again, you can use the Heartbleed checker to make sure.
As a precaution, we'd advise changing all the passwords on sites you use regularly — but only when you're sure those sites are secure.
Remember, it's safest to use a separate password for each website and to make sure all passwords are nice and strong.
Watch your accounts carefully
There's one last thing to bear in mind. Heartbleed was around for a long time before it was discovered. As a result, nobody's certain if any hackers exploited it before it became common knowledge.
In case your business or personal data has been affected, it's a good idea to check your online banking, email and other services you use regularly. If you notice anything out of the ordinary, do investigate.
Five steps to repair your reputation after a security breach
 Even if you take every precaution imaginable, it’s still possible for your business to fall victim to a security breach. And while nobody wants to be that victim, it’s worth giving some thought to how you’d manage your reputation in the wake of a cyber-attack.
Even if you take every precaution imaginable, it’s still possible for your business to fall victim to a security breach. And while nobody wants to be that victim, it’s worth giving some thought to how you’d manage your reputation in the wake of a cyber-attack.
We reveal the five steps every business should take to minimise damage and rebuild their reputation.
1. Take control and act fast
When US retail giant Target suffered a huge data breach last year, one of the biggest criticisms levelled at the company is that it didn’t do a good job of acting quickly and communicating well with customers.
Don’t make that mistake. Once you’ve taken the necessary precautions to secure your systems, share information with your customers, employees and partners.
2. Be open and honest
Being as honest as possible when communicating the crisis will ultimately reassure customers that you are doing everything you can to resolve the issue and protect their details.
Hiding the truth from loyal customers will only damage your credibility in the long run. When tech firm Buffer was hacked, the company remained open and communicative throughout.
3. Provide helpful customer support
Do your best to provide first class support to any customers affected by the issue. They probably aren’t IT experts, so you’ll need to assist and reassure them if you want them to remain with your business.
Be on hand to respond to customer queries and you’ll retain your reputation and customer relationships long after the breach.
4. Remember - one size doesn’t fit all
Think about who you’re talking to when you communicate what’s happened. Tailor your message to address the concerns of each group.
For instance, while customers will be concerned about whether their data has been compromised, investors and partners will require specific information on how your company’s reputation, value and long-term prospects could be affected.
5. Don’t be afraid to apologise
You’ll be surprised at how far an apology goes. While many businesses will be quick to blame a third party for their security weaknesses, more switched on companies understand that customers don’t want to hear excuses.
Take ownership of your problems and be clear and compassionate about what went wrong, how you plan to fix things and why you can be certain this won’t happen again.
- Three things you can learn from NatWest’s IT woes
- How to write a disaster recovery plan
- How we coped when our business was hacked
This post was written by Brittany Thorley, who regularly advises businesses about web security.
The five biggest hacks of 2014 (so far)
 We’re barely a quarter of the way through the year, yet many hacking stories have already hit the headlines.
We’re barely a quarter of the way through the year, yet many hacking stories have already hit the headlines.
Worryingly, many of them involve large, reputable companies and websites. And if they can’t stay safe from hacking attempts, what does that mean for smaller companies?
Here’s our round up of 2014’s five big hacks, so far. Oh, don’t forget to read our advice on keeping your business safe and coping during a security breach.
1. Kickstarter
Phenomenally successful crowdfunding website Kickstarter was the focus of a successful hacking attempt in February. The attackers didn’t manage to make off with any credit card information, but they did get hold of email addresses, passwords and phone numbers.
"We're incredibly sorry that this happened," chief executive Yancey Strickler commented. "We set a very high bar for how we serve our community, and this incident is frustrating and upsetting. We have since improved our security procedures and systems in numerous ways.”
2. University of Maryland
Just a week after the Kickstarter incident, the University of Maryland was targeted. Worryingly, hackers were able to access a whopping 309,079 personal records.
These included information such as dates of birth, university numbers and social security numbers.
The university’s president, Wallace D Loh, confirmed the institution had fallen victim to a sophisticated attack: “I am truly sorry. Computer and data security are a very high priority of our university.”
3. Edward Snowden
Having your email address stolen is bad enough. But would you want your passport — complete with embarrassing passport photo — stolen? Just ask whistle-blower Edward Snowden, who had a photo of his passport posted on online by a hacker.
Snowden may not be the only person affected by this attack. The perpetrator claims to have gained access to 60,000+ passports belonging to law enforcement and military officials signed up to the EC-Council’s Certified Hacker scheme.
4. Tesco
Valentine’s was as much for hackers as it was for lovers this year. Just before 14 February, 2,240 Tesco customers were the victims of a hack that revealed their phone numbers, email addresses and voucher balances. The unluckiest bunch also had their vouchers stolen.
Following the unexpected hack, Tesco contacted affected customers and issued replacement vouchers where necessary. Every little helps?
5. Twitter user @N
In what is almost certainly the most viral hack of the year so far, Naoki Hiroshima lost his Twitter username, @N, estimated to be worth around $50,000.
As only 26 people can have a one-letter Twitter handle, they are highly desirable. Naoki was the subject of an elaborate attack that saw the hacker go via websites such as PayPal and GoDaddy to access personal information.
According to Naoki, the hacker used PayPal to find out the last four digits of his credit card number. They were able to obtain other personal information from GoDaddy, before using these details to hijack the rare Twitter account.
The good news for Naoki is that — after some fuss — he eventually got his username back.
Andrew Mason is the co-founder and technical director at RandomStorm
Your five-minute guide to online backup
![]() Online backup services can be a really convenient way to take a safe copy of your company data and store it away from your main business location.
Online backup services can be a really convenient way to take a safe copy of your company data and store it away from your main business location.
This means that if anything goes wrong your data, you still have a backup copy to work from.
How does online business backup work?
Online backup services are generally simple and easy to use:
- Your important data is uploaded to the backup provider’s servers, over the internet.
- These servers are usually located in a data centre, keeping your files available and safe.
- Software on your computer or server automatically keeps track of changing data, backing it up automatically.
And that’s pretty much it. You change a file in the office and the backup copy gets updated for you. Delete a file by accident and you can get a copy back within minutes.
With some research showing that 48% of businesses experience data loss each year, online backup can be a really effective way to protect your company.
Why use online backup?
Businesses have traditionally backed their data up to tapes, hard drives or CDs. So, why use online backup instead of these tried-and-tested methods?
- You don’t have to mess around swapping tapes or disks, or remembering to keep them somewhere safe, off your premises.
- Online backup is largely automated. Although you still need to monitor and test your backups, online backup has fewer management overheads.
- Fewer capacity issues. Online backup services are flexible, so as your data grows you can just pay a little extra for more storage.
- No hardware to buy or replace. You never need to replace backup drives, tapes or disks when they wear out.
- Keep track of file versions. Most online backup systems let you recover copies of files that have changed several times.
- Even if your office burns down and your server is destroyed, you can access your data online — from anywhere in the world.
Online backup: what to look for
Not all online backup services are equally safe and effective, so it’s important to choose an online backup supplier that:
- Takes at least two copies of your information and stores them in two different, secure data centres.
- Charges you only for the service you need. You shouldn’t be paying for unnecessary storage space or add-ons.
- Checks your data regularly for inconsistencies, so you can be confident your backups will work if you need to access them.
- Offers disaster recovery services, to be sure you can get up and running again quickly if you do have a problem.
Are online backups right for your business
An online backup service could be a good fit for your business if:
- You want a cost-effective, future-proof backup solution.
- You need a flexible data backup and retrieval mechanism.
- You need a backup system that doesn’t require too much looking after
- You want file-versioning without having to juggle lots of backup tapes.
To learn more about backups, read about how to find the right backup methods, and see the five key questions to ask about your backup system.
This is a post from Danny Walker, director at IT Farm.
Eight easy ways to boost your web security
 There’s always more you can do to protect your business from security threats. But there’s never quite enough time to do everything.
There’s always more you can do to protect your business from security threats. But there’s never quite enough time to do everything.
So, here are eight easy ways to give your company security a bit of a boost.
1. Get the latest version of Windows
Unlike in the fashion industry, old tech rarely becomes cool again. You aren’t going to get any new customers because you run Windows 98.
Also, the latest operating systems have better security features, meaning you'll be better protected from web threats.
The same applies if you’re using Mac OS, or some other operating system. Stick with the latest version to be safest.
2. Bin Internet Explorer
Internet Explorer is so 2004 and people using it tend to get targeted because hackers know they’re not likely to be very web-savvy.
More advanced browsers like Firefox and Chrome have additional useful features, are generally safer to use and cost absolutely nothing. Which means there’s no reason not to switch.
3. Keep all your software updated
Constant update notifications from your software can be really annoying, but ignoring them could end up causing you more problems.
Virtual bugs are just like real life ones — they’re constantly evolving to find different ways to infect you. Updates contain new info on how to swat the bugs. Unless you install them, you won't see the benefit.
4. Improve your passwords
If your password for something is 'password' then you're in for a bad time of it. Hopefully your passwords aren't this terrible, but it's likely they could be improved.
For maximum security, use a random combination of upper and lowercase letters, numbers and symbols. You can use a service like LastPass to help you remember them.
5. Use two-factor authentication
It sounds technical, but all two-factor authentication means is that logging in requires you to prove your identity in two ways. Usually, you need a password you know and a reference code that’s sent to your mobile phone.
You can easily set up two-factor authentication on many websites and online services, including Twitter, Gmail, iTunes, Facebook, Microsoft accounts and LinkedIn.
6. Maintain restore points
We’ve all had one of those moments when your jaw drops, you stare blankly at the screen and think: ‘I've made a huge mistake.’ It’s at times like these that System Restore can be a lifesaver.
System Restore is a feature in Windows that allows you to roll your computer back to a previous point in time. The idea is that if something goes wrong, you can go back to the last ‘known good’ configuration.
Your computer will probably create restore points on its own, but you can do it yourself when you make major system changes, too.
7. Backup your data
Ok, here’s the worst case: your computer is so utterly cream-crackered that you need to wipe it and start again.
If you’ve been backing up your data regularly then the process of getting back to normal becomes much less painful.
External hard drives for backups are pretty cheap these days. You can also use online storage, such as that offered by Dropbox and Google.
8. Be a vigilant browser
To be honest, this point alone could make up a whole new tip sheet. But in a nutshell, try to stick to websites you trust.
Sites listed higher up in search results are more likely to be safe because more people have used them.
There are some dark and dingy corners of the internet. Try and avoid them.
- Do you need mobile security software?
- How to choose security and anti-virus software
- How we coped when our business was hacked
Nick Chowdrey is a finance and accounting writer for Crunch, an online accountancy firm for freelancers and small businesses.




