Blog posts tagged IT security
How do hackers hack? Common, sneaky attacks
 If you pay attention to the headlines, it seems like hackers are hacking more than ever. Large companies like Apple and US giant Home Depot have fallen victim to security breaches of one kind or another.
If you pay attention to the headlines, it seems like hackers are hacking more than ever. Large companies like Apple and US giant Home Depot have fallen victim to security breaches of one kind or another.
Information relating to tens of millions of people has been compromised. But, how do hackers hack? What techniques do they use to infiltrate business networks and gather valuable data?
In this ongoing cyber conflict, it’s important to know your enemy. Read on to find out what strategies hackers use when they hack.
How hackers hack #1: intercepted passwords
Using strong passwords is certainly a smart idea, but in some cases it’s not enough. Although strong passwords are hard for hackers to guess, many will simply try to obtain the password through illegal means.
This usually involves breaching the security measures of a website or company, thereby gaining access to a list of user passwords. This recent password hack is a great example.
You can protect your business by using unique passwords for each individual account and changing them every few months. You should also protect your systems from hacking attempts by using up-to-date security software.
How hackers hack #2: fake wireless networks
If you ever go to a café, pub or airport, you might be tempted to connect to the free wireless network available there.
Free Wi-Fi is one of modern life’s conveniences. But be careful, because it can also be a prime target for hackers. They can set up fake wireless networks with legitimate-sounding names.
Once you’ve connected, hackers can steal your personal information and any unprotected data that you send over the network.
Be cautious when connecting to public Wi-Fi. Only use networks that require a password to connect and check the network name with the establishment you’re in.
Even then, don’t assume you’re safe. Consider connecting through a VPN to protect all the data you send across the wireless network.
How hackers hack #3: phishing
Ah, the old fake email scams. Hackers try all kinds of approaches to snare victims via fake emails.
You can often spot them through telltale inconsistencies or spelling and grammar errors. In any case, never give sensitive information out through emails, especially if you’re unsure of the source. Be wary of phishing attacks through social media too.
In 2012 alone, social media phishers were able to steal more than a billion dollars from small businesses. Spear phishing, where hackers target specific individuals, is also on the up.
Learn how to stay safe from fake emails >
How hackers hack #4: cookie hijacking
Cookies are small pieces of data that websites place on your computer. They’re used to provide certain functions online (like remembering when you’ve logged in to a website, or what’s in your shopping cart).
Some hackers hack using a technique called ‘cookie hijacking’. Basically, they steal the cookies on your computer, then use them to pretend to be you when they visit a website.
Because cookies are often used to remember when you’ve logged in to a website, cookie hijacking lets a hacker pretend to be you without knowing your username or password.
Using good security software is a good precaution against cooking hijacking. There’s also a lot websites can – and should – do to make their users less vulnerable.
If you’re particularly worried, you can regularly erase cookies from your computer. However, this may cause your preferences on websites to vanish, so it can be inconvenient.
These four techniques are by no means the only way that hackers hack. But they’re some of the most common and sneaky.
This is a post from Rick Delgado, a freelance writer and tech commentator.
Do your ex-employees keep logging in?
 When an employee leaves your businesses, are you letting them walk out with access to valuable company data?
When an employee leaves your businesses, are you letting them walk out with access to valuable company data?
According to the 2014 Intermedia SMB Rogue Access Study, 89% of employees who leave a company retain access to business or cloud applications like Salesforce, PayPal, email and SharePoint.
That’s a scary figure. We’ve written a lot about IT security lately, but statistics like this make us think that this level of coverage is warranted.
When a member of staff leaves your business, you must have a way to revoke their access to all your resources. Failure to do so just invites disaster.
Ex-employees are actually signing in
Of those people questioned for the research, 49% had actually signed in to an ex-employer’s account, despite having left the company.
Most of these people probably act out of curiosity, rather than malice. But they still have access to apps that may contain important company data.
A minority will almost certainly be intending to do harm to their former employers. It only takes one person to cause you all sorts of problems.
You could be looking at hefty reputational damage, a loss of competitive advantage — or even a big fine from the Information Commissioner.
Security begins at work
“Most small businesses think ‘IT security’ applies only to big businesses battling foreign hackers,” says Michael Gold, president of Intermedia.
“This report should shock smaller businesses into realising that they need to protect their leads databases, financial information and social reputation from human error as well as from malicious activity.”
You can start by putting some proper procedures in place to control and revoke access when employees leave your company. These are some good starter tips:
- Record who has access to what. You can’t be sure you’ve revoked everything unless you know what each employee can access. If you rely on apps with separate usernames and passwords, it’s particularly important to keep an up-to-date list of who has access to what.
- Don’t share usernames and passwords. Some cloud services charge extra for each user, so it’s tempting to have one generic username and give everyone access. Bad idea: every employee who leaves will know the username and password.
- Have an ‘offboarding’ process. You probably have a standard procedure for when people join your company. But do you have a similar set of steps to follow when someone leaves? If not, it might be an idea to put a checklist together.
It can be trickier than you might expect to get a handle on who has access to what in your business. However, once you do so, you can be more confident of retaining control over your most important data.
Simple protection from cyber criminals
 Last week’s celebrity hacking news showed just how easy it can be for hackers to gain access to sensitive or personal data.
Last week’s celebrity hacking news showed just how easy it can be for hackers to gain access to sensitive or personal data.
And you don’t need to be a well-known personality to be targeted by hackers. Many hackers target small businesses, because these companies are less likely to have invested in strong security measures.
Someone hacking or compromising your system could be your worst nightmare. But there are some simple ways to prevent it from happening. Here are some steps you can take to make your system safer.
1. Add another layer of verification
Two-step verification is a good way to add another layer of protection when staff log in to company systems.
Typically, two-step verification requires your staff to sign in with something they know (a password), plus something they have (often a one-time code that’s texted to their mobile phone or shown on a digital key fob, pictured).
Two-step verification provides significant extra protection, especially if your company uses its systems to store and share sensitive documents.
2. Use strong passwords
Most people know they need to use strong passwords. But most people still don’t do it.
Make it company policy to use strong passwords. Mixing uppercase letters, lowercase letters, numbers and symbols makes it much harder for someone to gain unauthorised access.
You can use password management tools — like 1Password or LastPass — to keep track of these hard-to-remember logins.
3. Don’t share your logins
Sharing usernames and passwords is a big no-no. If everyone uses the same details to sign in to your shared workspace, if something goes wrong then you don’t have an audit trail to a specific user.
It also creates potential risk when an employee leaves the business. They probably won’t do anything malicious, but are you willing to take that risk?
4. Encrypt important data
Encryption scrambles data so it can’t be read, even if a hacker gets their hands on it.
Windows 7 and Windows 8 both have encryption tools built in. There are plenty of other encryption tools available too —many are free.
Copyright © 2014 Ian Cowley, managing director at Cartridge Save.
Business questions from the celebrity iCloud hack
 |
|
Copyright: s_bukley |
You can’t have missed last week’s news that hackers gained access to intimate photos belonging to celebrities, including Jennifer Lawrence (pictured).
The story has raised important questions about what data individuals store in the cloud. Many of those questions have implications for businesses too.
After all, cloud services play a pivotal role in many companies. They’re used for all kinds of tasks, from backing up data and sharing files to enabling remote working and reducing the need for expensive in-house equipment.
The cloud certainly has significant advantages, and it’s here to stay. There’s a strong argument that overall, the security risks of using the cloud are lower than storing data in your own business.
But with cloud technology still developing, could this breach be the spark that forces cloud providers and their users to confront some key questions?
1. What’s your weakest link?
Although full details of the iCloud breach have yet to emerge, it seems likely the celebrities were victims of some kind of brute force or social engineering scam.
This means hackers used techniques to work out log in details, rather than exploiting a technical breach.
With cloud security, much of the focus is on measures systems like firewalls and backups. However, if all that stands between a hacker and your data is an easy-to-guess password (like ‘password’, ‘123456’, or your company name), that’s how criminals are most likely to access your data.
Our advice:
Strong passwords are important, and you should really combine them with two-factor authentication to up the security on your cloud accounts.
The biggest problem with strong passwords is that they’re a nightmare to remember. We recommend using password management software, like 1Password or LastPass.
2. Do you understand your cloud service?
An interesting piece from Wired argues that we’ll all benefit if some of the affected celebrities try to sue Apple over this case.
I won’t go into all the arguments, but one key point is we often start using cloud services without completely understanding what we’re getting into.
For example, Apple’s iCloud terms of service are over 8,000 words long. When you sign up, you agree to them, almost certainly without having read them.
As we use these services to store and share sensitive information, perhaps providers should make more of an effort to really communicate what they do to protect our data, and what we need to do, too.
Our advice:
If you don’t understand what a cloud service is going to do with your data, do further research before signing up. A local IT supplier might be able to help.
Don’t commit everything to begin with, either. Start by moving non-critical data to the cloud. You can shift more of your business across as you gain confidence.
3. Who can you talk to?
If you’re an A-lister, you can guarantee you’ll get attention when your cloud services get hacked.
But if you’re an ordinary business just trying to get on with work, are you confident you’ll get a response from your provider when something goes wrong?
Services like Apple’s iCloud and Google Apps are designed to be automated. You can sign up and start using them without having to speak to anyone.
Most of the time, they work flawlessly. But if something goes wrong and you can’t figure it out yourself, it can be hard to find someone to help with the problem.
Our advice:
Look for cloud providers that offer comprehensive support and have a good reputation. Search online for reviews and make sure they’re well established.
Often, a local IT supplier can help you find the most appropriate cloud services as well as providing support and help when you need it.
Blog by John McGarvey, editor of the IT Donut.
IT for Donuts: how to stay safe after the eBay breach
 IT for Donuts is a regular Friday feature where we explain a tech term or answer a question about business IT.
IT for Donuts is a regular Friday feature where we explain a tech term or answer a question about business IT.
In the wake of eBay's enormous security breach, this week we look at what you can do to protect yourself and your business.
The eBay security breach
On Wednesday, ecommerce giant eBay revealed it has suffered a security breach of gigantic proportions.
Cyberattackers compromised the company's user database and accessed key customer details. These include names, post and email addresses, encrypted passwords and dates of birth.
This information could be used to carry out identity theft, access users' other online accounts — and generally wreak havoc.
So, if you're an eBay customer, what should you do? And what precautions can keep you safe from similar attacks in future?
1. Change your passwords
For starters, change your eBay password. And as hackers know that people often use the same password for lots of different websites, change those too.
2. Use strong passwords
Strong passwords are hard to guess, because they use a combination of letters, symbols and numbers.
See how to create strong passwords >
3. Stop using the same password everywhere
Many of us use the same passwords for lots of different sites, even when we know it's a bad idea. So stop.
Using different passwords helps you contain problems, because hackers can't run wild through your online accounts.
Having said that, keeping track of multiple passwords is a pain, so you might also want to...
4. Start using a password app
These tools generate unique, strong passwords for each website. They then remember these passwords and insert them when you need them.
The obvious issue with using a password app is it means saving or storing your passwords somewhere. However, with high-profile security breaches regularly hitting the news, nowadays using a password app feels safer than not using one.
We like LastPass and 1Password.
5. Watch out for phishing emails
Now the eBay breach is public knowledge, other online criminals will try to take advantage with fake emails.
These phishing emails may purport to be from eBay and invite you to click a link to change your password. But if you do so, you'll really be providing those details to another hacker.
You can read our advice on phishing, but the safest thing is to visit eBay.co.uk, reset your password there and then ignore any future emails.
6. Think about what information you provide
Often, websites ask for a vast amount of information just to get you signed up. Think twice before providing your date of birth, mother's maiden name or other particularly sensitive details. Does the website really need that information?
If the site is subsequently hacked, you could pay the price.
7. Make things up
One way to avoid handing over sensitive data is to make stuff up. After all, why should a clothing retailer know your real date of birth?
If you enter fake information, hackers won't be able to use it to break into your bank accounts or steal your identity.
(If you do decide to enter fictitious details when registering for websites, you may need to remember them to pass that site's security checks in future. Entering false information may also be against a website's rules.)
Are they doing enough?
Following the advice here will help keep you from being affected by the eBay security breach. It'll also give you better control over your personal data in future.
However, is it time we started asking harder questions of the firms to which we entrust these details? Given the regularity with which security breaches occur, should these businesses be investing more time and money to protect us?
Previous IT for Donuts security tips
- How to wipe your computers for disposal
- What is a firewall?
- How out of office messages can be a security threat
Image copyright: Katherine Welles
Will wearable tech be big in 2014?
 I met a bloke wearing Google Glass a couple of weeks ago. The opportunity for conversation was brief, as I was on the down escalator in a tube station, but I managed to ask how he was finding it.
I met a bloke wearing Google Glass a couple of weeks ago. The opportunity for conversation was brief, as I was on the down escalator in a tube station, but I managed to ask how he was finding it.
“It’s switched off at the moment,” was his initial response, “but it’s really useful when it’s turned on.” He then veered off towards his platform, so I didn’t get the chance to ask him to expand on this insightful evaluation of Google’s headline-grabbing smart glasses.
It’s becoming normal
The encounter got me thinking though: a year ago, if I’d seen someone wearing glasses that can understand speech, give directions and record video, I would have been astounded. But 12 months later my reaction was simply mild surprise.
It just goes to show how quickly things change. It made me wonder what wearable technology holds for us in 2014 — and what opportunities this emerging sector will bring for business.
Wearable tech is on the way
Wearable technology is about much more than Google Glass. While these smart glasses have caused controversy and excitement, other wearable tech already available includes:
- Fitbit, a wireless tracking device that measures how active you are and encourages you to do more exercise.
- Jawbone UP, a similar device that tracks how you sleep, exercise and eat.
- Samsung’s Galaxy Gear, a ‘smart watch’ that lets you make phone calls and send texts.
But that’s just the tip of the iceberg. Gadgets proposed or under development include clothing that connects to your Facebook account, a ring that acts as your bus pass and a nappy that monitors the health of your baby.
Wearable tech and your business
Quite simply, we’re going to see a wave of wearable devices hit the market in 2014. Some will succeed. Many won’t.
But it seems obvious that wearable technology will bring advantages and opportunities for businesses. For instance, it’s not hard to see how something like Google Glass could be useful in a warehouse or factory environment.
Some firms will be keen to develop wearable tech themselves. Others will rush to release apps that work with gadgets produced by other companies.
It’s early days, but if you’re interested in learning more about wearable technology then you could do worse than head to the Olympia Conference Centre in London next March. That’s when the UK’s first wearable technology show will take place — and a great chance for you to see what’s coming in this new sector.
- ‘Ok Glass, let’s revitalised the High Street’
- Are we using technology, or is it using us?
- What’s next after tablet computers?
Image of Google Glass via Flickr user Ted Eytan, under Creative Commons.
Watch out for spear phishing
 Every day, it seems there’s a new online scam ready to catch up the unwary. Recently it was cyber-criminals posing as a dating agency on LinkedIn in order to harvest data from unsuspecting users of the professonal networking site.
Every day, it seems there’s a new online scam ready to catch up the unwary. Recently it was cyber-criminals posing as a dating agency on LinkedIn in order to harvest data from unsuspecting users of the professonal networking site.
This was a so-called ‘spear phishing’ attack, where online criminals target specific people rather than sending out messages at random. Top corporations and media outlets are increasingly becoming victims of these scams — but that doesn’t mean smaller companies aren’t at risk too.
Spear phishing is an example of social engineering, which sees online scammers manipulate people into sharing sensitive information about themselves or others.
It’s easy to fall victim and there’s no shame in it. These criminals are good at what they do, using flattery, confidence tricks and deception to get the information they want.
Social networks and email are two of the most common routes through which scammers will try and contact you or people in your business. To help you stay safe, here are five ways to avoid falling victim to a spear phishing attack:
- Always use your common sense. The most important thing to remember is not to automatically trust any email. Don’t let the presence of familiar personal information in a message lull you into a false sense of security.
- Post minimal personal information on social media. Yes, it’s tempting to tell everyone when it’s your birthday on Twitter, or that your son is called Oli, but it’s really better not to reveal information like birthdays, anniversaries or the names and ages of your children. You can always use single letters or initials in place of full names, if you have to tweet about little Johnny’s every move.
- If an email requests immediate action, do a little research. Scammers will try and stop you thinking for too long by creating a sense of urgency — like requesting you reply immediately to secure a special offer. Google the company name and get a contact number to ensure the email is valid.
- Be careful with emails that relate to current events. For example, emails about the royal baby or the scandal of the moment could well contain links to malicious web sites. Back in 2012, photos of Emma Watson could have been a threat to your company.
- Don’t assume emails from people you know are safe. Cyber criminals can collect a colleague’s email address from social networks or the internet and send email to you that looks like it is from them.
The bottom line is that vigilance is key to staying safe from a spear phishing attack.
It may seem like an inconvenience to do extra research when you receive a message you’re unsure about, but in the end it’s worth the time to know who you’re dealing with.
- Three ways to stay safe from the phisher-men
- Avoid this IT support telephone scam
- Three ways to avoid online scams
This post is from Espion, a firm specialising in IT security.
How to organise your email archive
 Companies are creating and keeping more data than ever — and some businesses are getting excited about what they can use all this ‘big data’ for.
Companies are creating and keeping more data than ever — and some businesses are getting excited about what they can use all this ‘big data’ for.
Yet the reality for many companies is that the data explosion actually equals data frustration. For all but the most disturbingly-organised individuals, essential documents are hard to locate. Files get saved in the wrong folder — and email is often the most-disorganised data of all.
Organising 12,000 emails a year
If you work in a typical office, there’s a good chance you use Microsoft Outlook to send and receive email. If you receive 50 emails a day, that’s over 12,000 emails hitting your inbox in a year.
If you decide to archive them all (after all, who knows when you might need a particular email in the future?) then finding a specific email soon becomes hard work.
In this sort of situation, the only option is to undertake an email search. And then wait. With email folders — especially the sent folder — extending into the tens or hundreds of thousands of emails, the standard Outlook search process is inadequate.
Outlook search is broken
In addition to being incredibly slow, the way Outlook works makes it difficult to find any email if you can’t remember the entire recipient list — which is hardly helpful.
It’s not uncommon for it to take over 15 minutes to find an email. Sometimes you’ll fail completely and give the whole thing up as a bad job. What a ridiculous waste of what should be highly productive time.
The problem is that even if you have a proper email archive system in place, most of these solutions are about storage, not retrieval.
Yet in a world of exploding data, effective information retrieval is an essential business tool. Most email users would bite your hand off for fast, guaranteed access to email, like a Google-style keyword search that rapidly locates the right information.
Email archive + keyword search
By combining an archive of every email sent and received with keyword search, you get a faster way to locate messages and documents that have been misfiled.
With the right approach, there is no need for big data to constrain your productivity. You can keep all your emails and find the one you’re looking for, when you need it — enabling you to be more productive.
Blog by Andrew Millington of Exclaimer
Are security fears holding you back?
 Here’s some good news for you: more businesses are taking IT and security risks seriously.
Here’s some good news for you: more businesses are taking IT and security risks seriously.
Security is no longer a topic that’s relegated to IT departments or individual staff members. A survey of UK organisations by risk management specialists NTT Com Security found that 56% of respondents discuss security and risk either routinely or frequently at board level.
The IT fear factor
However, as businesses become more aware of potential security risks, it seems a fear factor may be kicking in. The same survey found that concerns over information security and risk have stopped a project or business idea progressing in nearly half (49%) of organisations surveyed.
So, how do you monitor and manage the risks your company faces, without becoming paralysed? After all, if you paid attention to every online horror story then you’d probably shut up shop and find a nice, non-internet business to run, instead.
Get to grips with your security
There’s a strong argument to say that companies with the best handle on their security are the ones that see it as an opportunity.
Being proactive, identifying and managing risks and taking steps early can actually give you an advantage in the market. For instance, clients and customers like it when they know they can trust you to keep them safe.
But proactive security isn’t something many businesses do well. Only 1 in 5 organisations surveyed said they base their security spending on risks they’ve actually assessed.
The rest, presumably, take a range of basic security precautions and then react to other problems as they occur.
Proactive security is best
Neal Lillywhite, SVP Northern Europe at NTT, says that although businesses are aware they should take a proactive approach to managing risks, most don’t yet put this into practice:
“While the majority see a benefit to having a proactive approach when assessing the risk of information assets, the fact that still only a fifth base their spending on assessed risk shows there is plenty of room for improvement.”
If your business is one of the 4 in 5 that doesn’t do a good job of assessing the risks it faces, it’s probably time to start. And as there’s no time like the present, why not find out how to perform an IT security risk assessment right now?
Who's been reading your email?
 Think your email is safe and private? Think again. Most emails sent over the internet travel in plain, unencrypted form. That means anyone who knows where to look could theoretically intercept and read your most private missives.
Think your email is safe and private? Think again. Most emails sent over the internet travel in plain, unencrypted form. That means anyone who knows where to look could theoretically intercept and read your most private missives.
So, who could be reading your email?
Google, for a start
Google has revealed that it does scan the emails that pass through its Google Mail service. The tech giant has has stated this in submissions aiming to dismiss a class action lawsuit that accuses it of breaking wiretap laws.
Its position regarding the reading of our emails goes like this:
"Just as a sender of a letter to a business colleague cannot be surprised that the recipient's assistant opens the letter, people who use web-based email today cannot be surprised if their communications are processed by the recipient's ECS (electronic communications service) provider in the course of delivery."
This analogy fails to acknowledge the fact that when an assistant opens their boss’s mail they do so with agreed or implicit prior consent and they are subject to confidentiality agreements.
I have always maintained that writing to someone via email is akin to sending a postcard. The content of the email, just like a postcard, can be read en-route.
Securing your email
Securing your email is easy: you just need to encrypt it. This scrambles every message you send so it can't be understood by people other than the intended recipient.
These days you don't need detailed technical knowledge to use email encryption. Many companies offer email encryption products that handle the technical side of things for you. However, the key is to find one that doesn’t require your recipient to have installed software to decrypt your message and then send you an encrypted reply.
You might also want to find a service run by a UK company and hosted on servers in the EU. This means that UK and EU privacy law will apply — you don't risk getting caught up in the US Patriot Act, which many argue is a good reason to avoid US-based services.
My company offers an email encryption service called Egress Switch.
How to get started
You'll need to decide whether you want a pay as you go encryption service, or something more substantial.
It's also worth looking for a scalable service. You might start out as someone who will use encryption infrequently, for the odd highly-sensitive email. But over time you may decide you want to use encrypted email for all of your business communications.
In the end, though, it’s up to you: if you don’t mind risking Big Brother reading your email then you can do nothing. But if you'd prefer your private messages to stay that way, it's a good idea to adopt email encryption.
- Why you need to archive your email
- Send sensitive information in a self-destructing message
- How to prevent data breaches
Blog provided by Paul Simms of Reflect Digital on behalf of Egress Software Technologies.
Get an IT security healthcheck
 We cover IT security a lot on this blog, because it’s a really important subject and there’s a lot to say about it.
We cover IT security a lot on this blog, because it’s a really important subject and there’s a lot to say about it.
Unfortunately, that means it’s difficult to stay on top of current security threats, like knowing whether you should be more worried about hackers or viruses this week.
If you feel like you haven’t given any thought to data and IT security lately, we’ve found a security healthcheck tool that you might find useful.
Created by AVG, a company that makes security software, it asks you a number of questions before scoring your security overall and providing specific advice in each area.
It’s not a magic solution to keeping your data safe. IT security is different for every business, so you still need to learn more about the dangers you may face and speak to your IT supplier to make sure you’ve taken sufficient precautions.
However, this tool will get you thinking about the things that matter when it comes to IT security. And the advice at the end should give you some good starting points for improvements.
Just bear in mind that this advice is purely from a security perspective.
For instance, while the tool may advise you to upgrade to the latest version of Windows (and that might be the most secure option), there are other considerations too, like whether your existing software will keep working ok.
We also have lots of other information to help you secure your business IT systems. These are some good places to start:
The toilets and photocopiers that are out to get you

These days, tech dangers can even lurk in the bathroom
Last week news broke of two unexpected yet chilling security dangers, involving rogue photocopiers and high-tech toilets. (Yes, we are well into silly season - can you tell?)
For starters, it turns out your Japanese-style toilet could be vulnerable to attacks from hackers.
An unexpected shower?
Yes, loos from the Land of the Rising Sun have now reached a point where they they have built-in Bluetooth so they can be controlled by your smart phone.
By downloading the free app, you can control the shower and flush functions of a £4,000 toilet made by Japanese firm Lixil. (You can also keep a 'toilet diary' using the app, but we won't go into that.)
But where there's connectivity, there's potential for hackers - no matter whether we're talking about an expensive toilet or an expensive computer.
Problems arise in this case because all models of the super toilet use the same Bluetooth PIN of 0000. This means anyone within Bluetooth range can download the app, connect to your toilet, tap in the PIN and then play havoc with its functions.
No news on whether anyone has actually suffered a toilet attack yet, but with the story occupying top spot on the BBC's 'most shared' list last week, it's surely only a matter of time.
The photocopier that changes your figures
Hot on the heels of these terror toilets came news of the Xerox machine that's been overstepping its authority.
Now, back in the day, photocopiers copied what you told them to. You might have had the occasional paper jam or toner accident, but by and large you got an accurate copy.
Not any more. A bug in several Xerox models means they may alter numbers on the documents they copy. Computer scientist David Kriesel found that his was changing the figures on building plans and other documents.
The problem has been narrowed down to an issue with the compression software used by the machines, and raises all sorts of questions about who would be liable if you sent out an inaccurate photocopy to a client.
Really. Who ever heard of a photocopier making its own edits?
Too clever for its own good?
While there's certainly an element of humour to both these stories, they carry a serious message too.
Everything we own is becoming more connected. In time your fridge, your door locks, your car, your light switches and more could all be on the internet.
There will be benefits to this, but there will certainly be risks as well. A hackable toilet is only the thin end of the wedge, and nobody knows quite how thick it's going to be.
What's more, as machines get smarter in how they do things, they seem to get better at screwing things up too.
In a world where even a simple photocopier can make a hash of copying a document, it's dangerous to assume something is right just because the computer says so.
29% of people don't do backups. Are you one of them?
 We have almost total reliance on our computer systems, databases and critical files. We face frequent security threats.
We have almost total reliance on our computer systems, databases and critical files. We face frequent security threats.
Survey after survey demonstrates how our computers and data are at risk from crime, accidental damage, loss or component failure.
All this, and yet research shows that almost a third of computer owners (29%) have never backed up their computers. Only around 10% of people back up daily - yet that's what you need to do if your data changes frequently.
With a Google study (admittedly a few years old) telling us a two-year-old hard disk has an 8% chance of failing in the next year, many of us are taking needless risks with our data.
Backups aren't hard
These days, running backups doesn't even need to be all that tricky. An increasing number of smaller companies are turning to online backup as a simple and relatively affordable solution.
Online backup means your key files are sent over the internet to a remote server, where they're stored safely. Ragnar Percy-Bell works for Plexus Business Solutions, an IT support company in Kent. He reckons online backup is a convenient way to safeguard your data.
"Your computer and database files are encrypted so that they are totally secure," he explains. "They are sent via your normal internet connection to a secure computer file storage system off-site."
|
At least two backups
However, if the first rule of backups is to do them daily, the second is to never, ever rely on a single backup method. Although online backups may be convenient, you should always use a second backup method too. You just can't be too careful with your essential data.
If you're using online backup, your second backup system is likely to be an in-house system. It might be an old fashioned tape system, or simply a set of external hard drives that you copy your data too.
"You can use a remote backup system for daily critical files and databases and your existing tape or drive system for a full backup once a month," suggests Ragnar. "Your tapes and drive will last longer, plus you can feel totally sure that your business critical files will not be lost."
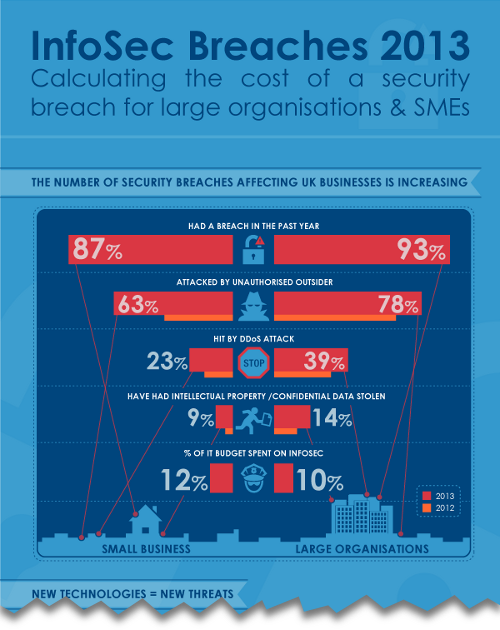
Infographic: the £65,000 security breach
We seem to have covered IT security and data protection on this blog a lot recently. And there's good reason for that: suffering a data breach can cost your business a lot of time and a lot of money.
How much? Well, in the worst case it could cost smaller companies up to £65,000 to recover, according to this infographic based on research from the Department for Business, Innovation and Skills.
Interestingly, it's lost custom and business disruption that make up the majority of that loss. Businesses will tend to spend relatively little on actually responding to an incident, although if you have to bring in external suppliers or consultants to evaluate the damage and set things right then that can add up.
Here's the infographic, so you can see the cost of security breaches for yourself. Click it to view the full version:
Infographic by Via Resource. See full-size version.
Five myths about hackers (and why they matter to your business)

Most hackers look absolutely nothing like this
Security breaches and hacking attempts seem to be in the news all the time. And the stories tend to focus on the organisations that have been hacked, rather than dwelling on who's doing the hacking.
Perhaps as a result, there are lots of myths and misconceptions about hackers. Read on and we'll explode five of the most common.
Myth one: hackers don't target small businesses
IT dealsSee the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
Just because the newspapers only report when big companies get hacked doesn't mean that smaller firms are safe.
In fact, there's evidence to suggest hackers are increasingly targeting small firms, which may hold valuable data - like customer details or intellectual property - but don't have big resources to invest in security precautions.
For instance, one poor newsstand owner ended up around £14,000 out of pocket after his cash registers were hacked to send customers' credit card details to Russia.
Myth two: hackers are kids
Are some hackers kids just out to cause mischief and gain kudos online? Sure.
But don't make the mistake of thinking that the stereotype holds true for everyone who might try and break into your computer systems.
These days, hacking is big business. There's a big black market for stolen information like credit card details. Hackers are coordinated, organised and professional about what they do, because they can make money doing it.
Myth three: hackers use cutting edge techniques
Hackers don't steal information by sitting at their desk working out how to break through your firewalls, work out your encryption and read your data. Well, most of them don't.
These days they're more likely to put their efforts into creating a convincing phishing website to steal your log in details.
Why? Because it's easier and it works.
Myth four: hackers only target Microsoft Windows
Don't assume that because you use an Apple Mac, you're safe from hacking attempts.
While it's true that Microsoft Windows attracts most attention from hackers, that doesn't mean they aren't also finding ways to break into other platforms and devices.
In fact, with data spread across smart phones, tablets, laptops, desktops, CDs, portable hard drives and in the cloud, you could argue there are more targets than ever for hackers.
Myth five: you can only stop hackers with security software
Yes, you can block hacking attempts with a strong firewall, and fend off many threats with good security software from a company like McAfee or Symnatec.
But don't let good security software lull you into a false sense of security.
Hackers have long realised it's people who are the weakest links in any line of defence. We're all susceptible to social engineering, which is why hackers use flattery, confidence tricks and outright lies to trick you into revealing sensitive information or granting access to key systems.
There are some good examples of social engineering here.
Five tactics to prevent data breaches

Are your data protection tactics right?
For businesses of any size, ensuring the accuracy, integrity and security of data is essential.
Under the Data Protection Act (1998), data controllers are required to take 'appropriate technical and organisational measures' to protect personal data from unauthorised or unlawful access or use, as well as preventing accidental or malicious loss or damage.
The principles of the act cover how data is stored, accessed and transferred to protect the subjects of that data, be they your customers, suppliers or employees.
Data breaches can affect anyone
Data breaches can affect businesses of any size and may have serious consequences. For instance, in January 2013, electronics giant Sony was fined £250,000 after millions of PlayStation Network customers’ data was stolen.
The implications of a data breach for smaller firms can be considerable, which is why ensuring protection is in place when handling data is a key priority for any business that uses information technology.
Here are five key data protection measures that can be taken by your business:
IT dealsSee the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
1. Define a clear IT policy
Implementing a clear IT policy is one of the most effective ways to ensure the integrity of your data. Use permissions to ensure employees can only access the information that is relevant to them and make sure they use secure passwords.
Passwords should also be changed regularly in order to minimise breaches.
2. Watch contractors and third parties
Negligence by contractors is one of the most common reasons organisations suffer data breaches in the UK.
Establish a written contract which ensures any contractors and other third parties adhere to data protection principles and best practice.
3. Secure email attachments and documents
It's important you understand when it's appropriate to use email to transport data.
Email attachments which include sensitive or confidential data should always be encrypted and password protected. The password for any documents should be communicated verbally (in person or via telephone) to ensure the data can only be accessed by the relevant parties.
4. Invest in antivirus protection
You should invest in appropriate virus protection and security software to maintain the integrity of your IT systems and prevent hacking.
This will not only help protect your data from theft, but also keep your technology safe from corruption and other problems.
Use a firewall to control access to the data you hold and implement secure remote access if you need employees to access data when away from the office.
5. Know how to handle a breach
Even if you take every possible precaution, it's still possible for a security breach to occur.
If this happens to you, make sure you have procedures in place to help you deal with the situation.
You may also wish to take out professional indemnity insurance, which can protect your business from customer disputes arising from loss of their data or documents.
Michael Howard writes on behalf of Markel UK, a specialist online insurer providing cover for professionals, professional practices and consultants.
Protect your business from a cyber attack
 There are an estimated 4.8 million small and medium-sized enterprises (SMEs) in the UK, many with their own ecommerce websites.
There are an estimated 4.8 million small and medium-sized enterprises (SMEs) in the UK, many with their own ecommerce websites.
In 2011, 32 million people purchased goods or services online. That gives the UK one of the world's biggest internet-based economies. And it's why keeping your website safe and secure from cyber-attacks has never been more important.
SMEs are easy targets
As a business owner, you’re probably dealing with plenty of critical day-to-day issues. Perhaps worrying about your website’s security is not top of your list of priorities.
You may be wondering why hackers would want to target a small business rather than big brands like Lush and Adidas. The simple answer is that hackers know smaller businesses have fewer resources dedicated to online security, making them easier targets.
For those involved, cyber crime is big business. It costs the global economy $338bn a year which, according to Symantec, is significantly higher than the global narcotics black market.
Since the beginning of 2010, 36% of all targeted cyber-attacks have been directed at SMEs.
With around 44 million attacks a year taking place against home computers, businesses and government systems in the UK, an offline website means a loss of income. For instance, PayPal reportedly lost £3.5m due to a cyber-attack in 2010.
As well as lost revenue, a website security breach can result in losing vital data, your reputation and even your ranking on Google. Ultimately, it could damage your business beyond repair.
Six simple tips to protect your site
Here are six simple but effective tips to protect your business against cyber attacks:
- Choose your passwords carefully. Password123 is not a secure password! Make sure passwords have at least eight characters and use a combination of letters and numbers. Here are some ideas for creating strong passwords.
- Install anti-malware and anti-virus protection for your website in the same way you would your PC. Reviews can help you determine if the product is right for your business.
- Use SSL to encrypt data. SSL provides a secure connection, protecting data sent between a customer’s web browser and your server. Your hosting provider can help set this up for you. Learn more about SSL.
- Avoid using wireless networks. If you must use them, make sure you're using the latest encryption standard, WPA2. This offers government-grade security.
- Keep programs and hardware up to date. This helps block malware that thrives in older equipment and out of date software. If you are using Windows or a Mac you can set up weekly update checks. You should also do this for any software you use to manage your website.
- Educate employees about the latest online threats. This way they’ll know clicking on bad links or opening dodgy attachments can compromise data. All your staff should be as vigilant at work as they are at home. If in doubt, don’t click it.
So, if website security wasn’t on your priority list, it might be time to add it now.
Guest post by Rahul Mistry, content writer for www.heartinternet.co.uk. You can follow Rahul on Twitter and Google Plus.
People don't trust businesses with personal data (but hand it over anyway)
 One in four consumers don't trust any company to secure their personal information online. That's according to a survey of 1,000 UK consumers conducted by information security and risk management firm Integralis.
One in four consumers don't trust any company to secure their personal information online. That's according to a survey of 1,000 UK consumers conducted by information security and risk management firm Integralis.
Although a quarter of all respondents said they don't trust any organisation to take care of their personal data online, there is some relatively good news in one sector: nearly 65% of people said they do trust banks with this information.
However, businesses operating in other fields need to do more to win the trust of their customers. Only 36% of people trust online retailers with their personal data, 24% trust supermarkets and just 22% trust online payment systems like PayPal.
No trust, no problem
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
But despite this general lack of confidence, people still use these services in droves. For instance, over half of people surveyed said they do grocery shopping online at least once a week. While people might not trust online retailers with their data, they're still willing to share it.
"Online shopping is unbelievably popular, even though people don't necessarily trust it," confirms Mick Ebsworth, information security consulting practice director at Integralis. "People are worried about the types of information these site sask for."
"Far too often, consumers are prepared to supply core personal details - like mother's maiden name or date of birth - to organisations that don't need that information."
This can put consumers at increased risk of ID theft, should that information fall into the hands of online criminals.
"People need to always think about the information they provide," explains Ebsworth. "Does an organisation need it? Your bank might not be attacked, but your account at another site with lower security might be. So why use the same passwords?"
Don't ask if you don't need it
Although consumers might be making mistakes by supplying personal information to firms that don't need it, the buck really stops with the organisations requesting it. If they want potential customers to trust them more, they need to be more circumspect about requesting information.
Ebsworth has some advice for online businesses: "Firstly, you need to put in place the technical controls to keep personal information secure. You need the right level of encryption and good levels of data storage. Think about who has access to that information - in your organisation, with third parties, and online."
"Secondly, only request information that you really need. Recognise that the consumer has a role to play here, but that you can help them."
Finally, he has a sober reminder for firms that might still be unconcerned about how they handle this data. "Everybody who collects personal information has a duty to take care of it. Although there's nothing in the law to say how you should deal with a data breach, the Information Commissioner's Office can levy big fines if they believe you haven't adhered to good practice."
Does your business need all the information it collects from customers? Do they trust you to take care of it?
Don't panic, but 23% of your staff are stealing from you

If dodgy employees all looked like this, they'd be easy to spot.
A staggering one in ten employees has stolen important data from their employer after handing in their notice, reveals a new study from IT security specialist LogRhythm.
It seems that downloading a company's customer database onto a USB stick or copying crucial documents to CD is much more common than you might have thought. Of the 2,000 employees studied, the survey found that a massive 23% had taken confidential data from their workplace.
Often, people steal client details or product information in the hope that it'll give them a head start with their new employer. But 14% of people who admitted taking data did so to help set up their own rival company. And 23% did it out of revenge, because they felt undervalued and poorly treated.
Employers know the problems
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
Clearly, anyone stealing data from their employer is in the wrong. But that doesn't mean businesses should make it easy for employees to get their hands on the good stuff.
This research also surveyed employers, 47% of whom said they don't have any system in place to stop staff accessing confidential information or taking data.
So, all-too-often it's lax security and a lack of concern that makes it easy for staff to walk away with crucial company assets.
Worse, 60% of employers said they never change passwords or access codes, which is a little like leaving the door wide open for former employees to come and grab what they like.
You wouldn't let a staff member keep their keys to the office after they've left, so why would you let their passwords keep working?
Are you at risk?
If this survey is at all representative, there's a good chance your business is at risk of data theft. So, what are you going to do about it?
- Restrict data access. Sensitive data like customer information should only be available to employees who absolutely need it. It should never be sent by email or stored in shared locations.
- Close user accounts promptly. If a member of staff has been sacked, close their network account immediately and revoke all their access rights.
- Don't share passwords. Shared passwords are the enemy of good security. Not only can people continue to use the password once they've left, but it's also much harder to tell who's been accessing the data.
- Rotate access codes regularly. If you have a PIN-entry system for your building or a wireless network with a password, make sure you have a system to change them regularly - probably every month.
Finally, there's an aspect to this that leaves a nasty taste in the mouth. The research found 53% of people who've stolen data use it to get a head start in their next job, or to impress their new boss.
If the new employer decides to make use of that data, what sort of message does that send? And do they really think that employee isn't going to do the same to them when the time comes?
In short: if you've ever benefited from a data theft, don't be surprised if you end up suffering sometime too.
Can you spot the phishing website?
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
You've probably heard of phishing. It's where scammers send you an email that looks like it's from an official organisation, usually your bank.
The email usually contains links to a fake log in page which collects your username, password and other security details. If you enter them, the scammers will subsequently use your credit card, empty your bank account or commit some other crime against you.
Some phishing websites are laughably bad, with terrible grammar, bad spellng and shonky design. But others can be very convincing.
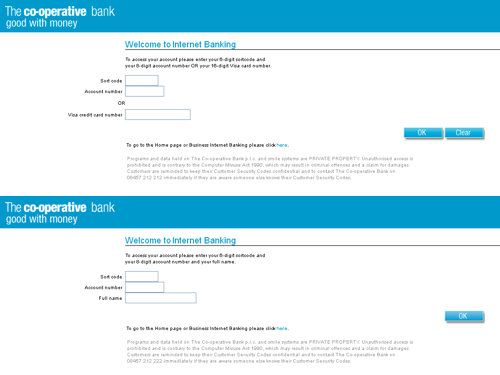
Spot the phishing site
To show you just how convincing phishing sites can be, here are two screenshots for you. One is the genuine sign in screen for the Co-operative Bank's online banking service. The other is a fake sign in screen from a phishing email I received.
You can click the image to see both screens full size. Can you tell which is which?
So, how did you do?
Well, the top screenshot is of the genuine sign in screen. The second one is the fake.
If you're familiar with this bank's online interface, you'll probably realise that the site asking for your full name is not genuine. But if you don't use your online banking often or simply aren't paying 100% attention when you click the link, it's easy to see how you could be fooled.
Three principles to avoid phishing
Checking the address of a site like this is usually the most foolproof way to see if it's fake. In this case, it was easy to tell, because the URL clearly wasn't the Co-operative's normal address:
![]()
It isn't always as obvious as this through, so here are three foolproof ways to avoid phishing traps:
- Don't click sensitive links in emails. If an email from a trusted source like your bank asks you to log in to your account, do so by manually typing in the website address rather than clicking a link.
- Pay attention to security notices. Most phishing emails will be caught by email filters, security software or web filtering tools. If you see a warning about an email, link or website, don't ignore it. (It's amazing how many people do.)
- Let the sender know your concerns. If you're in any doubt at all about whether an email or website is genuine, get in touch with the organisation it claims to represent. A quick phone call should be enough to confirm your doubts.
And as a final warning, don't ever enter sensitive log in information if you have any concerns at all about the website you're on. Even if it just looks or feels a bit funny, that's reason enough to stop and think before you make a mistake.
Note: don't click links in dodgy emails like we did. They can be dangerous, even if you don't enter in any sensitive information.
Did we just nearly break the internet? What the Spamhaus attack says about our security
 If you noticed your internet connection slowing markedly yesterday, with some sites sluggish and others unavailable, for once it might not have been down to your broadband supplier.
If you noticed your internet connection slowing markedly yesterday, with some sites sluggish and others unavailable, for once it might not have been down to your broadband supplier.
That's because spam fighting service Spamhaus was subjected to an enormous distributed denial of service (DDoS) attack.
It seems that Spamhaus blacklisted a controversial hosting provider, Cyberbunker, because its servers were apparently being used to send lots of spam. 'Friends' of Cyberbunker then bombarded Spamhaus with the biggest DDoS attack ever.
Are any of us innocent?
The incident spawned headlines like Global internet slows after 'biggest attack in history'. And with so much malicious data flying through the internet's wires, some innocent internet users found their service was disrupted as a result.
But how innocent are those internet users? Is our slack security as individuals partly to blame for the scale of the disruption?
It's an interesting question because this attack was coordinated using a huge 'botnet' of internet devices, including a large number of insecure broadband routers.
It's the exact threat experts recently warned us about, where hackers exploit weaknesses like default passwords to take control of these devices.
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equpment now from these trusted suppliers: |
Your router is part of the problem
As more details of the Spamhaus attack emerge, we might get a better idea of what devices it involved. But as The Guardian reports, that innocent-looking router in the corner of your office could have been a part of the problem:
"Some of those requests will have been coming from UK users without their knowledge, said Blessing [an internet expert]. "If somebody has a badly configured broadband modem or router, anybody in the outside world can use it to redirect traffic and attack the target – in this case, Spamhaus."
Obviously, whoever initiated the attack is ultimately responsible. However, the scale of it was partly due to the vast number of insecure internet devices out there.
We're all to blame
So, who is to blame? Manufacturers who sell their products with inadequate security and don't properly explain how to beef it up? Internet service providers that make their routers less secure so they can log in remotely when they need to? IT adminstrators who don't update their software promptly?
Or is it all of them, and each of us too?
The internet is a decentralised, open network. That makes it very difficult for any single body to effectively police this type of incident, and means that we're collectively responsible for the internet's security.
Yesterday, we almost broke it. Perhaps it's time we all took the time to be more secure online.
How to hack 420,000 internet devices
 Here's a stark reminder that internet security perhaps isn't quite as tight as we'd all like.
Here's a stark reminder that internet security perhaps isn't quite as tight as we'd all like.
An anonymous researcher managed to take control of 420,000 insecure internet devices like webcams, network routers and printers.
They were use to effectively create a huge network of internet devices that could be used for dodgy purposes like taking websites down via denial of service attacks. (The researcher didn't go ahead and cause any damage, but the potential was there.)
Standard passwords
Looking for a deal?See the latest business tech bargains we've found online. Or buy security software now from these trusted suppliers: |
What's striking about this research is both the huge number of devices that could be compromised, and the ease with which it could be done. Quite simply, the researcher accessed each device by trying standard usernames and passwords like admin or root.
In a month where a high-profile cyber-attack against South Korea hit the headlines, it's important for your business to remember that sometimes the simplest hacking attempts - like trying default usernames and passwords - can be just as damaging.
Don't neglect the obvious
The anonymous researcher summed up the problem in a post online:
"While everybody is talking about high class exploits and cyberwar, four simple stupid default telnet passwords can give you access to hundreds of thousands of consumer as well as tens of thousands of industrial devices all over the world."
In short: choose your passwords carefully. And whenever you add a new piece of equipment to your computer network, check if it has sign in credentials and change them if so. If you don't, you could be a part of this problem.
- The ABC of business IT security
- Most small businesses have had a security breach. Have you?
- Emma Watson could bring down your business computers
Image: Rob Kints / Shutterstock.com
Three things you can learn from NatWest's IT woes

Image: Flickr user StewC
If you were one of the millions of NatWest customers unable to access online banking, use debit cards or even get cash from a hole in the wall last night, the bank's reputation has probably dropped a notch or two in your mind.
It's hardly the kind of publicity a beleagured banking giant needs. However, major IT outages aren't restricted to banks. They can happen to any business. If one hits yours, it can have an immediate impact on your bottom line and longer-lasting consequences for your reputation.
So, as NatWest fights to deal with today's avalanche of negative coverage, what can you learn from its misfortunes?
Looking for a deal?See the latest business tech bargains we've found online. Or buy online now from these trusted suppliers: |
1. Keep communicating
One of the worst things you can do during an IT problem that affects customers is to go silent.
If you can explain the problem and when it's likely to be fixed, that's great. But even if you're unsure of the cause yourself, just being there to provide some information is better than nothing at all. At least you'll avoid that 'rats deserting a sinking ship' feeling.
Last night, NatWest was quick to apologise via Twitter, although few further updates were posted despite a veritable Twitter storm.
2. Learn from your mistakes
NatWest also suffered a huge outage last summer, which saw some people unable to access their money for days.
Although the bank has said yesterday's disruption wasn't connected to the previous problems, the fact that this is the second major outage in nine months has compounded the reputational damage, with many customers vowing to leave.
If a problem reveals failings in your IT systems, make sure you fix them properly. It may cost you time and it may cost you money, but the cost of inaction could be much larger.
3. Don't be afraid to say sorry
The most insincere apology I can recall in recent years is this classic from Apple. It's a great example of how not to do things.
Look, if your IT systems have failed and your customers were affected, it really is best just to apologise sincerely and explain what you're doing to fix things.
At this stage, being open and honest is the way to reassure customers that the same thing won't happen again.
Then make sure it doesn't happen again, of course. If NatWest suffers another outage any time soon then it'll take more than few words to restore its reputation.
The ABC of business IT security
 It’s good to refresh your knowledge when it comes to something as crucial as IT and data security. So here’s a slightly tenuous ABC of business IT security. Plus a D and an E for good measure.
It’s good to refresh your knowledge when it comes to something as crucial as IT and data security. So here’s a slightly tenuous ABC of business IT security. Plus a D and an E for good measure.
A is for anti-virus
Get good anti-virus software and keep it up to date. You usually have to subscribe to software updates, and don’t wait for this to expire before you renew it. Even a few days without adequate protection is asking for trouble.
Spyware - which attempts to extract information from your computer without your knowledge - is another threat. However, most anti-virus packages also include anti-spyware protection too.
You can shop around for the best anti-virus deals. Reputable suppliers include McAfee, Kaspersky and Bitdefender.
B is for backups
Ideally, all the data on your computer system needs to be backed up to external hard drives. This ensures that you won’t lose sensitive information if your computers are corrupted by spyware or viruses.
Inform your staff that they need to back up their data at the end of each day, and regularly remind them to do so. External hard drives don’t cost the earth (you can see a selection here on Amazon), and you’ll be saving yourself a lot of hassle if the worst comes to the worst.
C is for control
When it comes to protecting data from prying eyes, control is the key. If there are files on your company’s shared drive which you don’t want all your staff to view, you should control who can access them.
If you use Microsoft Windows, here’s how to restrict access to a certain folder:
- Right click the folder and click Properties
- Click the Security tab
- Click Edit and then Add
- Add the usernames of the people you want to access the folder into the box that appears on screen
- Click Ok
That’s it – you’ve created a list of people who can access that particular file or folder on the shared drive.
D is for data encryption
Encrypting your computer systems makes it harder for hackers and fraudsters to access sensitive business information.
This can be anything from emails and financial figures to documents and databases hat are stored on computers or servers in your business. You can also protect portable storage devices like USB drives, which protects them in the event of loss.
Setting up encryption software can be a little tricky, but this guide to encrypting your laptop is a good place to start. It’s also worth speaking to your IT supplier if you need help.
Encryption is an excellent way to ensure your business transactions are protected from unwanted attention. Even if a fraudster manages to steal a disk containing sensitive information, they should still be unable to read it.
E is for external help
Instead of relying on your own knowledge about maintaining computers, it is a good idea to have an trusted IT supplier you can turn to. They will help troubleshoot any problems with your system, allowing you and your staff to focus on running your business.
Even seemingly minor problems should be flagged up, as they can indicate larger problems with your IT security. It all helps avoid any lingering suspicions that your company has been targeted.
It’s often a good idea to choose a local IT supplier, so you can ask business contacts and friends who they’ve used in the past. Perhaps they could even negotiate you a discounted rate!
Written by online security expert, James Archer, on behalf of online retailer The Safe Shop
With IT risks worrying businesses most, here's how to cope
A survey into SME attitudes to risk has identified which of 24 'risk scenarios' (that's things that could go wrong, to you and me) are most likely to keep business owners awake at night.
The research, commissioned by McAfee, revealed UK SMEs view their technology systems and the integrity of their data as the biggest areas of risk.
In contrast, things that might traditionally have been perceived as significant risks - like big marketing campaigns or competitor initiatives - are seen as being much less likely to have a detrimental impact on business performance.
This graph shows the ten highest risks selected by businesses in the UK:
Although it's perhaps depressing that new technology is responsible for so many worries in business, this survey also suggests a greater awareness of the risks, which bodes well for long-term improvements.
What's more, most companies can reduce most of these risks by taking some fairly simple steps.
To start with, it's a good idea to create some sort of security plan. It doesn't have to be an enormous document, but writing even a short plan will force you to think about what the key risks are.
Once you've done that, make sure you've covered these basics:
- Get good IT security software from a reputable firm such as McAfee, Kaspersky, Bitdefender or Trend Micro. It can go a long way towards protecting your computers from viruses and hackers.
- Make sure you're on top of your IT maintenance and install software updates in good time. This will help you eliminate software bugs that hackers can use to break into your systems.
- Sort out your backups. Make sure you have a solid backup system in place and test it regularly. Cloud backup systems like Livedrive, Mozy and BackupGenie are good options for smaller companies.
- Think about how you'd cope in an emergency. You need to know how you'll carry on working in the event of problems and what steps you'd need to take to get things back to normal.
Finally, always remember that maintaining good IT security is an ongoing process. It's a good idea to find an IT supplier you trust and keep track of new security trends that could affect you.