Posts for September 2014
Why new software isn’t always better software
 |
|
Image: Twin Design / Shutterstock.com |
Apple released iOS 8 recently. Demand for this new version of its mobile operating system was so high that UK internet traffic surged as people rushed to download it.
Yet shortly after it became available, a number of tech pundits cautioned owners of older iPhones against upgrading.
Specifically, people who own the iPhone 4S were warned that the new operating system could cause everything to slow down.
Don’t be an early upgrader
This high-profile upgrade perfectly illustrates a question that’s faced businesses time and time again: should we upgrade our software now, or should we wait?
Software companies rely on big releases to give them a revenue boost. That’s why Microsoft throws the full force of its marketing machine behind each new version of its Windows and Office packages.
It’s nothing new — when Windows XP came out in 2002, they even got Madonna involved. But if the history of software upgrades teaches us anything, it should be that it’s usually best to wait.
People don’t like change
There are lots of reasons to hold off installing a new version of software your business depends on:
- People don’t like change. Software companies often move things round when they release a new version of an old package. Even if this change is obviously for the better, it can infuriate your staff if they’re used to the old way of doing things. Just look at the reaction when Microsoft introduced its Ribbon interface with Office 2007.
- New software often has bugs. It’s impossible to create a complex piece of software with no bugs. And often, major new releases are when serious bugs emerge. Give it a few months and you’ll find the software’s much more stable. Take Windows Vista, which was so full of bugs on release that its reputation never really recovered.
- Your current package has life left in it. Although a newer version might be available, most software companies will continue to provide support and updates for older versions of software. For example, although Windows XP was released in 2002, Microsoft only stopped supporting it this year.
So, even if you’re dazzled by the promised benefits of a new piece of software, it’s nearly always worth stopping to think before you plunge in and upgrade.
That’s just as true if you’re paying a monthly subscription for software that includes access to upgrades. In the short term, it might still be better to stick with the old version.
(It’s worth noting we’re referring to major, paid-for upgrades here, rather than the free security updates and patches that software companies release much more frequently. You should install these promptly to protect your data.)
What to think about
Before you upgrade any software, stop and think carefully. Here are five key things to get your head round before you upgrade everyone in your company:
- What are the reviews like? Search online to find out what experts think of the new software. Check review websites and comments on sites like Amazon, too. These are a great way to find out how real people are finding the software in the real world.
- How urgent is the upgrade? Find out when support will end for the software you currently use. Although there’s usually a decent buffer, some software will require you to upgrade sooner. For instance, you might have to upgrade your payroll software to access the latest tax tables.
- What are the benefits of upgrading? Occasionally, upgrading software can transform your business. For instance, companies are increasingly building online features into traditional software, making it easier to share data. If the benefits are clear, it might be worth upgrading earlier.
- Can you test it first? Rather than inflicting the new version on all your staff at once, you can roll it out to a few people and see how they find it. This will also help you identify any issues that are specific to your company.
- What does your IT supplier say? Forget asking the software company. They’ll tell you to upgrade. But if you work with a good IT supplier, they can help you understand the likely benefits — and potential risks — of upgrading. With their help, things will go more smoothly.
Finally, don’t assume that blindly upgrading is the best option for your business. Recent years have seen the software landscape change dramatically.
Cloud computing services are capturing an increasing slice of the software market. In some sectors, these innovative services are a great alternative to traditional desktop software.
If you think you’re due an upgrade, it’s the right time to investigate the alternatives and see if there’s anything better out there.
IT for Donuts: how to check your Twitter user statistics
IT for Donuts is our regular weekly feature where we explain a tech term or answer a question about business IT.
This week, we reveal how to check your Twitter user statistics. Since Twitter opened up its stats pages to everyone, this is easier than ever.
Your Twitter user statistics
There are lots of reasons to check your Twitter user statistics. If you’ve been making a concerted attempt to market your business through Twitter, they can help you understand how well you’re doing.
And even if your business doesn’t have a serious social media strategy, Twitter user statistics can still show you how your tweets are doing.
Even if you do nothing else, you can check them today, then have a look again in a month’s time. That’ll give you some idea of whether you’re using Twitter efficiently.
How to check your Twitter user statistics
Accessing Twitter user statistics used to be a bit of pain. And once you managed to get into them, there were still some doubts over the accuracy of the figures.
Nowadays, it’s easy to see your Twitter statistics:
- Sign in to your account on the Twitter website
- There’s no obvious link from your Twitter homepage to your user statistics, so just go to http://analytics.twitter.com.
- If you see the Twitter analytics home page, select the Sign in with Twitter button.
- Now you should see a page showing your Twitter user statistics. It’ll look something like this:
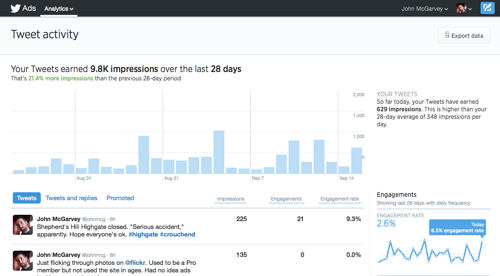
What your Twitter user statistics mean
Here’s a little information to help you interpret your Twitter user statistics screens.
- The graph at the top of the page shows the number of impressions your tweets have received in the last 28 days. An impression is recorded each time one of your tweets appears in another user’s timeline.
- Beneath the graph is a list of your tweets, with statistics for each. Engagements are the number of times users have interacted with the tweet — like by clicking it, retweeting or following you.
- Select any of the tweets to see detailed statistics on it. You’ll see impressions over the first 24 hours, clicks, retweets and more. The graph paints an interesting picture of how quickly tweets lose can lose attention:

- Finally, on the right of the screen you’ll see some smaller graphs, showing trends for things like engagement, clicks on links in your tweets, retweets and so on. These provide a good overview of how your recent tweets compare to older ones.
Your Twitter user statistics can give you a good feel for how your tweets are performing. But don’t see them as the be all and end all.
Twitter isn’t simply about reaching as many people as possible. It’s about reaching the right people, and really connecting with them.
Previous IT tips:
Do your ex-employees keep logging in?
 When an employee leaves your businesses, are you letting them walk out with access to valuable company data?
When an employee leaves your businesses, are you letting them walk out with access to valuable company data?
According to the 2014 Intermedia SMB Rogue Access Study, 89% of employees who leave a company retain access to business or cloud applications like Salesforce, PayPal, email and SharePoint.
That’s a scary figure. We’ve written a lot about IT security lately, but statistics like this make us think that this level of coverage is warranted.
When a member of staff leaves your business, you must have a way to revoke their access to all your resources. Failure to do so just invites disaster.
Ex-employees are actually signing in
Of those people questioned for the research, 49% had actually signed in to an ex-employer’s account, despite having left the company.
Most of these people probably act out of curiosity, rather than malice. But they still have access to apps that may contain important company data.
A minority will almost certainly be intending to do harm to their former employers. It only takes one person to cause you all sorts of problems.
You could be looking at hefty reputational damage, a loss of competitive advantage — or even a big fine from the Information Commissioner.
Security begins at work
“Most small businesses think ‘IT security’ applies only to big businesses battling foreign hackers,” says Michael Gold, president of Intermedia.
“This report should shock smaller businesses into realising that they need to protect their leads databases, financial information and social reputation from human error as well as from malicious activity.”
You can start by putting some proper procedures in place to control and revoke access when employees leave your company. These are some good starter tips:
- Record who has access to what. You can’t be sure you’ve revoked everything unless you know what each employee can access. If you rely on apps with separate usernames and passwords, it’s particularly important to keep an up-to-date list of who has access to what.
- Don’t share usernames and passwords. Some cloud services charge extra for each user, so it’s tempting to have one generic username and give everyone access. Bad idea: every employee who leaves will know the username and password.
- Have an ‘offboarding’ process. You probably have a standard procedure for when people join your company. But do you have a similar set of steps to follow when someone leaves? If not, it might be an idea to put a checklist together.
It can be trickier than you might expect to get a handle on who has access to what in your business. However, once you do so, you can be more confident of retaining control over your most important data.
IT for Donuts: shortcuts to move windows easily
 IT for Donuts is our regular weekly feature where we explain a tech term or answer a question about business IT.
IT for Donuts is our regular weekly feature where we explain a tech term or answer a question about business IT.
This week, learn some Microsoft Windows keyboard shortcuts that help you move application windows around the screen. These are particularly helpful if you use more than one screen with your computer.
These shortcuts work in Windows 7 and 8.
Move a window to the left or right
If you’re working in a window but want to show another window alongside it, a simple shortcut will ‘tile’ that window to the left or right of your screen.
This means the Window will snap to the left or right of the screen, and resize itself to take up half of the width of your monitor. You can then move another window into the space next to it.
To make your window ‘tile’ in this way, Hold down the Windows key (it’s the key in between Ctrl and Alt on the left side of your keyboard) and tap the left or right arrow keys.
Move windows between monitors
If you have two monitors connected to your computer (like in the image, above), there’s another easy shortcut to move windows between the two monitors.
Hold the Windows and shift keys together, then tap the left or right arrow keys. This will move the window to your left screen or right screen.
Weird wearable tech that's much stranger than the Apple Watch
Just over a week ago, Apple presented its new smartwatch to the world. This computer-on-your-wrist is Apple's first new type of product since the iPad. It'll be interesting to see if it has the same impact.
Wearable technology has been lauded as 'the next big thing' for a while. For instance, Google Glass went on sale in the UK earlier this year. And in March, a wearable technology show took place in London.
The Apple Watch might be the most mainstream piece of wearable tech yet. But that simply highlights the fact that plenty of strange gadgets have gone before it. Here are five of the most unusual:
1. Drumpants. (Yes, drumpants.)
Easily the most ridiculous pair of jeans we've ever seen, these trousers double up as a drumkit.
Well, to be precise, they're a set of electronic pads that you can wear under your clothes. When you tap them, they make noises. Prices start from $99 for a basic kit.
2. eBay's USB bracelets

Have you ever felt the urge to wear a USB cable on your wrist? Last year, eBay teamed up with the Council of Fashion Designers of America to create bracelets that also work as USB phone chargers.
Practical? Almost certainly. Fashionable? Well, would you wear one?
3. Panasonic's barely-noticeable wearable camera
Just check out how cool Brazilian football star Neymar looks wearing the Panasonic HX-A500 camera. You barely notice it's there:
Actually, this camera can go underwater and shoots at the latest 4K resolution (that's much better quality than your high-definition TV). So while it might not be subtle, it could be useful to extreme-sports fans.
4. Virtual reality

Virtuality image by Dr. Waldern/Virtuality Group (Dr. Jonathan D. Waldern), via Wikimedia Commons
Back in the 90s, one of the coolest ways to spend your time was to take a trip to the Trocadero in London. There you could put on a Virtuality headset and dive into the world of Virtual Reality.
These days, the crowdfunded Oculus Rift is picking up the VR mantle. Watch this space, then...
5. A sweater that senses your mood
Hate expressing your feelings honestly? You'll be wanting the Ger Mood Sweater. It uses sensors on your hands to read your 'excitement level', then lights up the collar with colours that are supposed to reflect how you're feeling.
Yeah, whatever. This thing makes wearing even Google Glass seem pretty normal.
The myths and realities of cloud CRM

From multinational corporations to one-person businesses, it seems everybody’s moving to the cloud.
The numbers certainly confirm this trend: 69% of global data traffic will shift to new-style ‘cloud data centres’ by 2017, according to the Cisco Systems Global Cloud Index.
Customer relationship management (CRM) is at the forefront of the cloud boom. Up to 40% of CRM systems sold in 2013 were cloud-based, according to Gartner. So, if you’re still lagging behind, is it because you’re unsure about some aspects of the cloud?
If so, here are the four biggest myths about cloud CRM systems:
1. Your data won’t be secure
Small and medium-sized businesses often lack the internal resources to implement adequate security measures. However, the same companies are often concerned that the cloud will expose their data to greater threats.
Moving to the cloud does mean putting your faith in a third party. However, cloud providers are able to implement sophisticated firewalls, security protocols and data encryption. It’s unlikely that most smaller companies could protect an in-house system to the same level.
Learn more about cloud security >>
2. You can suffer uncontrollable outages
A survey conducted by Maximizer Software in 2013 revealed that 71% of small and medium-sized businesses fear outages and disruptions if they move to the cloud.
In reality, however, a large, dedicated service provider is much less likely to suffer breakdowns than a small, in-house IT department.
3. Small businesses can’t afford the cloud
It’s not just large corporations that can afford cloud technologies. Operating in the cloud can also cut costs for many small and medium-sized companies.
This is because no expensive infrastructure is required, security is largely handled for you — and costs for IT staff, power and maintenance are reduced.
4. The cloud means changing business processes
Many companies fear that moving to the cloud will affect their business for the worse. While it might take a little while to adapt to a new cloud system, over time it can pay dividends.
Improved collaboration, easier data access, convenient offsite working and new ways of tapping into business intelligence can all result from moving to the cloud.
So yes, you have to change some processes. But those changes should be for the better.
Of course, it pays to be cautious before adopting any new technology platform. However, sooner or later the cloud will become a reality for most of us. Why lag behind?
- How do businesses use cloud computing?
- How CRM and IT are moving to the cloud
- Six questions to ask about your new CRM system
Copyright © 2014, Mike Richardson, managing director for EMEA at Maximizer Software.
Simple protection from cyber criminals
 Last week’s celebrity hacking news showed just how easy it can be for hackers to gain access to sensitive or personal data.
Last week’s celebrity hacking news showed just how easy it can be for hackers to gain access to sensitive or personal data.
And you don’t need to be a well-known personality to be targeted by hackers. Many hackers target small businesses, because these companies are less likely to have invested in strong security measures.
Someone hacking or compromising your system could be your worst nightmare. But there are some simple ways to prevent it from happening. Here are some steps you can take to make your system safer.
1. Add another layer of verification
Two-step verification is a good way to add another layer of protection when staff log in to company systems.
Typically, two-step verification requires your staff to sign in with something they know (a password), plus something they have (often a one-time code that’s texted to their mobile phone or shown on a digital key fob, pictured).
Two-step verification provides significant extra protection, especially if your company uses its systems to store and share sensitive documents.
2. Use strong passwords
Most people know they need to use strong passwords. But most people still don’t do it.
Make it company policy to use strong passwords. Mixing uppercase letters, lowercase letters, numbers and symbols makes it much harder for someone to gain unauthorised access.
You can use password management tools — like 1Password or LastPass — to keep track of these hard-to-remember logins.
3. Don’t share your logins
Sharing usernames and passwords is a big no-no. If everyone uses the same details to sign in to your shared workspace, if something goes wrong then you don’t have an audit trail to a specific user.
It also creates potential risk when an employee leaves the business. They probably won’t do anything malicious, but are you willing to take that risk?
4. Encrypt important data
Encryption scrambles data so it can’t be read, even if a hacker gets their hands on it.
Windows 7 and Windows 8 both have encryption tools built in. There are plenty of other encryption tools available too —many are free.
Copyright © 2014 Ian Cowley, managing director at Cartridge Save.
IT for Donuts: stop loose wires sliding off your desk
IT for Donuts is our regular weekly feature where we explain a tech term or answer a question about business IT.
This week, are you forever having to locate wires that have slipped down the back of your desk? This tip might just change your life.
Losing laptop wires
If you work from your laptop, you probably have cables for a mouse, keyboard, monitor and power on your desk.
You might also have charging cables for your smart phone, tablet, and Bluetooth headset. Oh, and don’t forget your network cable.
That’s a lot of wires to keep track of. And if they slip down behind your desk, you can be faced with a nightmare tangle to sort out, just so you can plug in and charge up your phone.
The simple way to keep wires visible
If we’re honest, this tip has been posted on various advice websites before — most notably, Lifehacker. But it’s so simple and handy that it’s worth sharing again.
This picture — from the laptop stand on my own desk — tells the story:
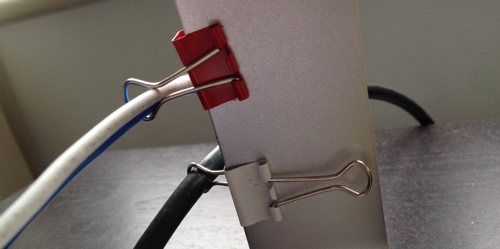
Yes, it’s that simple. Run the cables through the ends of a Bulldog clip or two (you might need to unclip them from the main meta springy bit), then clip them to a solid item on your desk — or to the desk itself.
You’ll never lose a cable behind your desk again.
Business questions from the celebrity iCloud hack
 |
|
Copyright: s_bukley |
You can’t have missed last week’s news that hackers gained access to intimate photos belonging to celebrities, including Jennifer Lawrence (pictured).
The story has raised important questions about what data individuals store in the cloud. Many of those questions have implications for businesses too.
After all, cloud services play a pivotal role in many companies. They’re used for all kinds of tasks, from backing up data and sharing files to enabling remote working and reducing the need for expensive in-house equipment.
The cloud certainly has significant advantages, and it’s here to stay. There’s a strong argument that overall, the security risks of using the cloud are lower than storing data in your own business.
But with cloud technology still developing, could this breach be the spark that forces cloud providers and their users to confront some key questions?
1. What’s your weakest link?
Although full details of the iCloud breach have yet to emerge, it seems likely the celebrities were victims of some kind of brute force or social engineering scam.
This means hackers used techniques to work out log in details, rather than exploiting a technical breach.
With cloud security, much of the focus is on measures systems like firewalls and backups. However, if all that stands between a hacker and your data is an easy-to-guess password (like ‘password’, ‘123456’, or your company name), that’s how criminals are most likely to access your data.
Our advice:
Strong passwords are important, and you should really combine them with two-factor authentication to up the security on your cloud accounts.
The biggest problem with strong passwords is that they’re a nightmare to remember. We recommend using password management software, like 1Password or LastPass.
2. Do you understand your cloud service?
An interesting piece from Wired argues that we’ll all benefit if some of the affected celebrities try to sue Apple over this case.
I won’t go into all the arguments, but one key point is we often start using cloud services without completely understanding what we’re getting into.
For example, Apple’s iCloud terms of service are over 8,000 words long. When you sign up, you agree to them, almost certainly without having read them.
As we use these services to store and share sensitive information, perhaps providers should make more of an effort to really communicate what they do to protect our data, and what we need to do, too.
Our advice:
If you don’t understand what a cloud service is going to do with your data, do further research before signing up. A local IT supplier might be able to help.
Don’t commit everything to begin with, either. Start by moving non-critical data to the cloud. You can shift more of your business across as you gain confidence.
3. Who can you talk to?
If you’re an A-lister, you can guarantee you’ll get attention when your cloud services get hacked.
But if you’re an ordinary business just trying to get on with work, are you confident you’ll get a response from your provider when something goes wrong?
Services like Apple’s iCloud and Google Apps are designed to be automated. You can sign up and start using them without having to speak to anyone.
Most of the time, they work flawlessly. But if something goes wrong and you can’t figure it out yourself, it can be hard to find someone to help with the problem.
Our advice:
Look for cloud providers that offer comprehensive support and have a good reputation. Search online for reviews and make sure they’re well established.
Often, a local IT supplier can help you find the most appropriate cloud services as well as providing support and help when you need it.
Blog by John McGarvey, editor of the IT Donut.
IT for Donuts: call 0800, 0808 and 0500 numbers free from your mobile
 IT for Donuts is our regular weekly feature where we explain a tech term or answer a question about business IT.
IT for Donuts is our regular weekly feature where we explain a tech term or answer a question about business IT.
This week, have you ever been stung by calling a ‘freephone’ number from your mobile phone? Although free to call from landlines, mobile phone companies often charge to call 0800, 0808 and 0500 numbers.
But there is a way round these charges. Read on and we’ll explain…
From your inclusive allowance
Ok, here’s the disclaimer. When you use this method to call freephone numbers, it’s not quite accurate to say that they’re free.
Actually, calls placed via this method will come out of the call allowance included with your mobile phone contract. So although most pay-monthly mobile phone users can benefit from following these instructions, proceed with caution if you’re on a pay-as-you-go deal.
All clear? Ok, here we go.
Use 0800Buster
To call an 0800, 0808 or 0500 number from your mobile without getting hit with a nasty surprise on your next bill, visit the 0800 Buster website.
On the left side of the screen, you’ll see some instructions about how to place a call. You’ll be given a number to dial which starts with 03.
Calls to 03 numbers cost the same as calling an 01 or 02 number, and must come out of any inclusive calls allowance.
When you call the number, you’ll hear a short message. Tap in the number you want to call, followed by the hash (#) key. After a moment, you should hear another ringing tone, before your call is answered.
That’s all there is to it!
More mobile phone tips
11 ways to keep hackers out of your wireless network
 Because wireless networks are simple to set up and generally work without needing constant adjustment, they’re easy to neglect. Yet for a hacker, your wireless network could provide the easiest route into your business data.
Because wireless networks are simple to set up and generally work without needing constant adjustment, they’re easy to neglect. Yet for a hacker, your wireless network could provide the easiest route into your business data.
It’s vital you protect your wireless network from unauthorised users. These 11 steps will help you lock it down and keep it safe.
1. Use WPA2 encryption
You probably know that you should protect your wireless network with encryption, so people can’t connect without entering a password.
But did you know that different levels of encryption offer different levels of protection? Make sure you use WPA2, which is the most secure option for everyday wireless devices.
2. Turn off guest networking
If you have a guest wireless network, there’s a good chance that it’s unsecured. This makes it easy for guests to get connected. But it also makes life easier for hackers.
Unless absolutely necessary, it’s best to keep guest networking turned off.
3. Change standard passwords
Many routers and other wireless devices share standard passwords. That means if you don’t change the admin password on your wireless router, hackers can break in by entering the standard password.
Change this to a strong password. Use a combination of upper and lower case letters, numbers and symbols.
4. Change the standard network name
The name of your wireless network is also called the SSID. Often, this is set to the make and model of your wireless router.
If you leave this as it is, the SSID helps hackers identify your router, so they can try standard passwords or break in via known weak spots.
5. Hide your network’s name
Most wireless routers allow you to turn off the ‘SSD broadcast’ feature. This means your wireless network won’t show up when people scan for networks.
Instead, they’ll have to know the network name in order to connect. And that gives you another layer of safety.
6. Track who is using your Wi-Fi
Most wireless routers maintain a ‘device list’ showing all devices that have been connecting to your network. Some will alert you when a new device connects.
Check this list every now and then. If it contains any devices you don’t recognise, always investigate.
7. Switch on MAC address filtering
Every wireless device — like your laptop, smart phone or tablet — has a unique ID called a MAC address.
When you turn on MAC filtering, you can tell your router which MAC addresses should be allowed to connect. If a hacker’s device isn’t on the list, they won’t be able to get in.
8. Isolate your devices
If your wireless router offers this setting, isolate the devices on your network. This means that although they’ll be able access the internet, they won’t be able to discover each other.
This provides another layer of defence. If a hacker manages to access your network, they shouldn’t then be able to reach servers, computers or other devices.
9. Keep firmware up to date
Firmware is the basic operating system that tells your router what to do. Like the software on your computer, it may need updating now and again — sometimes to fix security problems.
Although firmware updates are not released as frequently as software updates, it’s worth checking for them now and again.
10. Use firewall settings
Most wireless routers have some sort of firewall built in to protect your network from malicious attackers.
No matter how basic the firewall is, switch it on. It’s certainly better than nothing. If you’re in the market for a new router, perhaps pay extra for one with a more advanced ‘stateful protection’ firewall built in.
11. Use WPS with caution
WPS stands for Wi-Fi protected setup. It’s a simple way to connect new devices to a wireless network. All you have to do is press a button on your router, then connect your device.
However, a major WPS security flaw was discovered in 2011. As a result, it’s better to disable WPS and connect devices manually.
- Why every business need a wireless network
- How to work remotely and securely
- Five IT security mistakes you may be making
This post is by Adrian Case from Akita.
How to handle your post-holiday inbox
 We’re all familiar with that day of reckoning. It’s usually a Monday. You’ve probably been stuck in a traffic jam or on a full train on the way to work. And once you arrive, you have a two-week email backlog to get through.
We’re all familiar with that day of reckoning. It’s usually a Monday. You’ve probably been stuck in a traffic jam or on a full train on the way to work. And once you arrive, you have a two-week email backlog to get through.
Your post-holiday email can be demoralising, even if you did the right things to prepare before you went away. So, here’s a five-step action plan to help you deal your inbox while staying relaxed and in control.
1. Talk to people
Before you open your email, talk to your colleagues. If someone else was handling your workload in your absence, sit down over coffee and get them to sum up what’s happened.
That way, when you do delve into your inbox, you’ll have a better idea of what needs attention.
2. Sort by sender
You know who your most important contacts are, so sorting messages by the sender’s name is a good way to identify key messages.
But don’t rush to reply to messages immediately. First of all, move onto step three…
3. See the big picture
Skim through your inbox and identified the main priorities. Then handle the most important messages first. Use the ‘4Ds’ principle to take care of the highest-priority messages.
Either deal with an email immediately, delegate to someone else, delete the message or defer it. As you reply, make sure you’ve checked the whole email chain. Has anyone already answered on your behalf?
4. Address less important messages
Once you’ve applied the 4Ds principle to your most important emails, go back through your inbox and deal with second priority emails in the same way.
Many of these will probably be circulars that can be left for a while, or maybe even deleted. Be ruthless before replying and ask what your reply will contribute at this stage. Don’t waste your time — or that of your recipients.
5. After a week, delete everything else
Yes, it sounds drastic, but once you’ve been back at work for a week then any emails you haven’t yet dealt with will be well past their sell-by dates.
If — by some faint chance — you have missed something, you can be sure the sender will contact you again.
- Email overload is damaging productivity
- When it comes to email replies, is faster always better?
- How to sort out your email once and for all
Copyright © 2014 Monica Seeley. Monica is the founder of Mesmo and a leading expert on email best practice.
How Wi-Fi can be a marketing tool
 There’s a growing expectation among consumers that Wi-Fi should be available when they walk into a large retailer, shopping centre, hotel, café or other hospitality business.
There’s a growing expectation among consumers that Wi-Fi should be available when they walk into a large retailer, shopping centre, hotel, café or other hospitality business.
So, if you feel obliged to provide free wireless internet access to your customers, how can you use it as a marketing and advertising tool?
Many business owners see Wi-Fi as an expense, without realising it’s an investment on which they can show a return.
Wi-Fi is a gateway to opportunities
Something as simple as a wireless network can help market your business in a number of ways:
- Understand your customers. You can collect basic information about customers when they connect to your wireless network. Just ask them to answer a few questions to get online. For instance, request their name, age and contact information.
- Show you’re ahead of the game. Offering services that are relatively new but growing in popularity — such as guest Wi-Fi — can set you apart from competitors. It’s particularly powerful if customers might not yet have come to expect free Wi-Fi from businesses like yours.
- Reinforce your brand. You can buy wireless routers that allow you to show a welcome page when a user connects. Use this to remind customers of your products and offers — or maybe even promote exclusive deals for Wi-Fi users.
One other big benefit
Finally, don’t forget the biggest benefit of all. Free Wi-Fi is a powerful marketing tool in its own right.
Consumers love to browse the internet, check their emails, update their social networks and more — no matter whether they’re having lunch, staying in a hotel or doing the weekly shop.
A free Wi-Fi service works to market your business all by itself, encouraging more customers to come through your door.
- How to build a wireless network
- Why every business need a wireless network
- Finding the right mobile internet device
Copyright © 2014 Bal Rana, founder of Freedom Hotspot.



