Posts for May 2014
Why the cloud is like a serviced office
 “If someone asks me what cloud computing is, I try not to get bogged down with definitions. I tell them that, simply put, cloud computing is a better way to run your business.”
“If someone asks me what cloud computing is, I try not to get bogged down with definitions. I tell them that, simply put, cloud computing is a better way to run your business.”
That’s the cloud, according to Marc Benioff, CEO and founder of cloud business platform Salesforce.com.
And while you could argue that he has a vested interest, he has a point. The cloud is so widespread that every business needs to understand what it is and how it can help deliver products and services people will actually pay for.
But there are many definitions of the cloud. If IT is not your main focus, the cloud can quickly turn into brain fog.
The cloud is like a serviced office
For a straightforward, alternative definition of the cloud, take a look at a serviced office like the one we work out of here at Desynit.
Other than a great view of the station and a fantastic local bakery, there are good reasons for us being here:
- When we moved in, we didn’t have to worry about sourcing basic office equipment. It was included.
- All the main services are managed for us: lighting, heating, internet, reception, cleaning and so on.
- Because we share with other businesses, we can access facilities like meeting rooms on a pay-as-you-go basis.
- The building is in good condition and well-maintained, with a proper alarm system, locks and security.
- As our business grows, it’s easy for us to find more suitable premises. (We’ve moved to a bigger office three times so far.)
On top of all that, there’s only one bill to pay each month. That makes life much easier for our finance team and helps us budget accurately.
The real benefits of the cloud
It doesn’t come for free, that’s for sure. But in terms of value to a business, it’s a clear win. So when Marc Benioff talks about businesses running better in the cloud, this is what he means.
Desynit Director, Matt Morris, explains: “You no longer need to think about the bricks and mortar issues of hardware, licensing, maintaining operating systems and installing updates — to name just a few. It’s all taken care of.
“If you need additional services, bolt them on. Need more capacity for peak time? It’s there on a pay-as-you-go basis.”
Oh and one more thing. This particular office is mobile. Wherever you are, as long as you have internet access, just step right in.
The final fittings and fixtures
Let’s come back to the serviced office analogy. The basic building set-up may tick most of the boxes, but what if you have a more unusual requirement?
Some cloud providers open up their platforms so third party vendors can develop apps and add-ons to meet business needs. (At Desynit, we integrate apps from the Salesforce AppExchange.)
When your requirements aren’t standard, being able to do this makes a big difference.
Choosing the right cloud platform will enable you to focus on your core service, rather than on your supporting systems. And that has to be better for your business.
- How the cloud changes your business IT
- Which cloud persona fits your business?
- Cloud computing: there’s nothing new under the sun
Amy Grenham is the marketing manager at Desynit, a business systems IT consultancy and Salesforce.com integration partner.
Infographic: how to run your business from a smart phone
You can do some pretty cool things with mobile devices these days. But if you only use your smart phone for email and calls, you're missing out on opportunities to be more efficient and productive.
This infographic from payments firm Payment Sense shows the current state of the mobile market and lists some useful apps you can try.
View the full infographic from Payment Sense.
Related information from IT Donut:
IT for Donuts: how to stay safe after the eBay breach
 IT for Donuts is a regular Friday feature where we explain a tech term or answer a question about business IT.
IT for Donuts is a regular Friday feature where we explain a tech term or answer a question about business IT.
In the wake of eBay's enormous security breach, this week we look at what you can do to protect yourself and your business.
The eBay security breach
On Wednesday, ecommerce giant eBay revealed it has suffered a security breach of gigantic proportions.
Cyberattackers compromised the company's user database and accessed key customer details. These include names, post and email addresses, encrypted passwords and dates of birth.
This information could be used to carry out identity theft, access users' other online accounts — and generally wreak havoc.
So, if you're an eBay customer, what should you do? And what precautions can keep you safe from similar attacks in future?
1. Change your passwords
For starters, change your eBay password. And as hackers know that people often use the same password for lots of different websites, change those too.
2. Use strong passwords
Strong passwords are hard to guess, because they use a combination of letters, symbols and numbers.
See how to create strong passwords >
3. Stop using the same password everywhere
Many of us use the same passwords for lots of different sites, even when we know it's a bad idea. So stop.
Using different passwords helps you contain problems, because hackers can't run wild through your online accounts.
Having said that, keeping track of multiple passwords is a pain, so you might also want to...
4. Start using a password app
These tools generate unique, strong passwords for each website. They then remember these passwords and insert them when you need them.
The obvious issue with using a password app is it means saving or storing your passwords somewhere. However, with high-profile security breaches regularly hitting the news, nowadays using a password app feels safer than not using one.
We like LastPass and 1Password.
5. Watch out for phishing emails
Now the eBay breach is public knowledge, other online criminals will try to take advantage with fake emails.
These phishing emails may purport to be from eBay and invite you to click a link to change your password. But if you do so, you'll really be providing those details to another hacker.
You can read our advice on phishing, but the safest thing is to visit eBay.co.uk, reset your password there and then ignore any future emails.
6. Think about what information you provide
Often, websites ask for a vast amount of information just to get you signed up. Think twice before providing your date of birth, mother's maiden name or other particularly sensitive details. Does the website really need that information?
If the site is subsequently hacked, you could pay the price.
7. Make things up
One way to avoid handing over sensitive data is to make stuff up. After all, why should a clothing retailer know your real date of birth?
If you enter fake information, hackers won't be able to use it to break into your bank accounts or steal your identity.
(If you do decide to enter fictitious details when registering for websites, you may need to remember them to pass that site's security checks in future. Entering false information may also be against a website's rules.)
Are they doing enough?
Following the advice here will help keep you from being affected by the eBay security breach. It'll also give you better control over your personal data in future.
However, is it time we started asking harder questions of the firms to which we entrust these details? Given the regularity with which security breaches occur, should these businesses be investing more time and money to protect us?
Previous IT for Donuts security tips
- How to wipe your computers for disposal
- What is a firewall?
- How out of office messages can be a security threat
Image copyright: Katherine Welles
IT for Donuts: three iPad gestures you might not know
 IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week, discover three new ways to control your iPad through gestures.
The power of gestures
When you’re using an iPad (or any other touch screen device, for that matter), a gesture is just a fancy name for a movement you can make on the screen to control the device.
For instance, if you use an iPad, you’ll be familiar with swiping a finger to move between the different pages of your home screen.
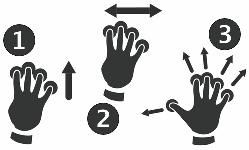
You might find these three gestures particularly helpful when moving between apps or back to your home screen. The numbers correspond to the diagrams above.
1. Swipe up with four fingers
No matter what app you’re using, touching your iPad’s screen with four fingers and then sliding them up will show all the apps you have open.
They’ll appear in view which scrolls left and right. Swipe with a finger to move through them. To close an app, swipe up.
2. Swipe left or right with four fingers
This is a super-fast way to jump from one app to another. Instead of hitting the home button and then tapping the app you want, swipe left with four fingers.
Your iPad will jump to the app you were using previously. Swipe left again to go back another app. To get back to where you started, just swipe right.
3. Spread your fingers and thumb
Once you’ve learnt this gesture, you’ll never need to use your iPad’s home button again.
To jump back to your iPad home screen, just touch the screen with the four fingers and thumb of your hand. Then spread them out. Your home screen will appear.
Which gestures do you use most on your iPad? Do you find the touchscreen more natural than using a keyboard and mouse?
Three quick tips for mobile security
![]() Our tablets and smart phones go with us nearly everywhere — even to places many of us would prefer they didn’t (I’m looking at you, toilet-texters).
Our tablets and smart phones go with us nearly everywhere — even to places many of us would prefer they didn’t (I’m looking at you, toilet-texters).
But although we treat mobile devices like extra limbs, I don’t know of any arms or legs that contain sensitive information about our identities, banking habits and current location.
Mobile threats range from app-based malware to adware and even ‘chargeware’ that costs you money without you realising it.
And, of course, there’s the age-old problem of leaving your phone in the pub after one too many pints.
Standard mobile security is pretty abysmal. So, what can you do to stay secure?
1. Know your permissions
When you open a new app on your smart phone, it may ask permission access other information or functions, like your contacts or location.
Don’t grant permissions without reading what the app is asking for. Instead, take time to get to know your permissions, then make educated decisions about what permissions you’re willing to grant.
A location-based application — like one that maps your runs — obviously needs to know your location. But does a drawing app?
Always ask yourself whether a permission request ties up with what the app is meant to do.
You can also check out the app’s reviews to decide whether to trust its creator. If they seem technologically adept, that’s a sign your data will be in good hands (or ones that aren’t malicious).
2. Don’t hack your device
Many smart phones come with restrictions put in place by your mobile service provider. For instance, you might only be able to install apps from an approved app store.
These restrictions can seem limiting, making it tempting to find ways to bypass them. But believe it or not, often those restrictions are in place for a reason.
They may relate to security holes or other vulnerabilities. You could expose these if you hack into your phone.
If you want to experiment, it’s better to do so on an old device. Keep your regular phone — and data — safe.
3. Reign in Wi-Fi and Bluetooth
If you’re not using Wi-Fi and Bluetooth, turn them off.
Keeping Wi-Fi on constantly can mean your phone connects to hotspots as you go, rather than using a secure mobile data connection.
That’s fine when you’re at work and you know the network. But it’s less secure when you’re using ‘Steve’s super-legit hotspot’ while you wait at a bus stop.
This isn’t an imagined threat. Recent research suggests rogue Wi-Fi networks are very much on the increase.
Even if Steve isn’t looking to steal your financial info, you have no way of knowing who else has access to his network.
The same goes for Bluetooth. Either turn it off when you’re not using it, or make sure the default settings don’t let other users connect to your device without permission.
For more information, read this mobile security guide guide from security experts Lookout.
Guest blog from Rosie Scott. Rosie is a content strategist at a digital marketing agency and avid blogger. You can find her at The New Craft Society www.thenewcraftsociety.com> or on twitter @RosieScott22.
IT for Donuts: write emails people can understand
 IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week, we reveal a quick way to check and improve your emails before you send them.
The plague of email
Long, badly-written emails are a plague on productivity. They can leave the recipients confused and unsure of what — if anything — they need to do in response.
If you find yourself writing an involved message, it’s a good idea to run it through Hemingway before pressing send.
Hemingway is a free online tool that gives your writing a readability grade. It also flags up complex sentences and highlights words that might be unclear.
I recently blogged about how I use it when I’m writing for websites like IT Donut. But you can use it to write emails, too.
How to use Hemingway
Using Hemingway is easy. Just write your email as normal, using Outlook, Gmail or whatever you normally use.
Once you’ve finished, click and drag with the mouse to highlight the text in your email. Then copy the text using CTRL+C (or CMD+V, if you have a Mac).
Then go to the Hemingway website. Click in the middle column, which will contain some introductory text about Hemingway. Delete this text, then use CTRL+V (or CMD+V) to paste in your email content.
Hemingway will give your text a readability score, shown in the top right of the window. Aim to get this below 10.
Editing your email
Hemingway will highlight your text where it identifies areas for improvement. Work through these one-by-one.
Often you can see suggested edits by running your mouse over the highlighted text. Good ways to make your text more readable include:
- Splitting long sentences into two or more separate sentences.
- Putting short, simple words in place of complicated ones.
- Using accurate, descriptive words that leave little room for doubt.
You can edit your text within Hemingway, then paste it into your email software once you’re happy.
Just remember: although Hemingway is a good way to sense-check a message, it’s not foolproof. Language is complicated, and often you’ll want to overrule its suggestions.
Previous tips:
Six web browser plugins that are (virtually) essential
![]() A few carefully-chosen web browser plugins can make all the difference to how you use the internet. You’ll work faster and feel smarter when you're online.
A few carefully-chosen web browser plugins can make all the difference to how you use the internet. You’ll work faster and feel smarter when you're online.
So, what is a browser plugin and which ones should you choose?
What is a web browser plugin?
A web browser plugin is a piece of software that adds extra functions to your web browser. Plugins are also called add-ons or extensions.
Most are created by to add a feature that isn’t available with a web browser as standard.
Plugins are available for all major web browsers and most are free. You can search plugins online for Google Chrome, Microsoft Internet Explorer, Firefox and Apple’s Safari.
If you’ve not explored web browser plugins before, you’ll probably be surprised at the range available to you. Here are six of our favourites:
1. Nimbus
Nimbus lets you take a snapshot of the website you’re viewing and save it to your computer as an image. It’s useful in all kinds of situations and is more versatile than most of its competitors.
You can grab the entire page or select a portion of it, then add annotations before saving, printing or sending it straight to your Google Drive.
Download for: Firefox and Chrome.
2. LastPass
LastPass is a free password manager that keeps track of all your complicated, hard-to-remember website passwords. If you tend to use the same password for different accounts or currently write your passwords down, LastPass is a good way to be more secure and make your life easier.
Once you’ve installed the plugin, it’ll remember passwords as you use different websites. LastPass is generally more secure than the password tools built in to browsers. And it has handy extra features, like a built-in password generator.
Download for: all major browsers.
3. Pocket
In a world full of distractions, Pocket will help you avoid going off-task to read an article or blog post. It puts an extra button in your web browser. If you’re on an interesting page, press the button and it’s saved for you to read later.
You can then sign in to your Pocket account at a convenient time to review and read everything you’ve saved. There’s a mobile app, too, so you can catch up on your reading on the train or bus (or in bed).
Download for: all major browsers.
4. Adblock Plus
Ok, so here’s the thing. Online advertising keeps most of the internet free. So if you care about your favourite websites staying in business, you might think that blocking online ads isn’t really fair.
However, if you feel some online ads are too intrusive and underhand, Adblock Plus is the solution. Install it to enjoy an ad-free internet experience. (You can configure it to only block particularly obtrusive ads, if you like.)
Download for: all major browsers.
5. Check My Links
This one is a must if you run or manage a website. It scans all links on a given page to make sure they’re working properly. You’ll see broken links highlighted in red. It’s a handy way to QA your site.
Check My Links identifies links that aren’t working, of course. But if you’re getting into detailed SEO work, it also shows you when links are being redirected or messed with in other ways that Google might not like.
Download for: Google Chrome.
6. Lazarus 3
Have you ever spent time completing an online form, only for a crash to destroy your efforts? Lazarus 3 saves forms as you type. If anything interrupts you — like a power cut or a website failure — your work is safe.
Lazarus 3 works with virtually every online form. If you need to reconstruct your data, you just go back to the form and select the special Lazarus icon that appears.
Download for: all major browsers.
Is technology damaging your health (and your business)?

This could be affecting your health.
Leading scientists warned today that we've become 'supremely arrogant' by failing to pay attention to our body clocks.
And guess what? Technology is part of the problem. The light from smart phones, tablets and computers tends to be in the part of the spectrum that disrupts the body clock.
Using these devices in the evening can delay the release of sleep-promoting hormones. That means you feel sleepy later and wake up feeling tired as a result.
Get more sleep, be more healthy
It would be easy to dismiss this as some Daily Mail-esque scare, except that reduced sleep has been convincingly linked to all kinds of health problems. Not getting adequate sleep could be a contributory factor in cancer, heart disease, obesity and other ailments.
There are less-serious consequences too, but these can be more disruptive to everyday life. For instance, who isn't less alert and more grumpy after a poor night's sleep?
If you find you're prone to making rash decisions or snapping at colleagues, is it because you were up late last night on your iPad?
The health risks of running a business
Many business owners work long days and answer emails at all hours. As a result, it's not hard to argue they might be particularly susceptible to tech-related sleep issues.
And even if it feels like you're getting things done by working long hours, you might be doing more harm than good. Some tech pundits argue that sleep deprivation leads to muddled thinking and poor decisions.
Throw in stress — which can also disrupt sleep — and you start to see how the working patterns you choose when running your company might affect both your future prosperity and your health.
Perhaps it's time we started turning technology off in the evenings.
IT for Donuts: scan documents without a scanner

IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week, we reveal that you don’t need an expensive document scanner to create digital copies of documents. If you have a smart phone made in the last couple of years, its camera should be more than up to the job.
Use your phone as a scanner
While dedicated scanners are fast and produce high-quality images, your smart phone’s camera provides a quick way to create passable digital versions of documents, receipts, business cards and more.
The most obvious way to scan a document with your smart phone is to open the standard camera function, point it at a document and press the take photo button.
Once you’ve taken a photo, you can check the quality by zooming in to make sure the text isn’t blurred.
You might need to experiment with the flash or other settings to get the best-quality image. However, if you’re after a copy of a receipt or need to send a key page to a colleague, this will do the job.
You can use your phone’s email function to send the scan to yourself or someone else, or connect it to cloud storage like Dropbox to save scans elsewhere.
With this approach, it’s best to make sure your phone’s camera is set to its highest-quality, so scanned documents stay legible.
Get a dedicated scanning app
If you plan to use your phone as a scanner regularly — or just want to take a slightly more efficient approach to your scanning — there are a number of scanning apps available.
These are good because they make sure your camera is set for the best-quality scans. Some apps can also convert scanned text into editable documents, which is great if you need to work on them in future.
You can try these apps:
- CamScanner converts scans into proper text and lets you add annotations to share with colleagues or contacts.
- Genius Scan includes tools to enhance the images you create, can export to PDF and connects to cloud storage services.
- Google Drive has a scanning function built in. It also converts documents to PDF format and saves them in your Google Account.
If you have a lot of scanning to do, you’ll want to invest in a proper scanner instead of using your smart phone. But for occasional use, the convenience of a smart phone trumps the quality of a scanner, every time.
Previous IT tips:
Is technology still blue?
 It seems that the jury is still out over women and technology. Despite some business fairs showing promising signs of women becoming increasingly visible, this week’s Times ran a piece by Antonia Senior entitled 'Sisters must programme it for themselves' bemoaning the continuing lack of women in the industry.
It seems that the jury is still out over women and technology. Despite some business fairs showing promising signs of women becoming increasingly visible, this week’s Times ran a piece by Antonia Senior entitled 'Sisters must programme it for themselves' bemoaning the continuing lack of women in the industry.
But is it fair to divide IT into the traditional geek territory of programming, still largely a male preserve, and the web designers, IT users and digital content creators who use the technology? And does the divide matter? Microsoft and Apple made billionaires of their creators, but a lot of development work is now a backroom job, while there are big bucks to be made in business by knowing which tools to use.
A self-taught career?
Chris Hall, whiz Drupal developer, is of the view that it’s not formal education that’s a barrier to women, or anyone else for that matter, in IT. As he says, ‘many people in successful IT careers have no formal qualifications at all, many have learned everything that supports their career via the very same devices and infrastructure they use in their daily work.’ Which makes me wonder if the supposed glass ceiling is more of a red herring.
The Dell-sponsored fifth annual Women’s Entrepreneur Network has a note of its own on women and technology claiming that ‘women especially understand that it’s not the technology itself that is important, but what connections, solutions and changes it enables you to make’.
Gender divide
Either way, should we be worried if one career attracts more men than women? Looking at why it happens, and making sure that the way we educate and raise our children gives them properly equal opportunities, aspirations and self-worth, is crucial. But maybe valuing both parts of the equation, and paying accordingly, is a bigger deal.
So why is our Marketing Donut pink and IT Donut blue? Well, as I write, our (male) CEO is wearing a pink shirt and our (female) head of web and digital systems a striking blue. Maybe once we stop thinking about jobs for the boys or girls we can just get on with building the careers we want.
Further reading:
Free IT policy templates now available

IT policies give your business shelter
Do you know what your staff are looking at online? Are you confident you're taking proper care of customer data? Is uncontrolled social media use rife in your company?
When you're running a business, sometimes keeping a grip on technology can feel like a losing battle.
Many business owners already suffer from too-much-to-do-too-little-time syndrome. Throw in tech-savvy employees running wild using their own tablets and software, and it's tempting to just let them get on with it.
Tempting, yes. Wise? No.
Policies to keep IT under control
No matter how much freedom you give your staff, it's important to retain some control over how technology is used in your business. Because when you have control, you can be confident.
You can be confident staff aren't wasting time. You can be confident you comply with data protection laws. And you can be confident you have a proper structure within which your business technology operates.
Your IT policies help establish this structure. They describe how technology should be used in your business, so your employees know what is and isn't allowed.
In short: they protect your company and your staff.
Get started with IT policies
Your IT policies don't need to run to hundreds of pages or contain complicated legalese. They just need to cover the essentials and be easily understood by your employees.
In fact, short and sweet beats long and detailed every time. IT policies should be documents your employees can read, understand and put into practice.
To help you create key IT policies for your business, we've created some free templates. Download them today and use them however you like in your company:
- Data protection policy
- Internet use policy
- Email use policy
- Social media policy
- Website privacy policy
You're welcome to just fill in the gaps, or copy the text to use as the basis for your own policies. Just keep in mind that every business is different, so it's best to get all your IT policies double-checked by a lawyer before you put them into place.
A friendly IT supplier might be willing to help too, especially if they already provide IT support for your company.
IT for Donuts: how to wipe your computers for disposal
IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week, see how to safely wipe sensitive data from your computer before you get rid of it.
Don't just delete data
Before you dispose of an old computer or server, it's vital to erase every trace of your data. Just ask the NHS, which was fined after computers containing patient data turned up on eBay in 2012.
Simply deleting the files isn't enough, because it's usually possible to reconstruct data from the imprint it leaves behind.
To get rid of data so it can't possibly be retrieved, you have three main options:
- Smash up your computer's hard drive. While this will do the job, disk drives can contain dangerous materials and pose a safety risk, so it's not recommended.
- Get a computer disposal company to do it. Make sure you pick a company with a good track record, so you can be confident the data is erased.
- Use a data wiping tool yourself. This is fairly straightforward and will give you confidence that data really has been wiped. Read on to learn how to do it.
Get a data scrubber
To remove data securely, you need to use data scrubbing software. This writes meaningless data over your files several times, until the original data can't be recovered.
If you just want to completely wipe your computer, there are a number of data scrubbers that will do the job. We like Darik's Boot and Nuke (DBAN). It should work with virtually all laptop and desktop PCs, as long as they have a CD drive.
Before you start
Before you erase your computer, there are a few things to bear in mind:
- Following the instructions on this page will erase everything from your computer, irretrievably. Back up anything you want to keep.
- Once you've run DBAN, you will need to reinstall your operating system if you want to keep using the computer. This takes time and can be fiddly.
- The process of erasing everything can take a while. Depending on the size of your disk drive(s), it can be anything from a couple of hours to a couple of days.
How to use DBAN
To follow these instructions, you'll need a blank CD and a computer running Windows 7 or 8. This can be a different computer to the one you're erasing.
- Download the DBAN software, but don't try to run the file (it won't work).
- Put a blank CD into your CD drive.
- Right-click the file you've downloaded and select Burn disc image.
- Wait while your computer copies the DBAN software to the CD.
- If the computer on which you created the CD is not the one you want to erase, put the CD into the computer you do want to erase.
- Turn on or restart the computer you want to erase.
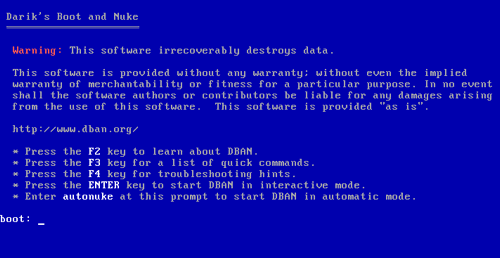
- After a moment, the DBAN software should load. If you see your normal operating system, you need to find out how to make your computer boot from a CD. The instructions for this vary, so you may need to search online.
- Once you see the blue DBAN screen (see image above), pause for a moment. Are you ready to erase everything on this computer? Have you backed up all the data you need?
- If so, type autonuke and hit the Enter key.
- DBAN will begin scrubbing all disks in your computer. This can take anything from a few hours to over a day, so if you have a laptop, make sure it's plugged in!
Once DBAN has finished wiping your hard drive(s), you'll see a message to say DBAN succeeded. That's it — you can now dispose of the computer safely.
Scrubbing selected files
If you don't want to go as far as scrubbing your entire computer, you can use the free Eraser package to scrub selected files from a Windows PC. This is an excellent way to dispose of files securely while retaining a functioning computer.
More information about deleting data:
Why 3D printers are useless for business
 3D printers are coming, and they’re going to change the world. Shops will soon be printing products to order. Garages will print parts for your car on the spot. And instead of cooking dinner, you’ll just print it out.
3D printers are coming, and they’re going to change the world. Shops will soon be printing products to order. Garages will print parts for your car on the spot. And instead of cooking dinner, you’ll just print it out.
Well, one day all those things might be true. But right now, 3D printers are nothing more than novelty items. They’re ok at printing plastic trinkets and ornaments, but not so good at creating practical items.
Printing a plastic mess
We’ve been as guilty as anyone of hyping 3D printers as the next big thing. And yes, there’s potential. The problem is that the technology — especially the affordable 3D printers you can buy today — is way off achieving that potential.
While forward-looking articles talk excitedly about printing bicycles, houses and even human organs, people who actually own 3D printers seem to have mixed results, to say the least.
You only need to take a look at the art of 3D print failure, a Flickr group containing hundreds of photos of 3D printing gone wrong.
Some of the warped plastic shapes are impressive. But they demonstrate that the technology — at least at the affordable end of the market — is more for hobbyists than businesses.
The drawbacks of 3D printers
3D printers available today don’t just suffer from questionable reliability. They also tend to be slow. It can take hours to print relatively simple objects.
What’s more, the raw plastic is expensive. You’ll also need to know how to use relatively complex software in order to design the objects you’re going to print.
So, if tempted to pick up a 3D printer for your business, keep your expectations realistic. You won’t be buying a tool that’s going to revolutionise your company or make your life easier.
You’ll basically be buying a toy. 3D printers are indisputably fun to play with and have a curiosity value to them. But they’re not serious business tools. Not yet, at least.




