Posts for April 2013
Bring your own device: get your BYOD policy right

Unlike in the photo, tablets usually have something on the screen when people use them.
Each year, small business owners are bombarded with a barrage of new acronyms and hot tech trends to watch – some of which are more applicable to a small and growing businesses than others.
But bring your own device (BYOD) is not something they can dismiss as a buzzword irrelevant to their own organisations. In fact, with a massive 40% of UK small business workers able to choose the device they work on, compared with just 20% of large enterprise workers, BYOD is more of a reality for small businesses today than their larger counterparts.
The reality is that BYOD is pervasive, whether businesses like it or not, or have a BYOD policy in place. Employees are truly driving the change, with 37% bringing non-compliant devices into their business networks before formal policies are established.
What’s more, consumer appetite for such devices shows no signs of cooling. More than six million Brits had a smartphone as well as a tablet in December 2012. The same comScore research found almost a third of all UK page views come from mobiles and tablets.
Benefits of BYOD
So what benefits could BYOD offer business? For smaller companies, there is the clear IT infrastructure and cost rationalisation for allowing employees to use their own devices. However, perhaps more significant is what BYOD promises in terms of productivity.
A Dell Quest study into global BYOD trends (PDF link) found 70% of companies believe BYOD improves employee productivity and customer response times. With the flexibility to use devices that best suit their preferred modes of working, employees have an opportunity to work more efficiently and creatively.
What’s more, as the blurring of the private and business worlds continues, employees are going to demand more from IT, so there will be an increasing need for businesses to offer a culture of enablement, rather than one characterised by limitations.
This may explain why 71% of organisations believe implementing a BYOD policy improves workforce morale, while 65% recognise it can be a valuable tool for attracting and retaining talent.
These advantages can help a business to maintain its competitive advantage and avoid getting left behind – something 59% of organisations (PDF link) feel could happen in the absence of a formal BYOD policy.
But the onslaught of multiple devices and operating systems means businesses are grappling with the task of safely and securely enabling staff to create a personalised workspace that enhances the user experience and promotes productivity.
Creating a BYOD policy
There’s no one-size-fits-all approach when it comes to BYOD policy, but there are some key considerations for businesses:
- Access rights and data security. Data protection is the largest pain point for businesses grappling with BYOD. As privately-owned tablets log on to corporate networks and exchange company files, it becomes harder for businesses to guarantee the accessibility, availability and protection of data.
IT must become an enabler, ensuring data is available regardless of where and how it is stored and accessed. Business owners must account for company data that’s out and about with an employee, ensuring its security when moving between secure corporate servers and unregistered personal devices. - Financial and management considerations. The more devices accessing the likes of email and remote desktop, the more support issues come up, stretching IT resources. A strict policy helps minimise these costs.
- Accounting for the user. Users themselves are the principal security risk within an organisation. Companies not only have to deal with people bringing in devices, but also other home-owned and managed applications and services as users demand a specific experience in their work environment.
As time goes on, more devices, operating systems, services and apps will provide a growing number of interfaces with corporate data. A company must consider how they can implement policy-based user and content management to mitigate the risks.
Crucial to any successful policy is ensuring that an employee-centric approach is taken. Companies mustn’t only consider productivity and cost-savings, but must ensure users are comfortable committing to a BYOD programme:
- Make workflows simpler for employees. Find and implement data solutions that help integrate personal devices and traditional IT without complicating things for employees. Use desktop virtualisation to enable access to corporate content, personal content and external material in the same interface without jeopardising the integrity of corporate data from any location.
Mobile device management systems (MDM) help a business monitor when staff send and receive email, and access corporate data and external sites - depending how the employer configures their system. Staff must be comfortable with how their personal devices are monitored for security. - Outline how devices may and may not be used when connecting with company resources. Outline which operating systems, apps and sites will work, and those which may have limitations. Provide alternatives, not obstacles. Prevent employees using unsafe services by providing adequate alternatives.
- Clearly detail the security requirements for password protection, the rights of the company to lock or locate a lost device, and how much staff can expect the business to pay towards the cost of equipment and data use.
- Take a multi-layered approach to technology. Combine numerous security technologies into a layered approach with proactive and reactive data protection. Carry out regular security audits to ensure vulnerabilities are addressed.
- Future-proof your business. Update your business continuity plan to reflect BYOD realities. For example, make it easy to report lost devices so the company can cut access swiftly.
Far from being the current hot trend, BYOD is already happening. Those businesses able to approach it with preparation, the right technology, and an open mind will be primed for success.
Sarah Shields, General Manager and Executive Director, Dell UK.
Can the sounds of a cafe increase your creativity?

Ok, it's time to get creative! You need ideas, and you need them fast.
But wait. If you're working in an open plan office then it's just too noisy to concentrate on the creative process. And if you retreat into a silent meeting room or opt to work from home then it's far too quiet to come up with those super-imaginative ideas.
A simulated cafe
No worries. I know what you need: the ambient sounds of a cafe, without the hassle of actually having to go to a cafe.
Let me introduce Coffitivity, a website that plays the ambient sounds of a bustling coffee shop through your computer speakers or headphones.
Calm and commotion
The creators of Coffitivity claim 'the mix of calm and commotion in an environment like a coffee house is proven to be just what you need to get those creative juices flowing'. They even provide some research to back up their claims.
Does it work? Give it a go and see for yourself. If you don't fancy a simulated coffee shop experience, you could always try white noise, nature sounds or, er, 24 uninterrupted hours of ambient sound from Star Trek.
|
Sponsored links: |
TOTW: what to do if your mobile phone gets dropped in water
 Smart phone, meet glass of water / pint of Guinness / insert damp environment as applicable. Being dropped in water or another liquid is a common way for a mobile phone to meet its end.
Smart phone, meet glass of water / pint of Guinness / insert damp environment as applicable. Being dropped in water or another liquid is a common way for a mobile phone to meet its end.
Someone should probably tell that to the 75% of owners who use their expensive smart phone while on the toilet.
For this tip of the week (TOTW), we explain what to do if your mobile phone gets dropped in water.
Recovery is by no means guaranteed, but swift action can often save a smart phone from a watery grave.
1. Move fast and pop the battery out
Are your reactions good? Let's hope so, because the first crucial step to saving your mobile phone when it's been dropped in water is to fish it out and pop the battery off the back.
If the phone appears to still be functioning, don't try and turn it off first. Pressing buttons could let more water inside or fry the circuits.
Once it's powered down the chance of damage is lower, so the quicker you can do this the better. If your handset is an iPhone, or another model without a removable battery, you'll have to switch it off instead and hope for the best.
Whatever you do, don't be tempted to try and turn it on after a few minutes just to 'check if it's ok'. You could do irreversible damage.
2. Dry the water from your phone
IT dealsSee the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
Assuming you've already removed the battery, take out the SIM card and remove any other accessories, like memory cards or headphones.
Then grab some kitchen towel (or whatever you have to hand) and dry the outside of your mobile phone as thoroughly as possible. Your aim is to stop water leeching in through gaps in the case.
It can take real effort to remove all traces of water from handset keypads, headphone connections and so on.
You may be tempted to use a hairdryer, but don't. The air can actually push water further into your device. Instead, try using a vacuum cleaner to suck water from nooks and crannies.
3. Leave it to recover
Even if your mobile phone looks bone dry, there's likely to still be water where you can't see it. Before you take the risk of switching it back on, give it a decent chance to dry out.
A good option is to leave your handset in a bowl of rice for a few days. This may draw the moisture out for you. Alternatively, you can buy special bags to draw out any damp lurking in your smart phone. Try this Bheestie bag (£14.99) or this kit (£14.20).
The key here is to be patient. Don't leave your phone in an overly-warm place or be tempted to heat it up, as this may do more harm than good.
After a few days, check your handset and give it a good shake to see if any water droplets emerge. If there are no signs of damp, you can put it back together and risk turning it on. If you're lucky, it'll spring back to life. If not, you'll need to take a trip to a repair shop.
Dell XPS 12 review: a tablet and laptop in one?
A Dell video promoting the XPS 12.
The Dell XPS 12 convertible ultrabook is the PC manufacturer's latest attempt to marry laptop and tablet technology into a sleek, sophisticated all-round business machine.
With prices starting at £999, it'll have to be good to convince business owners and executives to ditch their existing iPads and laptops.
We spent a few days with the top of the range model, which clocks in at just under £1,300. Here's how it fared.
Dell XPS 12: good first impressions
This Dell Ultrabook is a sleek, solid machine. It comes elegantly packaged in a classy box (well, it's as classy as a cardboard box can be), and the laptop itself is clearly well made.
The external finish feels good and the screen's hinge is substantial. There are none of the tacky lights, badges or finishes you often see on laptops. Quite simply, it looks and feels like a premium laptop.
Weighing in a 1.54kg, it's light enough to pop in your bag and carry around all day. It also feels more than up to withstanding the odd knock, which is inevitable for any mobile computer.
It's all about the screen
IT dealsSee the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
The XPS 12 has a superb 12.5" touch screen. It's bright, clear and has a full high definition resolution of 1920 x 1080 pixels. This means text and images are very sharp - it must be one of the best screens at this size on the market. (Learn about screen resolution.)
The only downside of such a high resolution is that text appears quite small in standard mode. You can fix this by cranking up the text size in Windows, but non-technical owners may be unaware this is possible. (Instructions are here.)
The screen has another trick up its sleeve too. It rotates through 180 degrees to transform from a laptop form factor to a tablet.
Basically, you rotate the screen then close the laptop, leaving the screen facing upwards and covering the keyboard. You can see it in action in the Dell promotional video at the top of this review.
The touch screen features are more useful than we'd expected when using the XPS 12 in 'laptop' mode. It's certainly true that the Windows 8 interface makes more sense when you experience it on a machine that has touch capabilities.
In tablet mode, you use the touch screen exclusively. It works pretty well, except when you have to venture into the Windows 8 desktop, which is best navigated via the mouse.
Capable and powerful
As you'd expect from the technical specifications, this is a very capable machine. The Intel i7 processor flies through tasks, and we were particularly impressed at the speed with which the XPS 12 starts up.
That's down to the 256GB solid state drive, which means Windows and other programs load impressively quickly. You can comfortably use this as your only machine - whether in the office or out and about.
In fact, when you're out and about you'll appreciate the responsive keyboard and track pad, although we did find it easy to nudge the volume switch on the side of the case when you're typing at speed.
Battery life is reasonable too, if not stunning (expect to get around five hours of work from it). Die-hard mobile workers may be disappointed that the battery is built-in, so you can't swap it when it runs flat.
Is the design worth the price?
There's no doubt at all that as a thin, light laptop, the XPS 12 ranks highly. The fast load times and impressive screen stand out. We'd happily use it as our main computer.
But we're sceptical about the tablet features. Although the touch screen is useful, it's hardly essential. And while the rotating display is cleverly designed and solidly engineered, in tablet form the XPS 12 is just a bit too heavy.
It's twice the weight of an iPad and significantly chunkier, which means it's not practical to hold the XPS 12 for long periods (like when you're reading during your commute or taking signups at an exhibition).
If you want a top-end laptop for occasional use as a tablet, you won't do much better. But if you want a laptop and a tablet, we'd say buy a laptop and a tablet instead.
You can learn more about the Dell XPS 12 and buy online from the Dell website.
Business tech bargain: a great Lenovo laptop for under £450
 This business tech bargain is a great-value laptop from Lenovo, a respected manufacturer that makes machines highly-rated for reliability. In fact, you'll find Lenovo computers in use at many of the world's biggest companies.
This business tech bargain is a great-value laptop from Lenovo, a respected manufacturer that makes machines highly-rated for reliability. In fact, you'll find Lenovo computers in use at many of the world's biggest companies.
To be specific, it's the Lenovo Ideapad Z580. This 15" mid-range workhorse laptop has a capable Intel i5 processor, a big 1TB hard drive (that's enough storage for almost anything) and 8GB of RAM.
In short, it's more than enough to handle the business applications you might throw at it, unless you need to do graphic design or work with video, in which case you'll need a laptop with a more powerful graphics chip.
Being a Lenovo laptop, you can also be confident it'll be built to stand up to the odd knock and should last you a good few yars.
Oh, and the price? It's currently available from online merchant Dabs at £462. However, if you use voucher code Z580 then you'll get it for a bargain £442 all in.
See details and buy from Dabs >>
|
Sponsored links: |
Fancy hanging out with Boris?
Here's one for your diary. Late tomorrow afternoon, Boris Johnson will be holding his first Google Hangout, live from London tech event the InnoTech Summit.
According to an enthusiastic press release, BoJo will be exploiting the search giant's video chat platform to connect with US venture capitalists. He's aiming to promote the UK's growing digital economy and attract investment to London's technology hub, Tech City.
The Mayor of London is, apparently, the first high-ranking UK politician to hold a multi-party video chat in this way. On the international stage, it's fair to say Barack Obama got there first, holding a White House Hangout in February.
However, although the discussions might be interesting, it seems likely many will join the Hangout to see how Boris manages to juggle the twin challenges of handling technology and communicating with an international audience.
As this video shows, it didn't go so well last time he attempted to operate a complex piece of machinery:
If the thought of watching Boris hanging out doesn't horrify you too much, you can join the Hangout here from 5pm tomorrow. Let us know how it goes.
Protect your business from a cyber attack
 There are an estimated 4.8 million small and medium-sized enterprises (SMEs) in the UK, many with their own ecommerce websites.
There are an estimated 4.8 million small and medium-sized enterprises (SMEs) in the UK, many with their own ecommerce websites.
In 2011, 32 million people purchased goods or services online. That gives the UK one of the world's biggest internet-based economies. And it's why keeping your website safe and secure from cyber-attacks has never been more important.
SMEs are easy targets
As a business owner, you’re probably dealing with plenty of critical day-to-day issues. Perhaps worrying about your website’s security is not top of your list of priorities.
You may be wondering why hackers would want to target a small business rather than big brands like Lush and Adidas. The simple answer is that hackers know smaller businesses have fewer resources dedicated to online security, making them easier targets.
For those involved, cyber crime is big business. It costs the global economy $338bn a year which, according to Symantec, is significantly higher than the global narcotics black market.
Since the beginning of 2010, 36% of all targeted cyber-attacks have been directed at SMEs.
With around 44 million attacks a year taking place against home computers, businesses and government systems in the UK, an offline website means a loss of income. For instance, PayPal reportedly lost £3.5m due to a cyber-attack in 2010.
As well as lost revenue, a website security breach can result in losing vital data, your reputation and even your ranking on Google. Ultimately, it could damage your business beyond repair.
Six simple tips to protect your site
Here are six simple but effective tips to protect your business against cyber attacks:
- Choose your passwords carefully. Password123 is not a secure password! Make sure passwords have at least eight characters and use a combination of letters and numbers. Here are some ideas for creating strong passwords.
- Install anti-malware and anti-virus protection for your website in the same way you would your PC. Reviews can help you determine if the product is right for your business.
- Use SSL to encrypt data. SSL provides a secure connection, protecting data sent between a customer’s web browser and your server. Your hosting provider can help set this up for you. Learn more about SSL.
- Avoid using wireless networks. If you must use them, make sure you're using the latest encryption standard, WPA2. This offers government-grade security.
- Keep programs and hardware up to date. This helps block malware that thrives in older equipment and out of date software. If you are using Windows or a Mac you can set up weekly update checks. You should also do this for any software you use to manage your website.
- Educate employees about the latest online threats. This way they’ll know clicking on bad links or opening dodgy attachments can compromise data. All your staff should be as vigilant at work as they are at home. If in doubt, don’t click it.
So, if website security wasn’t on your priority list, it might be time to add it now.
Guest post by Rahul Mistry, content writer for www.heartinternet.co.uk. You can follow Rahul on Twitter and Google Plus.
When does a big smart phone become a phablet?
Smart phones are getting bigger. Clearly unhappy with the already-really-rather-large size of its new Galaxy S4 (whch has a 5" screen), Samsung recently announced a new even-more-ginormous phone.
Yes, the forthcoming Samsung Galaxy Mega (check out the name) has a massive 6.3" screen. It's a phone that is, frankly, ginormous.
To illustrate just how big it is, we've knocked up this diagram comparing it to an iPhone 5 and the Samsung Galaxy S4. The image isn't actual size, but it is to scale:
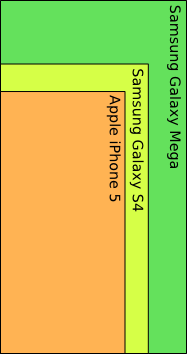
The trend towards larger displays on smart phones isn't a new one. It seems to reflect our desire to do much more with these devices than just make phone calls.
Larger screens are better-suited to watching video and playing games, as well as less-exciting functions like viewing and editing documents or making video calls.
But how big is too big? And at what point does a smart phone stop being a phone, and start being a tablet?
Finding a phoneIf you're in the market for a new mobile, it's worth checking all the main mobile networks for a good deal: |
Introducing the phablet
Well, some tech firms have pre-empted that question by creating an entirely new product category. I give you: the phablet.
Yes, really. Online seller Expansys even has a whole phablet category on its website. Phablets are a bit bigger than a typical smart phone but a bit smaller than your average tablet.
Tell friends or colleagues that you have a new phablet and they'll have no idea what you're on about, of course. But at least you'll know your new gadget has a name.
Phones, phablets, tablets ... who cares?
At the end of the day, as long as your phone / phablet / tablet does what you need it to, it doesn't matter what you call it.
But if you are shopping for a new smart phone, the diversity of screens available means it's important to check yours is right for the job. For instance:
- Is it big enough to easily read text on the screen?
- Is it small enough to fit in your pocket or bag?
- Can you use the phone comfortably with one hand?
If 6.3" isn't enough for you, there's no word yet on whether Samsung has any larger handsets planned. But it does seem unlikely, as there's already a wide range of 7" tablets on the market. These include the firm's own Galaxy Tab, the Amazon Kindle Fire and the cheap-as-chips BlackBerry PlayBook.
TOTW: how to remove comments from a Word document
 If you've been working on a Word document in a team or have to send a report out for comments and approval, you may end up with a file that's covered in comments, tracked changes and markup.
If you've been working on a Word document in a team or have to send a report out for comments and approval, you may end up with a file that's covered in comments, tracked changes and markup.
You'll probably want to remove the markup and comments from your Word document, particularly if you're sending it outside your business (tracked changes have embarrassed organisations many times over the years).
So, for this tip of the week (TOTW), we explain how to remove markup, comments and other hidden data from your Word documents.
Use the Document Inspector
IT dealsSee the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
Recent versions of Microsoft Word include a tool called the Document Inspector that helps you identify and remove comments, markup and hidden information. Bad news for Mac users though: the Document Inspector is only available on Word for PCs.
Here's how to use it:
- Open the document from which you want to remove comments and hidden data.
- Click the File tab in Word, then click Info.
(If you don't see the File tab, click the Microsoft Office button at the top left, then select Prepare > Inspect Document. This will open the Document Inspector, so you can skip step three.) - Select Prepare for Sharing > Check for Issues > Inspect Document.
- The Document Inspector will open. You can choose which items you want to check for. Make sure every box is ticked.
- Click Inspect. You may have to wait a moment if it's a large document.
- The Document Inspector will show all the comments, changes and data it has found.
- You can remove these items by clicking Remove All on each line.
Note: most of these changes cannot be undone. - You can rescan the document by clicking Reinspect.
- Click Close once you're done.
That's it. Now you can save your document as normal and send it out without worrying that it might contain any hidden text or information.
Business tech bargain: 37" Samsung HDTV for under £300
 Flatscreen TVs have all sorts of business uses. Many companies use them for presentations in meeting rooms, to show key statistics in the office, or to display corporate information in reception.
Flatscreen TVs have all sorts of business uses. Many companies use them for presentations in meeting rooms, to show key statistics in the office, or to display corporate information in reception.
This business tech bargain is the Samsung 37EH5000 37" Full HD LED TV, available from eBuyer for just £299.99 including VAT and delivery.
Prices have fallen massively in the last year or so, but £300 is still an excellent price for a 37" model from big-name manufacturer Samsung.
See details and buy online now >>
About this tech bargain
This Samsung 37" high-definition TV can be hooked up to computers and other devices via its two HDMI ports. These should work fine with any computer that has an HDMI or DVI connection (just make sure you get the right cable).
However, if you want to use it with older computers that only have a VGA connection, you'll need a VGA to HDMI adaptor too.
It's time to ditch the cloud
‘Cloud’ is one of the hottest IT buzzwords in years. Millions of people now make use of remotely delivered services – ‘cloud computing’, in the language of many IT firms.
But even the most popular cloud computing services such as iTunes and Google Mail haven't succeeded in educating the general public on how the technology behind these services actually works.
That’s fine when all you want to do is send an email or listen to music, but what happens if your needs are a little more specialised?
IT dealsSee the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
A low-cost alternative?
One of the undoubted benefits of cloud computing is its ability to deliver a low-cost alternative to many traditional business IT solutions.
But if people setting up a new company don't understand the principles of the cloud, are they really going to be aware of all it has to offer them?
More importantly, is the IT industry right to be so obsessed with the cloud as an overarching concept? After all, if you're launching a new business, your focus is going to be on the bottom line, not on some silly buzzword.
It’s about the service, not the delivery
So, instead of telling prospective customers a service will be delivered through the cloud, would it be a better idea for IT sales pitches - and the conversation in general - to focus on the merits of an individual service?
After all, few existing or potential small business owners are going to boast about the manner in which a service they used is delivered, but they will enthuse about something that works well and saves them money.
At Webfusion, we’ve created this infographic to show you the full extend of the public’s ignorance.
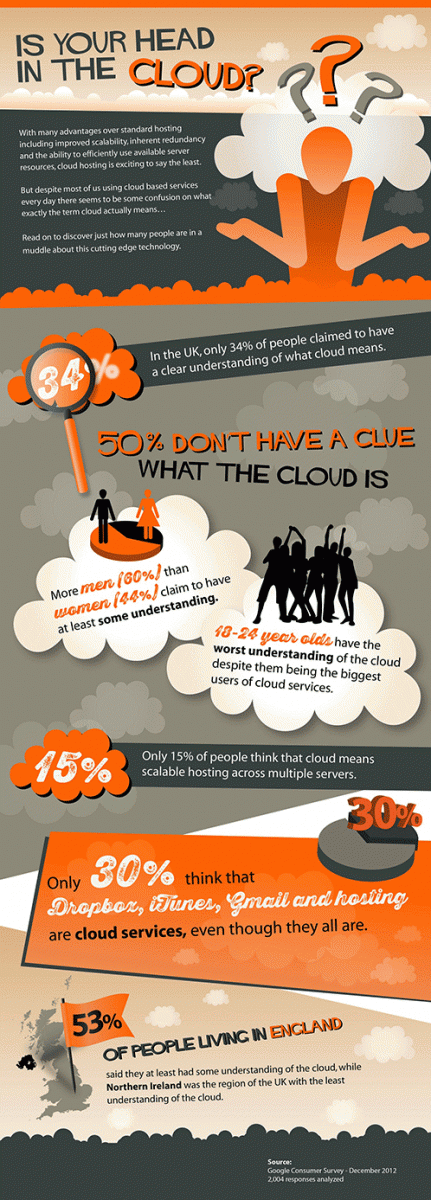
Infographic from Webfusion.
So what do you think? Is it time the IT industry stopped talking about the cloud, or does the term still have value?
People don't trust businesses with personal data (but hand it over anyway)
 One in four consumers don't trust any company to secure their personal information online. That's according to a survey of 1,000 UK consumers conducted by information security and risk management firm Integralis.
One in four consumers don't trust any company to secure their personal information online. That's according to a survey of 1,000 UK consumers conducted by information security and risk management firm Integralis.
Although a quarter of all respondents said they don't trust any organisation to take care of their personal data online, there is some relatively good news in one sector: nearly 65% of people said they do trust banks with this information.
However, businesses operating in other fields need to do more to win the trust of their customers. Only 36% of people trust online retailers with their personal data, 24% trust supermarkets and just 22% trust online payment systems like PayPal.
No trust, no problem
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
But despite this general lack of confidence, people still use these services in droves. For instance, over half of people surveyed said they do grocery shopping online at least once a week. While people might not trust online retailers with their data, they're still willing to share it.
"Online shopping is unbelievably popular, even though people don't necessarily trust it," confirms Mick Ebsworth, information security consulting practice director at Integralis. "People are worried about the types of information these site sask for."
"Far too often, consumers are prepared to supply core personal details - like mother's maiden name or date of birth - to organisations that don't need that information."
This can put consumers at increased risk of ID theft, should that information fall into the hands of online criminals.
"People need to always think about the information they provide," explains Ebsworth. "Does an organisation need it? Your bank might not be attacked, but your account at another site with lower security might be. So why use the same passwords?"
Don't ask if you don't need it
Although consumers might be making mistakes by supplying personal information to firms that don't need it, the buck really stops with the organisations requesting it. If they want potential customers to trust them more, they need to be more circumspect about requesting information.
Ebsworth has some advice for online businesses: "Firstly, you need to put in place the technical controls to keep personal information secure. You need the right level of encryption and good levels of data storage. Think about who has access to that information - in your organisation, with third parties, and online."
"Secondly, only request information that you really need. Recognise that the consumer has a role to play here, but that you can help them."
Finally, he has a sober reminder for firms that might still be unconcerned about how they handle this data. "Everybody who collects personal information has a duty to take care of it. Although there's nothing in the law to say how you should deal with a data breach, the Information Commissioner's Office can levy big fines if they believe you haven't adhered to good practice."
Does your business need all the information it collects from customers? Do they trust you to take care of it?
Business tech bargain: solid state storage deal
 Solid state drives (SSDs) are superfast replacements for traditional computer hard drives.
Solid state drives (SSDs) are superfast replacements for traditional computer hard drives.
Because they rely on flash memory instead of spinning magnetic disks, they have no moving parts and can access data more quickly.
Switching the standard hard drive in your laptop for an SSD can lead to impressive performance improvements. The only problem is that SSDs tend to cost a bit more than an equivalent hard drive.
Having said that, prices have dropped in recent months, and we've just spotted a great deal: currently, you can grab a 500GB Samsung SSD for £249.99 over at Dabs.
That's a good price. But as long as you buy before 15 May, you'll be able to claim £40 cashback, bringing the effective price down to £209.99. Now that is a tech bargain!
About this tech bargain
This Samsung SSD holds up to 500GB of data, which should be enough for general business use. In fact, it's very generous in SSD terms, and will give you space for an awful lot of music and a fair few films too, making it a good all-round option.
It's a standard-size unit which will slot straight into most laptops in place of the existing hard drive. It comes with all the normal fittings you might need, plus software to help you move your data across.
Replacing your laptop's hard drive with this should lead to noticeable performance improvements, particularly when it comes to starting your computer up, opening software and working with large files.
Don't panic, but 23% of your staff are stealing from you

If dodgy employees all looked like this, they'd be easy to spot.
A staggering one in ten employees has stolen important data from their employer after handing in their notice, reveals a new study from IT security specialist LogRhythm.
It seems that downloading a company's customer database onto a USB stick or copying crucial documents to CD is much more common than you might have thought. Of the 2,000 employees studied, the survey found that a massive 23% had taken confidential data from their workplace.
Often, people steal client details or product information in the hope that it'll give them a head start with their new employer. But 14% of people who admitted taking data did so to help set up their own rival company. And 23% did it out of revenge, because they felt undervalued and poorly treated.
Employers know the problems
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
Clearly, anyone stealing data from their employer is in the wrong. But that doesn't mean businesses should make it easy for employees to get their hands on the good stuff.
This research also surveyed employers, 47% of whom said they don't have any system in place to stop staff accessing confidential information or taking data.
So, all-too-often it's lax security and a lack of concern that makes it easy for staff to walk away with crucial company assets.
Worse, 60% of employers said they never change passwords or access codes, which is a little like leaving the door wide open for former employees to come and grab what they like.
You wouldn't let a staff member keep their keys to the office after they've left, so why would you let their passwords keep working?
Are you at risk?
If this survey is at all representative, there's a good chance your business is at risk of data theft. So, what are you going to do about it?
- Restrict data access. Sensitive data like customer information should only be available to employees who absolutely need it. It should never be sent by email or stored in shared locations.
- Close user accounts promptly. If a member of staff has been sacked, close their network account immediately and revoke all their access rights.
- Don't share passwords. Shared passwords are the enemy of good security. Not only can people continue to use the password once they've left, but it's also much harder to tell who's been accessing the data.
- Rotate access codes regularly. If you have a PIN-entry system for your building or a wireless network with a password, make sure you have a system to change them regularly - probably every month.
Finally, there's an aspect to this that leaves a nasty taste in the mouth. The research found 53% of people who've stolen data use it to get a head start in their next job, or to impress their new boss.
If the new employer decides to make use of that data, what sort of message does that send? And do they really think that employee isn't going to do the same to them when the time comes?
In short: if you've ever benefited from a data theft, don't be surprised if you end up suffering sometime too.
Five things 4G will do for your business
 4G, the new mobile technology that allows for superfast mobile internet connections, is just beginning to have an impact on the UK telecoms market.
4G, the new mobile technology that allows for superfast mobile internet connections, is just beginning to have an impact on the UK telecoms market.
However, although 4G has been talked about for several years now, many people are still in the dark about what it’ll do for their businesses. That’s why we’ve compiled these five key benefits:
- It lets you do more on the move.
- It’ll make remote working easier.
- It could cut your costs.
- It may boost your productivity.
- It’ll increase your mobile sales.
The key thing about 4G is that it really boosts the connection speed for mobile devices. That means you can do more on the move.
In fact, some 4G connections should offer speeds comparable to or faster than fixed-line broadband, which means tasks like working on shared documents, videoconferencing and more all become practical.
How to get 4GEverything Everywhere is the only company currently offering 4G mobile. It covers major UK cities. EE is the same company as T-Mobile andOrange, so if you have a mobile contract with them you may be able to move to 4G even if you're within your minimum contract period. O2 and Vodafone promise preferential 4G upgrades to some customers once their 4G networks become available later this year. |
Experts predict that 4G will eventually cover up to 99% of the UK population, which means even people living in rural areas will have a connection that’s fast enough to make remote working practical.
4G costs will drop as more mobile networks launch their 4G services. But 4G could trigger big savings in unexpected areas. As more employees are able to work remotely, you may find you can move to a smaller office or reduce your power bills.
4G will make it more practical to hold online meetings and use collaboration tools smoothly, which could result in less time spent travelling to meetings (and more time spent working).
Your customers will be using 4G too, which means they’ll find it easier and quicker to browse your website. That’ll encourage them to buy products on the move (if your website works well on mobile devices), increasing your sales.
Ultimately, 4G is an engine for economic growth. It’ll bring wide benefits helping companies to grow and encouraging investment in businesses from both the UK and abroad.
Business tech bargain: get £50 off a MacBook Air
 Apple's MacBook Air has been enormously successful, and still sets the standard for on-the-go computing.
Apple's MacBook Air has been enormously successful, and still sets the standard for on-the-go computing.
This business tech bargain sees you get a decent-spec MacBook Air for £50 less than usual, which is pretty good given how hard it can be to get money off Apple products.
For £879.99 you can buy an 11" MacBook Air from Zavvi. That's £50 less than the cost of an identical model bought from Apple itself.
This thin, light laptop includes a relatively powerful Intel i5 processor, 4GB of memory and 128GB of storage, which should be more than enough for most mobile workers.
See it now on the Zavvi site >>
About this tech bargain
The MacBook Air has been widely lauded as one of the best ultraportable computers around. It's small and light enough that you can slip it in your bag just in case you think you might need it.
The battery lasts for hours and yet it's powerful enough to get proper work done. It's also built to a very high standard, with a bright screen, responsive trackpad and positive keyboard.
TOTW: shortcuts to help you use PowerPoint professionally

Giving a presentation can be nerve-wracking. And let's be honest: although PowerPoint is a useful aid, many presenters rely on it too much.
But once you've made sure you're not committing any crimes with PowerPoint, here's a tip of the week (TOTW) with some useful shortcuts to make your presentation run smoothly and professionally:
Presentation gearThe right equipment can go a long way to ensuring a smooth presentation. You might need: |
Move through your presentation
Most people who use PowerPoint will know this already. However. if you tend to flail with your mouse to move through your presentation, why not try using the left and right arrows keys instead?
Tap these to step through your presentation one slide at a time - forwards or backwards.
Alternatively...
For a more professional look to your presentations, consider using a presentation remote control. This will allow you to step through presentations without having to stay by your computer. Kensington and Targus both make good models.
Presentation booksPresentation technique matters just as much as the kit you use. Why not get advice from these great books?
|
How to take a break
If someone interrupts your presentation unexpectedly, or you want to hold a group discussion without the distraction of what's on screen, use these shortcuts:
- Tap W to turn the screen white
- Tap B to turn the screen black
Just tap the key again to resume your presentation.
Scribble on your slides
You can literally underline a key point in PowerPoint, by drawing on the screen:
- Press CTRL + P to turn your mouse pointer into a pen icon
- Then click and hold the mouse to draw on your slides
- When you're finished, press CTRL + A
(If you use a Mac, tap the Command key instead of CTRL.)
Alternatively...
You can use a laser pointer to point at key items. These are available for a few pounds - just be careful not to point it in anyone's eyes!
The end is near for Windows XP

The end is nigh for Windows XP
If your business is one of the millions still using Windows XP, it's time to start thinking about moving to a more modern operating system.
Actually, you can consider this your early warning that Microsoft will be ending support for Windows XP in just under a year's time, on 8 April 2014.
After that date, Windows XP will no longer receive software updates from Microsoft.
That means no more security patches to protect you from viruses, spyware and hackers. No more fixes for software bugs. And no more updates to improve performance and stability.
Windows XP: 11 years and counting
Upgrading WindowsIf you're using Windows XP, you can upgrade to Windows 7 or Windows 8. It's a good idea to discuss the options with a reputable IT supplier. You can purchase Windows from these outlets: |
If you keep using Windows XP after 8 April next year then it will keep on working, probably. But the longer you keep using it, the greater the risk you'll be running.
The truth is Windows XP is more than 11 years old. Business technology has changed immensely in that time, and you're still reliant on this outdated software then you'll be doing yourself a real favour by upgrading.
If your computers are under three years old then you should be able to upgrade them to a more recent version of Windows without needing to invest in new computer equipment.
If your computers are older than that, then you might benefit from investing in new hardware at the same time.
Have the conversation now
In either case, it's worth discussing the issue with your IT supplier or support company now, so you have an idea of what you might need to do over the next few months.
You'll probably be presented with the option of upgrading either to Windows 7 or 8.
Windows 7 is a couple of years old and has been tried and tested in companies of all sizes. Windows 8 is the newest version, but has a revised interface that takes a little getting used to.
Which option is right for you will depend on the compatibility of your existing software, and your own preferences.
Don't panic though - you're hardly the only business out there still using Windows XP. Some statistics suggest nearly 40% of businesses are still are using the venerable software, with many experts expecting most of these companies to choose Windows 7 over Windows 8.
Do you still use Windows XP? Are you worried about the end of support?
Can you spot the phishing website?
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
You've probably heard of phishing. It's where scammers send you an email that looks like it's from an official organisation, usually your bank.
The email usually contains links to a fake log in page which collects your username, password and other security details. If you enter them, the scammers will subsequently use your credit card, empty your bank account or commit some other crime against you.
Some phishing websites are laughably bad, with terrible grammar, bad spellng and shonky design. But others can be very convincing.
Spot the phishing site
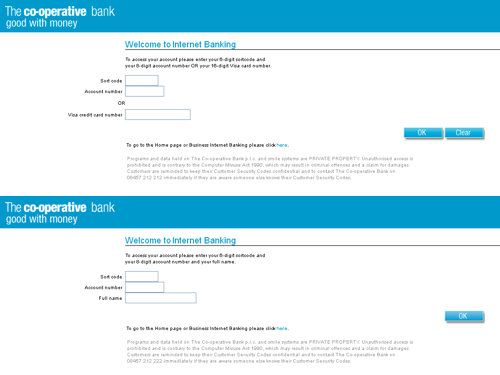
To show you just how convincing phishing sites can be, here are two screenshots for you. One is the genuine sign in screen for the Co-operative Bank's online banking service. The other is a fake sign in screen from a phishing email I received.
You can click the image to see both screens full size. Can you tell which is which?
So, how did you do?
Well, the top screenshot is of the genuine sign in screen. The second one is the fake.
If you're familiar with this bank's online interface, you'll probably realise that the site asking for your full name is not genuine. But if you don't use your online banking often or simply aren't paying 100% attention when you click the link, it's easy to see how you could be fooled.
Three principles to avoid phishing
Checking the address of a site like this is usually the most foolproof way to see if it's fake. In this case, it was easy to tell, because the URL clearly wasn't the Co-operative's normal address:
![]()
It isn't always as obvious as this through, so here are three foolproof ways to avoid phishing traps:
- Don't click sensitive links in emails. If an email from a trusted source like your bank asks you to log in to your account, do so by manually typing in the website address rather than clicking a link.
- Pay attention to security notices. Most phishing emails will be caught by email filters, security software or web filtering tools. If you see a warning about an email, link or website, don't ignore it. (It's amazing how many people do.)
- Let the sender know your concerns. If you're in any doubt at all about whether an email or website is genuine, get in touch with the organisation it claims to represent. A quick phone call should be enough to confirm your doubts.
And as a final warning, don't ever enter sensitive log in information if you have any concerns at all about the website you're on. Even if it just looks or feels a bit funny, that's reason enough to stop and think before you make a mistake.
Note: don't click links in dodgy emails like we did. They can be dangerous, even if you don't enter in any sensitive information.
Business tech bargain: Logitech speaker dock
 If you want to keep your office nice and quiet, this might not be the business tech bargain of your dreams.
If you want to keep your office nice and quiet, this might not be the business tech bargain of your dreams.
However, if you like to play a bit of music on a Friday afternoon or operate a stockroom, shop or other premises where background music is appreciated, this bargain Logitech rechargeable speaker dock for your iPhone / iPod might be just the ticket.
It's currently available from Amazon for just £47.
About this tech bargain
This Logitech Rechargeable Speaker S715i plays music from your iPhone or iPod, while simultaneously charging your device. You can also play music from other sources via the aux in port.
It comes complete with rechargeable batteries, which allow you to operate it when you're away from a mains power supply (although the volume does go louder when it's plugged in).
This tech bargain gets excellent reviews on Amazon and comes with a power adaptor, travel case and remote control.
At £47, it's by far the lowest price we can see it available for (the next cheapest seems to be Play.com, at about £70). We wouldn't be surprised if it sells out quickly, so see full details and buy online now.
Google, please stop messing with things that work fine
I'm a long-time user of Google Mail. By and large, I think it's brilliant.
The enormous amount of storage space means my email archive contains thousands of messages going back over half a decade. I can log in from anywhere and find exactly what I need in moments.
Making Gmail worse
But last October the search giant started testing a new interface for writing messages. Now it's decided to roll it out to all users. And, unfortunately, it's a backward step.
The old interface might look rather traditional, but it does the job well:
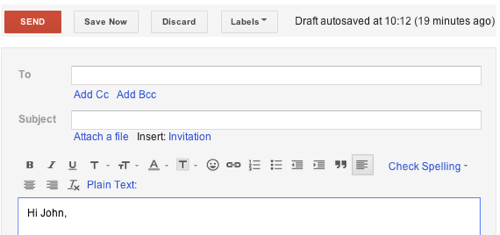
The line of icons across the top ensures you're never more than one click away from inserting bullets or links, indenting text, changing formatting or running the spell check.
Contrast that with this new, cleaner interface. When you start writing an email, this pops up over your inbox:
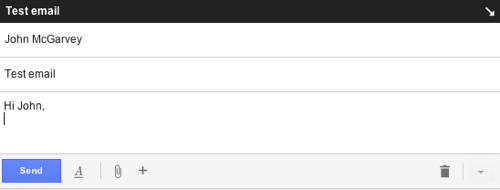
With icons stripped from the interface, it takes more clicks to find functions that were previously obvious:
- To add bullets or change text formatting, you must click the underlined A to show formatting options. A second click picks the option you want. That's twice the clicks it took before.
- It works differently when you want to add a link or emoticon. There's no extra click, but you have to run the mouse over the + symbol to reveal the option you need.
- The process for finding the spellcheck is different again. First, you have to click the non-descriptive down arrow at the bottom right. Then choose Check spelling from the list. Once again, what previously took one click now requires two.
Google says the new interface is faster and more focused. I contend that having to think harder about how to insert a bulleted list or embolden text is almost certainly going to break your focus more effectively than the old icon toolbar did,
Besides, the new interface keeps your inbox visible behind it, so you can see new emails as they arrive. That won't be distracting in the slightest, will it?
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equipment now from these trusted suppliers: |
Your email matters
The way email works is important because we spend so much time using it (more than a quarter of the average day, according to some research).
When companies alter services like these that we're comfortable with and rely on, it can make us less efficient, change our working practices and make us feel uneasy.
That's the way I'm feeling at the moment. And that's why I'm irritated by Google's unneccessary tinkering and arbitrary changes. Maybe it's time I switched to Microsoft Outlook instead.
TOTW: three ways to avoid online scams

Last week's enormous denial of service attack highlighted the problem of badly-secured internet devices.
Looking for a deal?See the latest business tech bargains we've found online. Or buy IT equpment now from these trusted suppliers: |
So, for this IT Donut tip of the week (TOTW), we thought we'd remind you of three elementary security precautions.
1. Take care of personal details
There's been a Facebook post doing the rounds asking people to post their 'porn name'.
Depending on who you believe, the answer to this hilarious joke is a combination of things like your mother's maiden name, your middle name, the name of your first pet or the name of the street you grew up on.
These answers - and those to other similar games - often include information used for online security checks. So, always be very wary about revealing it to anyone. Their motives could be more sinister than you think.
2. Make sure your bank is your bank
Phishing schemes have been around for years, but as they're still going strong then they must keep catching people out.
So, if you receive an email purporting to be from your bank, be suspicious, especially if it asks you to reply with sensitive information (like card or security details) or directs you to a website that collects this information.
In fact, if you're in any doubt about the veracity of an email from your bank, give them a call to check. And instead of clicking links in the email, visit their website by typing the address into your web browser.
3. Use different passwords for key services
Make sure your email password is different to your Twitter password and your online banking password.
There have been a rash of high-profile password leaks over the last couple of years, and there'll be more in the future. Some hackers try using leaked passwords to log into other services. So, keep your passwords unique to stay secure. Get help creating unique passwords you can remember >>
Business tech bargain: pre-order the new Samsung Galaxy S4
 Samsung's latest, greatest smart phone, the Samsung Galaxy S4, is now available to pre-order. If you can't wait to get your hands on this impressive mobile phone, then now's the time to place your order online.
Samsung's latest, greatest smart phone, the Samsung Galaxy S4, is now available to pre-order. If you can't wait to get your hands on this impressive mobile phone, then now's the time to place your order online.
You will, unfortunately, still have to wait until the phone's official release. But over at Carphone Warehouse, if you order today you can expect delivery on 26 April, which is the day the new handset becomes available.
Place your order online now >>
There's a wide range of tariffs to choose from, which could see you pay as little as nothing up front (you'll have to commit to a two-year contract, mind you) to £590 to buy the handset outright.
You'll also receive a free accessory bundle which includes a screen protector, flip cover, in-car charger and 32GB memory card.
About Samsung Galaxy S4 pre-orders
Samsung announced the Galaxy S4 at an event in New York last month. Some of the handset's key features include:
- Full high-definition screen, which isn't a first for a smart phone but does mean everything looks a little sharper.
- An eight-core central processing chip, that'll ensure this phone runs superfast (there's a large battery too, to allow for the extra power it'll consume).
- An NFC (near field communication) chip, which may - in future - allow you to pay for things by tapping your phone on a reader in shops.
- A 13 megapixel camera, offering excellent quality photos and videos.
As with other Samsung smart phones, the Galaxy S4 will run Google's Android operating system, which means buying one will give you access to an enormous library of free and paid-for apps. It also includes 4G capabilities, ensuring you can use it on EE, currently the UK's only 4G network.
For all that, this phone isn't a vast leap forward over the company's existing S3. It's more of a careful evolution - which should still position it as one of the best smart phones on the market today.
To be sure of getting your hands on one, place your pre-order now.
Free competitive analysis tools for your business
 You can use tools like Google Analytics to see how visitors interact with your website. But that’s just a drop in the ocean in terms of competitive analysis.
You can use tools like Google Analytics to see how visitors interact with your website. But that’s just a drop in the ocean in terms of competitive analysis.
If you’re running a small or new business, there are some excellent, comprehensive and free competitive analysis tools that can provide valuable data to help you understand your market.
Business tech dealsWe scour the web to find you the best business tech bargains. |
You’ll need to be willing to put a bit of time in to learn how to get the most from these free competitive analysis tools. But if you do, you’ll be rewarded with information to help your business succeed.
Competitive analysis for due diligence
You don’t have to pay to view Companies House accounts if you can download them already for free online. That’s where competitive analysis tool Duedil comes in.
Short for ‘due diligence’, it’s an excellent tool that provides free business intelligence such as insight into competitors, suppliers, investors and clients.
You can also use it to benchmark a business’s performance and growth over time, build sales leads and integrate social networks such as LinkedIn.
Competitive analysis tools beyond Google
Google Analytics and Google Trends are good free competitive analysis tools because they’re integrated with the most popular search engine in the world. It means you get data ‘right from the horse’s mouth’.
But it’s a good idea to go beyond Google to get deeper insight into your website’s analytics. Comparing data sets can help you avoid sample biases that come about from opt-in panels or toolbars, giving you a more accurate picture of how your audience is behaving in response to your marketing efforts.
For example, have a look at the free competitive analysis tools from SEOmoz.
Using Facebook for competitive analysis
Search engines are constantly learning more about how people categorise and search for information. A big part of the mix in recent years has been social media, which search engines now indirectly recognise and attribute authority to.
In other words, it’s important to use and understand social media to reach your audience, and watch and learn from competitors too.
Anaylse your social media efforts using tools like FeedCompare, HootSuite, SocialMention and Google Alerts.
Competitive analysis doesn’t need to be expensive and complicated. As long as you’re willing to work at it, you can get valuable insight on your partners, suppliers, clients and customers … and get a step ahead in your business.
- How democratising data can benefit your business
- Business benefits of web analytics
- Coping with growing data storage needs
Helen Major has a keen interest in finance and has been writing for blogs and newspapers on the subject since she graduated from the University of Edinburgh in 2007. She is currently writing on behalf of Duedil, a free Company House and directors’ search database.