Posts for January 2014
IT for Donuts: how to show UK dates in Google spreadsheets
IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week: if you use Google spreadsheets, you might have noticed that it defaults to show dates in US format. This can be incredibly annoying when you're in the UK, so we explain how to fix it.
Using Google Drive spreadsheets?
Google Drive allows you to create and work on documents, spreadsheets, presentations and more. It's Google's answer to Microsoft Office, and it saves all your documents online so you can access them anywhere.
Although it lacked a lot of features when it first launched, Google Drive is now more than adequate for many uses. In fact, we use it to manage blog posts and articles on IT Donut.
However, like many online apps, Google Drive is very US-centric. This is particularly noticeable if you're entering dates into a spreadsheet. Even if you enter them in UK format (like 15/01/2014), it converts them to US format (01/15/2014).
Changing your regional settings
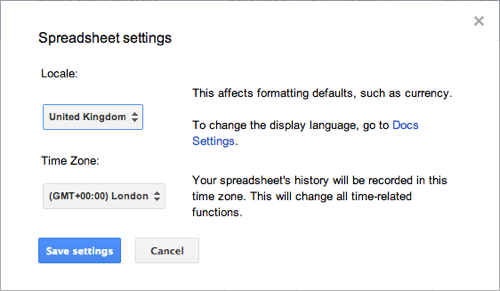
It's really easy to fix this annoyance, if you know where to look. When you're in your spreadsheet, just choose the File menu, then select Spreadsheet settings...
You'll see a box containing an option to set the locale (see image, above). Change this to United Kingdom, hit Save settings and you're done. Now you can work with dates that are written the correct way round.
Previous IT for Donuts posts:
Video job applications — for when a CV isn’t enough?
 If research from recruitment specialist Hello my name is… (HMNI) can be believed, the hottest trend in job applications this year is going to be video.
If research from recruitment specialist Hello my name is… (HMNI) can be believed, the hottest trend in job applications this year is going to be video.
That’s right: while for years we’ve relied on handwritten application forms and CVs to identify good prospects from no-hopers, now employers could be set to receive videos from candidates when they apply.
Cringe-inducing?
The research questioned 1,000 business leaders and discovered that candidates who upload a video accompaniment alongside their CV may have an edge.
The whole idea sounds a little cringe-inducing — especially if you’re not the sort of job applicant who feels comfortable making their own showreel — and so HMNI has given these short videos a suitably cringe-inducing name: the ‘MeVie’. (We think it’s pronounced ‘me vee’.)
Although some video applications have caused a stir online (check out this inventive example), that’s because they’re currently the exception rather than the norm.
If your business starts receiving a three-minute video with every three-page CV, are you really going to sit there and watch them all before drawing up your shortlist?
Besides, doesn’t video simply encourage employers to make decisions based on shallow attributes — like which candidates look good in front of a camera — instead of focusing on the things that really matter?
Put it this way: if you don’t have a camera-friendly nature or the skills to record and edit video, you’re going to be at a disadvantage. Even if you’re the best candidate for the job.
M&S seem to like it
That said, the concept of the MeVie does have the backing of Marks and Spencer, so perhaps there is something in it.
The retail giant’s executive director of general merchandise, John Dixon, said: “As an employer, there’s no doubt it can be problematic differentiating between candidates by CV alone. The MeVie allows you to see beyond the CV to the person behind it.”
I’ll be honest: I’m not convinced. You’ll still have to meet and interview the candidates you like, in any case. And surely the risk of video is that you might dismiss candidates who are uncomfortable or unhappy in front of a camera — while in reality they might be best for the job.
Would you start asking job candidates to send in video with their applications?
How to stop internet downtime crippling your business
 When your internet connection goes down, your business can suffer disruption that wastes your time and hits your bottom line.
When your internet connection goes down, your business can suffer disruption that wastes your time and hits your bottom line.
If that sounds all-too-familiar to you and your company, here are a few ways to reduce disruption caused by an unreliable internet connection.
1. Upgrade your old router
Consider upgrading your router if it’s more than five years old. Newer routers offer more reliable, stronger wireless signals, better security and faster downloads.
If you have laptops, smart phones or tablets that can operate using newer, faster wireless networking standards then make sure your router can perform at the same speed, too.
2. Check your computers for security problems
Security problems like malware and viruses can hit your internet speed by consuming your computer’s processing power and sending data across your internet connection.
Make sure you have good security software that’s working properly and gets regularly updated.
3. Reposition your router
If you rely on a wireless internet connection on your premises, where you position your router can dramatically affect the strength of the signal — and therefore the speed of your connection. Try and position it near the centre of your office, rather than leaving it in the corner by your phone socket.
If you still struggle to get a strong connection, consider getting a signal booster to improve coverage or connecting the most important devices to the router via a cable.
4. Check your contract
Some ‘unlimited internet’ packages aren’t actually unlimited. They have fair-use clauses or restrictions to ensure that one user’s heavy use doesn’t slow the service for others
If you exceed your package’s usage limit, you might be charged extra of have the speed of your connection capped. Your internet provider may also limit speeds at peak time, or slow access to sites that require a lot of bandwidth, like YouTube.
Ultimately, if your business requires a reliable, fast connection then you should consider investing in a fibre connection, if fibre is available in your area. However, these tips are a good way to make your connection more reliable without having to splash out on an upgrade.
- More ways to speed up your broadband
- Internet speed test
- Why your internet connection might be slower than you’d hoped
This is a guest post from Christian Nellemann, founder and group CEO of XLN Telecom, a specialist provider of small business broadband and phone services.
Apparently we need to send even more email
 Here’s a good one for you. According to new data from digital marketing agency Alchemy Worx, brands could increase engagement and revenue by simply sending more email.
Here’s a good one for you. According to new data from digital marketing agency Alchemy Worx, brands could increase engagement and revenue by simply sending more email.
Before we examine this idea any further, let’s just recap where we are in the world of business email:
- According to some research, dealing with email takes up more than a quarter of the average worker’s day.
- A while back, Google redesigned its inbox in an effort to tackle the growing problem of email overload.
- In 2012, there were a massive 144 billion emails sent every single day — most of which were probably rubbish.
In short: email is out of control. And they reckon we should be sending more of it?
More emails, more revenue?
The business behind this research, Alchemy Worx, is an email marketing agency. Its conclusions are based on an analysis of its own client data, which consists of 2.2bn emails sent to 40.6m recipients over the last year.
This analysis found that if a brand with five million email subscribers sent one more email to that list every month, it could achieve an extra 1.9m email opens and an extra 175,000 clicks on links in the emails.
Alchemy Worx reckons that could equate to an extra £1.8m in revenue.
Every business is different
So: send more emails and you’ll get more business. Is it really that simple?
Well, no. Even if we disregard the wider issue of inbox overload and the mess that will ensue if every company decides to send emails more often, it’s clear different businesses will see different results.
The best analysis I’ve found comes from MailChimp. If you’re re-evaluating your email marketing strategy then it’s worth reading the whole article, but the key point is that every business has an email sweet spot.
If you increase the frequency with which you email your customers, over time people engage with each individual email less.
This means that if you move from sending an email once a month to sending emails three times a month, you’ll almost certainly find your click through rate drops for each individual email.
As you’re now sending three times as many emails as you were before, the total number of clicks may still be higher. That means more engagement overall, and — potentially — more revenue.
But if you increase email frequency too much — say to five or six times a month — you could see lower engagement than with fewer messages.
You need to be more sophisticated
Email marketing is a long-term effort. You don’t want to undo all your hard work of building a list of loyal customers by sending them so many emails that they start to think of your messages as spam.
But equally, you don’t want to email so infrequently that you drop out of people’s minds altogether.
Quite simply, you need to figure out what works for your company. Again, MailChimp has summarised it well:
“I’d highly recommend ignoring calls to ‘send send send,’ and find a comfortable middle ground that feels balanced between individual campaign engagement and overall periodic engagement.”
So, while using your data to make decisions is important, there might be other considerations too. For instance, it’s increasingly possible to send targeted emails to specific groups of customers, rather than hitting everyone with the same email.
Finally, next time you’re about to press ‘send’ on a marketing email, spare a thought for the state of your recipients’ inboxes. With email, as with many things, less really can be more.
IT for Donuts: how out-of-office messages can be a security threat

While you're on the beach, is your email causing problems?
IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week: you probably use an out-of-office message to reply to emails automatically when you're away. But did you know they can be a security risk?
What's an out-of-office message?
Most email software and services will allow you to create a message that will be automatically sent to people who email you while you're away.
You can use this feature to let people know you might be slower to reply than normal, and to tell them who to contact in your absence.
See how to set up an out-of-office message in Microsoft Outlook or Google Mail.
The problem with out-of-office messages
Although out-of-office messages are certainly useful, they sometimes contain information that can be used by criminals. For instance:
- If you're a freelancer, it's a fair bet that you work from home. So if your out-of-office message boasts that you're on holiday in Australia, criminals might deduce that your house is an easy target for burglary.
- If your message includes a colleague's name, email or phone number, cyber-criminals can use these details in a spear phishing attack. They can email your colleague with a convincing-sounding message, to trick them into providing sensitive company data.
- If you've created an out-of-office reply that lets people know you're away for two weeks, criminals may try to impersonate you online, knowing that you're less likely to notice someone else using your identity.
However, these scenarios don't mean you should stop using out-of-office messages entirely. Just take some precautions.
Writing safer out-of-office messages
Being selective about the information you include in your out-of-office messages is the best way to minimise the security risk:
- Just say you're 'unable to respond to emails at the moment', instead of providing detailed information about your holiday.
- Don't promise to reply by a certain date or say when you'll be back.
- If possible, avoid providing a specific colleague's details. Instead, include a generic email address (like [email protected]).
- If you feel you must offer a colleague's details, only provide one name. Don't give scammers a whole list of targets.
- Consider setting two messages, if your email service allows this — one to be sent to colleagues, one (containing fewer details) to be sent to external contacts.
Do you bother with out-of-office messages when you're away from email?
How to take control of your inbox
 Email is a massive drain on productivity for many businesses. It’s not hard to see why. An inbox stuffed with thousands of unread messages is par for the course, making it easy to get sucked into a spiral of doom that goes as you try to discern what’s important.
Email is a massive drain on productivity for many businesses. It’s not hard to see why. An inbox stuffed with thousands of unread messages is par for the course, making it easy to get sucked into a spiral of doom that goes as you try to discern what’s important.
It’s tempting to hit the delete button to purge the lot and hope anything important will somehow make its way back to you.
But while it might be cathartic, wiping out your inbox will not help you gain control. Like a crash diet, it will all pile back on eventually.
Instead, here are five to put you in charge of your inbox, for good:
1. Keep it secure
Email security should be top priority when managing your inbox. With so much valuable data in there around, it’s essential you’re confident that it’s secure.
Threats include malware, spam, phishing and data leaks. While they can seem complex, taking some basic IT security precautions will go a long way to keeping you safe. You can also purchase software and tools to boost your security.
2. Start unsubscribing
Virtually every website you encounter will try to lure you into subscribing to updates and it’s very easy to forget just how many you’ve signed yourself up to.
Until, that is, your inbox is stuffed senseless with newsletters and promotions that you have no interest in. Be ruthless: do you really need to receive details of every promotion and special offer that’s going on?
3. Don’t put off responding
While it might be easy to push aside emails and deal with them later, you know it will most likely never happen.
Instead, you end up with a growing pile of unread mail that seems to reproduce all by itself. Act on each email straight away and decide whether it needs a response or whether you can just delete it.
4. Be more organised
Nearly every email package allows you to create folders for your email, so make use of this feature.
It’s wise to create logical divisions based on your workflow or needs. For example, if you have several clients to manage, having a folder for each will help keep communication clear and organised. You can even categorise personal email into groups like family, friends and purchases.
5. Standardise replies
A cookie cutter template email might seem like a horribly impersonal way of responding.
However, if you find yourself sending the same message over and over again to different people, it can be a good way to minimise the time you need to spend on email.
- Ten ways to use email effectively
- How to stop email ping-pong games dead
- Streamline your email and save time
This is a guest post from Ben Williams, on behalf of Mimecast email security.
Ten security predictions for 2014
 You’ve already seen our exciting IT predictions for 2014. But what of IT security and data protection? Are there any threats your business needs to know about?
You’ve already seen our exciting IT predictions for 2014. But what of IT security and data protection? Are there any threats your business needs to know about?
Alex Balan, head of product management at internet security firm BullGuard, has come up with these ten predictions.
1. Ransomware
It’s devious and destructive and it makes hackers money. Ransomware has been around a while, but because it’s effective it’s going to be around for a lot longer.
A good example of ransomware is Cryptolocker. It encrypts your documents and shows a message saying you must pay a ransom to get your computer back. If you don’t pay up then you lose your data — and there’s little anyone can do to help you.
2. Mobile malware
There is a growing body of evidence to show mobile devices being attacked, with online criminals often aiming to steal personal financial details.
This is hardly surprising given the explosive growth in smart phones and tablets. There’s plenty of data on mobile devices to be stolen. Hackers can also make money by setting up their own premium-rate numbers, then dialling them from compromised mobile phones.
Learn more about mobile security software.
3. Shoring up personal security
The news about the NSA and GCHQ monitoring internet traffic, emails and phone calls was the most important cyber security event in 2013. These revelations have increased awareness of the need for personal security.
Until now, people have generally only taken security precautions reactively, typically after something has happened. But now they’re becoming more proactive. This will create a growth in technologies to help users keep their communications and data private.
4. Forget me not
We’re likely to see more attacks on old software and systems that are full of security holes. For example, Microsoft XP reaches the end of its life in April, which means no more updates, even if a security problem is found.
This popular but creaking operating system is widely used and how many people know Microsoft is turning its back on it? Hackers know, of course. There will be many attempts to find new exploits in XP, which means many people will fall victim to malware.
5. The internet of things
You may or may not have heard of the ‘internet of things’. It describes the increasing connectedness of everyday objects. We have internet-connected webcams, CCTV systems, televisions, digital video recorders and even baby alarms. These devices may be vulnerable to attack.
It might sound bizarre, but soon we’ll see fridges, toasters and other devices that are hooked up to the internet. Don’t be too surprised when you hear of these things being hijacked by hackers (fancy a hacked toilet, anyone?).
6. Back it up
Never in the history of humankind has an industry grown so rapidly and so pervasively as technology. It reaches into every corner of our lives. Film cameras are a thing of the past, physical bank branches are becoming quaint and well-known retailers have disappeared from the High Street.
But what happens when computers crash? Thankfully, more people are aware of the potential for damage, and this is leading to an increase in back-up technologies. Expect the arrival of more backup services this year — especially ones that work over the internet.
7. Biometric authentication
Biometric authentication is widely regarded as the most secure form of identity control. Early systems were slow and intrusive, but because today’s computers are faster and cheaper than ever, the interest in biometrics has been renewed.
There are several types of biometric authentication in use, but fingerprint authentication is becoming the most common. We’ll see more computers, mobile devices and accessories with built-in fingerprint readers this year.
8. The deep web gets deeper
Law enforcement agencies have scored some significant ‘deep web’ successes the past year, most notably taking down of the Silk Road web site, which allowed users to buy anything from heroin and cocaine to guns and fake currency could be bought.
Authorities will continue to make inroads into the deep web in 2014 but the odds are that deep websites will respond by making it harder to take down sites or identify the people responsible.
9. Smart phones in the workplace
You may not realise it, but when you take your smart phone into the workplace and hook it up to your computer, you’re committing a security faux pas. If your device has malware on, you risk releasing it into the company network.
Hackers love breaking into company networks because they are treasure troves. And because smart phones are so popular, hackers are targeting them in order to access corporate networks. We’ll see an increase in this type of activity in the coming year, so it pays to be aware.
10. Service provider hacks
When an internet service provider (ISP) gets hacked it resonates long and loud. In April 2013 UK giant BT dumped Yahoo as its email provider following months of hacking complaints from customers.
Many hackers break into ISP systems just to get free broadband, but at the organised crime end of the spectrum it’s done to launch large-scale spam and malware attacks. Don’t be surprised to see more ISP hacks in the coming year.
- Eight tech mistakes your business could make in 2014
- The big 2014 tech predictions list
- Will wearable tech be big in 2014?
This is a guest post from Alex Balan, head of product management at BullGuard.
IT for Donuts: do I need a 4G connection?

Image: 1000 Words / Shutterstock.com
IT for Donuts is our regular Friday feature where we explain a tech term or answer a question about business IT.
This week: now that most mobile phone networks offer 4G tariffs and handsets, is it worth considering 4G for your business?
What is 4G?
4G is a relatively new kind of mobile internet connection. It allows you to connect your smart phone or tablet computer to the internet at very high speeds, while you’re out and about.
4G is named because it’s a fourth generation mobile network. It follows on from 3G, which you probably use at the moment if you access the internet through a smart phone. The main mobile phone networks offer 4G connections, including O2, EE and Vodafone.
What makes 4G special?
If you’re familiar with 3G, you can think of 4G as the same thing, but much speedier. In the right circumstances, a 4G connection can be three to four times faster than your average home broadband connection, giving you the ability to do more online when you’re out and about.
All that speed means 4G can be a boon if you need to send and receive large files when you're on the move, like this aerial photography company that uses it to process large images.
But because 4G is faster, it's also makes for snappier all-round internet access. For instance, your phone or tablet should download emails and display websites faster, reducing those frustrating moments while you wait for something to load.
Sounds great. What's the catch?
To get a 4G connection, you need three things:
- A mobile device capable of 4G. Many of the latest smart phones and tablets can connect to 4G networks, but you'll find most older devices won't be able to.
- A 4G mobile tariff. Guess what? Because 4G is better than 3G, it costs more to get a 4G contract from your mobile network. Expect to pay at least £5 — £10 a month extra.
- A 4G signal. 4G network coverage is improving fast in urban areas, but if you spend a lot of time outside major towns and cities then you'll find 4G availability is patchy.
So, to start using 4G you're probably going to need to buy a new mobile device, get a new contract, and check the coverage in areas you expect to use it.
Should I move to 4G?
4G is a genuinely worthwhile upgrade, if you can afford it and if it's available in the places where you spend most of your time. You'll notice a real improvement even compared with a good 3G connection, and it should eliminate some of the frustrations of mobile internet access.
However, at the moment it's hard for your average company to make a convincing case for moving to 4G. In fact, 3G is still more than adequate in most circumstances, even if you might have to wait a few extra seconds to download your email.
That means most businesses will be fine with 3G for now. But improving coverage and (hopefully) falling prices, the story could be different in six to 12 months' time.
Could technology replace nearly half of current jobs?

If you're looking for some thought-provoking reading on this dull Friday, there's an excellent piece over on The Economist website about how advances in technology could soon spark massive changes in the jobs market.
According the the article, an Oxford University study reckons 47% of today's jobs could be automated in the next 20 years.
Of course, this phenomenon is nothing new — as the article observes, machines have been displacing humans for years:
"In the Industrial Revolution artisan weavers were swept aside by the mechanical loom. Over the past 30 years the digital revolution has displaced many of the mid-skill jobs that underpinned 20th-century middle-class life."
However, it's the sheer speed of change in the 21st century that could spell trouble ahead. Although history demonstrates that technology creates new jobs to replace those lost, there's a lag, as shown by the huge disruption in the photographic market:
"When Instagram, a popular photo-sharing site, was sold to Facebook for about $1 billion in 2012, it had 30m customers and employed 13 people. Kodak, which filed for bankruptcy a few months earlier, employed 145,000 people in its heyday."
Computers are getting better at doing more complicated tasks, and we may not be far from having self-driving cars, robot baristas and even computerised doctors.
That's going to bring plenty of busines opportunities, for sure. But it could also spell significant changes in society. Are we ready to deal with them?
How to stop internet downtime crippling your business
 When your internet connection goes down, your business can suffer disruption that wastes your time and hits your bottom line.
When your internet connection goes down, your business can suffer disruption that wastes your time and hits your bottom line.
If that sounds all-too-familiar to you and your company, here are a few ways to reduce disruption caused by an unreliable internet connection.
1. Upgrade your old router
Consider upgrading your router if it’s more than five years old. Newer routers offer more reliable, stronger wireless signals, better security and faster downloads.
If you have laptops, smart phones or tablets that can operate using newer, faster wireless networking standards then make sure your router can perform at the same speed, too.
2. Check your computers for security problems
Security problems like malware and viruses can hit your internet speed by consuming your computer’s processing power and sending data across your internet connection.
Make sure you have good security software that’s working properly and gets regularly updated.
3. Reposition your router
If you rely on a wireless internet connection on your premises, where you position your router can dramatically affect the strength of the signal — and therefore the speed of your connection. Try and position it near the centre of your office, rather than leaving it in the corner by your phone socket.
If you still struggle to get a strong connection, consider getting a signal booster to improve coverage or connecting the most important devices to the router via a cable.
4. Check your contract
Some ‘unlimited internet’ packages aren’t actually unlimited. They have fair-use clauses or restrictions to ensure that one user’s heavy use doesn’t slow the service for others
If you exceed your package’s usage limit, you might be charged extra of have the speed of your connection capped. Your internet provider may also limit speeds at peak time, or slow access to sites that require a lot of bandwidth, like YouTube.
Ultimately, if your business requires a reliable, fast connection then you should consider investing in a fibre connection, if fibre is available in your area. However, these tips are a good way to make your connection more reliable without having to splash out on an upgrade.
- More ways to speed up your broadband
- Internet speed test
- Why your internet connection might be slower than you’d hoped
This is a guest post from Christian Nellemann, founder and group CEO of XLN Telecom, a specialist provider of small business broadband and phone services.
How to avoid five big email headaches
 A flexible, modern email system can really make your life easier. Advanced email clients combine your email, calendar, address book and file management tools to make it easier to find the messages and files you need.
A flexible, modern email system can really make your life easier. Advanced email clients combine your email, calendar, address book and file management tools to make it easier to find the messages and files you need.
Here are some of the ways an advanced email system can help you avoid the most time-consuming, headache-inducing aspects of email.
1. Finding and organising related files
We often store messages, documents and files relating to the same subject in different places. This means you need to waste time switching between different apps and windows to access them.
An advanced email system will help you keep all information about a particular subject in a single folder. You can assign categories to files and folders too, making it easier to identify what you need.
2. File loss and corruption
Most email systems store messages, attachments, calendar data and contacts within a single database file (in Microsoft Outlook, for example, data is stored in .pst files).
As the file grows in size, performance suffers. But more seriously, if it gets deleted or corrupted, you can lose everything. An advanced email client avoids this by processing and storing messages and documents as separate files in regular folders.
3. Data security and downtime
Even the very largest, most reputable email services can go down occasionally. This can leave you cut-off from crucial data.
An advanced email client will combine offline and online storage so that data is stored on your computer as well as on the email server. This means you can access it even if the email service goes down.
4. Switching between accounts
One big limitation of web-based email services like Google Mail is that it can be tricky to access more than one email account, address book or calendar without constantly logging in and out.
However, advanced email clients can connect to and work with several accounts at once, so you can use multiple mailboxes, calendars and address books more easily.
5. Getting support when you need it
Modern email applications have become increasingly more sophisticated. That’s a good thing, until you run into a problem. Then it can feel like you’re on your own — especially if you’re using a free service.
Switching to an advanced email client for which you pay a small amount each month should give you access to proper support channels, so you can search for help online or pick up the phone if you get stuck.
- Digging for gold in your inbox
- How to sort your email out once and for all
- Control yourself, and your emails
This is a guest post from Vladimir Spirin, managing director at EverDesk.
Eight tech mistakes your business could make in 2014
 If you’ve read our expert predictions for 2014, you should have some idea of what might happen in the world of technology this year.
If you’ve read our expert predictions for 2014, you should have some idea of what might happen in the world of technology this year.
But if you cast your mind back to 2013, was there anything about your business technology that you regret? Maybe you’ve barely used that new tablet you bought, or have struggled to cope with your ‘phone phobia’.
To help you avoid making any errors in 2014, here are the top eight IT mistakes businesses will make.
1. Plodding along with slow broadband
There’s little that will take a sledgehammer to productivity more than slow, clunky or inefficient broadband.
Even if you’ve switched to a faster fibre connection, you’re almost certainly sharing bandwidth with other businesses nearby. You could consider moving to an Ethernet service, which offers the benefits of a fibre connection, plus less competition for bandwidth.
2. Picking up someone else’s phone bill
It’s one thing picking up the tab after a swanky business lunch, but what about your phone lines? As voice networks have become more sophisticated, so have the scams used by phone hackers, fraudsters and other criminals.
Hacking is a growing threat to any business connected to the public telephone system. Estimates as to the scale of the problem vary, but it’s thought that fraudsters are generating calls worth billions that customers are legally obliged to foot the bill for. Ask your provider if you’re protected.
3. Holding back from the cloud
A remarkable number of businesses still feel overwhelmed by the C-word. ‘Data sovereignty’ is the latest hot potato, with managers fretting over where their data is held and who can access it.
A trusted cloud provider will be able to create a solution for your business, rather than relying on a one-size-fits-all approach. The cloud is a buzzword that’s stuck around for a reason. And that’s because the benefits of converged, hosted infrastructure in the cloud are convincing.
4. Assuming BYOD is sorted
So, all your employees are happily using their own smart phones, laptops and tablets in your business. You’ve nailed this ‘bring your own device’ (BYOD) thing, right?
What’s not to love about BYOD? Well nothing, until someone leaves a laptop on the 0642 to Euston. Most businesses don’t have any way to track and manage the data on these devices. If one of your team lost a smart phone, could you handle the consequences? If not, add BYOD security to your to-do list.
5. Not virtualising your servers
Having a stack of ageing servers sitting in a cupboard is just burning money — not to mention the cost of having someone to back up and maintain them.
Moving to reliable, efficient virtual servers hosted by an external provider will free up your time, space and money. They’ll give you more peace of mind, too, because you’ll know it’s the supplier’s job to look after them.
6. Ignoring the video revolution for another year
Getting déjà vu? It’s true that every year in recent memory has been the year of video conferencing. But with better devices and software now available, is it coming of age at last?
With remote working going from strength to strength, it looks as though video is finally going to have both the demand and the technology it needs to become standard in business.
7. Taking the soft option on security
Your internet security is taken care of, a firewall is in place and there’s a rigorous system to regularly reset passwords.
But are you neglecting some obvious risks? While an intruder on your intranet would set alarm bells ringing, how easy would it be for a couple of imposters in hi-vis jackets to wander on site unchallenged? Don’t forget the basics.
8. Sticking with out-dated phone systems
Still running most of your calls through traditional telephone lines? Then it’s worth taking a serious look at switching to a system that combines telephone and data services into a single connection.
A common solution is SIP (it stands for session initiation protocol). This technology connects your private company switchboard to the internet. Calls are then placed through your internet connection. This can reduce
line rental and call costs, as well as providing more flexibility.
- The big 2014 tech predictions list
- Cloud telephony: when disruption is a good thing
- You can’t avoid bringing your own device
This is a guest post from Timico.
Which card payment terminal is right for you?
 If you want to start accepting card payments, there’s a wide range of card payment machines to choose from. With so many options available, it can be hard to know where to start.
If you want to start accepting card payments, there’s a wide range of card payment machines to choose from. With so many options available, it can be hard to know where to start.
The first thing to do is consider your business and your customers. What do you sell? Are you always at a desk or are your customers spread out? How do you carry out most transactions: face to face, over the phone, online?
Once you answer these three questions, the type of card payment terminal you need should become clear. There are three basic types:
- Countertop card payment terminals. These operate from a fixed location. They can operate via dial-up (using your phone line) or over your existing broadband connection, and fit on to most shop counters.
- Mobile card payment terminals. These have a SIM card like a mobile phone and are used mainly by delivery services, market traders and other businesses on the go — anywhere where there isn’t a fixed point of sale or broadband connection.
You need a mobile phone signal to use a mobile card payment terminal. Some of use an app on a smart phone along with a Bluetooth connected chip and pin keypad. - Portable card payment terminals. These are popular with hotels, restaurants, bars, hairdressers, coffee shops and in other situations where the customer is not always in the same spot.
The terminal will operate within a certain radius of its base unit, which connects to your phone line or broadband like a countertop terminal.
One other thing to consider is whether you’d like to have the ability to take contactless payments, where customers can pay smaller amounts by waving their card over a card reader, instead of having to input a PIN.
To encourage use of contactless payments, some payment providers are offering lower commission rates on debit card payments, so if this appeals to you and your customers, it could be worth your while.
All types of card payment terminals are available with contactless functionality.
Andy Macauley is chief operating officer of Handepay.
Product intelligence: the future of ecommerce?
 When you’re selling online, how quickly you’re able to deliver your products can make or break your business. If your next-day delivery promise turns out to be hogwash then you’ll see customers switching to more reliable competitors.
When you’re selling online, how quickly you’re able to deliver your products can make or break your business. If your next-day delivery promise turns out to be hogwash then you’ll see customers switching to more reliable competitors.
The University of Cambridge, working together with James and James Fulfilment, is carrying out research that it thinks could lead to a new means of online order delivery — allowing consumers to interact with their order almost right up until it arrives.
Ecommerce product intelligence
The research is based on the concept of ‘product intelligence’, where computer models allow every product and order in a warehouse to effectively think for itself.
What does that mean? Well, if the researchers are correct, orders themselves will soon be able to communicate with warehouse and delivery staff to make sure that they are processed correctly.
Product intelligence could let consumers interact with their order right up until it is delivered.
For instance, currently if a customer wants to change the delivery address once an order has been dispatched, they have to contact the courier. But with product intelligence, they could let the order know the new address — electronically.
Popping out? Let your order know
In fact, it could be possible for consumers to interact directly with their online orders at every stage of the journey.
You might be able to tell your order that you’re are not at home because you’ve popped to a café down the road. Or you could even say: ‘use my mobile phone to come and find me’ while your parcel is out for delivery. Imagine that: no more ‘we called while you were out’ cards.
The difference with product intelligence is that the order will tell the carrier what it needs to do, rather than the customer telling the carrier. It sounds futuristic, but the infrastructure is mostly already in place, so the technology could become available very soon.
Product intelligence and efficiency
Product intelligence could also allow goods to decide where in a warehouse they should be stored. The researchers have found that doing this can be 20% more efficient than current best practice.
Although it might seem obvious that the fastest-selling products should be kept closest to the packing station, actually getting the information required to arrange products correctly is not easy.
When the products can confer amongst themselves, products that are frequently shipped together will know they should be stored together.
While online ordering has vastly improved in the past decade to become a slick, real-time process, many fulfilment centres and carriers have failed to invest at the same rate.
That’s why product intelligence has such huge potential: it could save businesses considerable time and money, and deliver much higher levels of customer satisfaction.
- Are small companies lagging behind in ecommerce?
- How to convert reluctant customers online
- Set up ecommerce on a budget
This is a guest post from James and James Fulfilment.



