Posts for April 2011
Empty office? Take advantage by cleaning up your IT

How not to clean your computer. (Image: jblyberg under Creative Commons.)
So, after the first of two super-long weekends, it feels a bit like Christmas - only with better weather. With only three working days this week, you might be wondering whether there's much point getting stuck in to anything. Some companies have even closed down for the duration.
If you've found yourself in an otherwise deserted office this Tuesday morning, maybe you can take advantage. It's an ideal opportunity to spring clean, spruce up and service your business computers. Here are our suggestions:
- Carry out software updates and patches. If you've been waiting for an opportune moment to roll out updates to computers on your network, this could be it. With fewer people about, any glitches should cause little disruption. So when things pick up next week, you'll be fully up-to-date and ready to go.
- Clean up your computers. Sometimes keeping a computer clean of junk feels like a losing battle - especially if you have adventurous employees who install their own software. But there are ways to fight back: for a start, try CCleaner, which should do a good job of removing surplus files and settings.
- Get paranoid - do a full virus scan. Just because you haven't detected any viruses doesn't mean there aren't any on your systems. As there's no such thing as too much security, why not kick off a time-consuming deep virus scan of all your computers and servers?
- Have an actual spring clean. According to this admittedly old research, there are more germs on your average keyboard than on your average toilet seat. Maybe now's as good a time as any to get the disinfectant out.
- Restart your servers. Yes, yes, I know that many IT managers take pleasure in how long their server has been up without a reboot. But really, if it's not being used, you might as well restart it. It won't do any harm, and should clear any residual data out of the memory.
- Try something new - how about Linux? Yes, the open source operating system is intimidating if you've not used it before. But with a live Ubuntu CD and a few spare hours, you can get a feel for it. Maybe it'll give you the impetus to consider open source for your business.
If all that sounds like too much work, perhaps you should take a break too - if you have the luxury of being able to do so. It's a long time until the next three day week...
The broadband lottery: here's why your internet connection might be slower than you'd hoped

Is your broadband slower than this? (Image: RogueSun Media under Creative Commons)
Broadband companies have been criticised for advertising connection speeds that only a fraction of customers ever actually get. But it's not always easy for them to predict what speed an individual customer will receive. Sebastien Lahtinen from thinkbroadband explains.
Imagine you run manufacturing business that uses widgets as a component. You see an advertisement on a website from a company offering to supply 'up to 24 widgets' each month for a fee of £35 per month.
However, when your first delivery arrives you find it only includes nine widgets. On querying the error, the supplier's response is that they only ever promised 'up to' 24 widgets.
It sounds confusing, unfair and illogical. Yet this is exactly how most broadband services are sold. And the grounds for it are actually quite reasonable.
What is broadband?
Broadband describes what were considered fast internet connections at a time when slow connections were the norm. Most UK broadband is delivered using DSL technology (most commonly ADSL, which stands for asymmetric digital subscriber line). This uses old-fashioned copper telephone cables to get an internet connection into your business.
There are two main causes of slow broadband speeds and it is important to distinguish between them.
1. Congestion
Congestion can affect all internet connections. It simply means that too many people are trying to transfer too much data at once. Like having too many cars on the roads, it leads to delays in data reaching its destination.
Each broadband supplier has to strike a balance between capacity and congestion. To keep costs down, many broadband suppliers - especially those in the price-sensitive consumer market - operate a high contention ratio. This is the number of connections being sold compared to the total available capacity.
At peak times, broadband suppliers with a high contention ratio may not be able to service all customers at full speed.
To alleviate this problem, some companies implement traffic management systems. These can differentiate between different kinds of internet traffic, ensuring that when you're using your connection for something that requires a fast response - like video calls or online gaming - you get given priority.
Many business broadband packages have a low contention ratio. However, even so, your broadband supplier can't guarantee good end-to-end performance. The internet is, essentially, a network of connected networks. Your broadband supplier only has control over their bit of it. If congestion is a problem elsewhere, they can't do anything about it.
2. Technology
One of the main problems with ADSL broadband is that it relies on old copper telephone lines which were never designed for digital communications.
Signals degrade as they travel along the line, meaning that the further you are from your local telephone exchange, the slower your broadband service will be. In general, if you're within 2km of the telephone exchange then you will receive the top speeds, with a sharp fall thereafter depending on the type of ADSL technology used.
The upshot of this is that ADSL broadband suppliers can't market a service with a definite speed until they know the exact telephone line on which it will be used.
Before you order, most providers will give you an estimate of the speed they expect you to achieve. Unfortunately, this can't be guaranteed either, particularly as broadband providers don't own the phone lines they use.
They have to pay Openreach (the division of BT which maintains phone lines) for access to your line - and they pay the same regardless of what speed connection your line can support.
Confusing, isn't it?
What this means for you
If you're looking to purchase an internet connection, the key consideration should be how important the connection is to your business.
Every year, more companies are moving from local servers to cloud-based business applications, and from traditional telephone systems to VoIP services.
These applications require a reliable internet connection, so you need to look at not only the headline speed (which, as we've established, doesn't always tell the whole story) and price, but also the level of service on offer.
If your business can't function without internet access, make sure you build some redundancy into your connection - perhaps by using more than one technology or supplier. It's also important you look at upload speeds. These are important for some applications, like VoIP, yet many connections prioritise downloads, at the expense of upload speeds.
About the author
Sebastien Lahtinen is co-founder of thinkbroadband, the UK's first community dedicated to helping users resolve broadband problems. In addition to reporting on the latest broadband news, you can run a speed test on your current service, view a broadband map showing locations of telephone exchanges, availability and speeds in your area, and check if your internet connection is ready for IPv6.
Could the Telenoid bring your staff closer together?

The Telenoid looks nothing like this. (Image: Flickr user firepile under Creative Commons.)
This is a guest post from the Microsoft small business team. Read their blog or follow them on Twitter.
Some people are calling it ‘location liberation’. But however you want to refer to it, it’s about using tools like video-conferencing, collaboration technology and cloud computing to make it easier to work with other people, no matter where you are.
Introducing the Telenoid
One development you might have seen last year came out of Japan (where else?). It’s a somewhat creepy tele-operated android, which apparently helps you 'feel' the presence of another person.
The idea – apparently – is that instead of seeing your colleagues elsewhere on screen, they’ll be kind of projected onto the android.
As the BBC explains, “Professor Ishiguro's system uses a motion-tracking webcam to transmit your voice, facial expressions and head movements to the Telenoid, via a high-bandwidth web connection”
That creepy appearance is actually intentional – as Ishiguro described, “we also gave the robot a minimal design, so that people can use their imagination to make it more personal.”
Will it ever catch on?
Hmmm. While it’s early days for this technology, it’s hard to ever imagine it in the offices and meeting rooms of small businesses up and down the country. Would you rather have a strange android figure sat in on meetings, or simply use a flatscreen TV and video camera to see who you’re talking to?
The story goes on: “Holding and touching a business colleague's avatar might be a step too far...” I don't think anyone would argue with that!
While videoconferencing and other collaboration tools certainly have their detractors, many businesses use them successfully. So, on balance it’s probably better to start there rather than placing an early order for a Telenoid or two.
What's it worth? How to price your technology product

Ben Dyer of SellerDeck has been keeping an eye on how IT firms price their products. And he thinks we could all learn something from them.
Technology companies have been responsible for some innovative pricing ideas. So, if you're struggling to price your product - whether it's technology-related or not - can you take some inspiration from them?
The three 'r's of pricing
Recurring revenue rocks. Working for a software company, I know all too well the challenge of selling items that are one-off purchases. The upside is an injection of hard cash. The downside is that your sales team has to convert a fresh batch of prospects, every month.
One alternative is to aim for recurring revenue with a subscription model. You can charge a monthly fee to people who use your software, offer bolt-on extras like support and upgrades. Customers like this pricing model because the monthly cost is low, and it gives you the ability to predict the growth (or decline) of your business.
Give it away
Another option is to give your product away. This sounds mad, but can lead to huge growth.
It's called the 'freemium model'. The idea is to get people using a basic version of your service, then upsell more advanced features.
The freemium model only really works if your product has tiered levels and it doesn't cost you much to set up a new customer. It's a science all to itself - I recommend checking out Chris Anderson's blog and excellent books, Free and The Long Tail.
Two companies, two different approaches
Apple and Amazon both have numerous divisions, products and services. They also have completely different pricing strategies.
At the recent iPad 2 launch, Apple's Steve Jobs revealed that the company now makes more money from 'post-PC' purchases (iPods, iPhones, iPads) than from its traditional computers. One reason for this is the rise of third-party apps which run on Apple devices. Apple takes a slice of each one sold.
Apple has successfully blended the upfront payment and recurring service models. I would argue theirs is the best example of this type of pricing on the market. Most impressively, Apple has even managed to keep the initial payment high!
Amazon has taken a different approach with the Kindle, its electronic book reader. These come in two parts: the software, which is free for almost all platforms (including the iPad), and the hardware.
The hardware is cheap. At just £111 the price is getting close to impulse-buy territory. Many observers reckon the Kindle will be free to Amazon Prime subscribers by the end of the year.
The rationale, of course, is that most of Amazon's Kindle revenue comes from selling ebooks for people to read on the device. That's the company's fastest growing product range.
Amazon has been smart and reactive. The Kindle isn't a rival to iPods and iPads. It's complementary - so Amazon can grow its revenue too.
What could you learn from IT companies about pricing?
2011: the year of the data breach?

Are you taking care of data properly? (Image: Flickr user dawnzy58 under Creative Commons.)
If the first months of 2011 are anything to go by, this could be the year of the data breach. It almost seems like companies are falling over each other to give away information about their customers.
Here are three high-profile data breaches that have hit the headlines in the last month alone.
While you read about them, think about how many smaller incidents may go unreported or even undetected. Then stop to consider if your business does enough to safeguard its customer data.
1. The Epsilon effect
Epsilon runs huge email marketing operations for clients like Citibank and Marks & Spencer, yet still managed to have millions of customer email addresses stolen when someone got into the company's systems without authorisation.
What we can learn: the information stolen during this breach belonged to Epsilon's clients, many of whom have since warned customers that they may receive more spam as a result.
So, if your business shares data for marketing purposes or joint ventures, make sure you only work with partners you trust, and ask searching questions to find out how they protect the data. Get a strong contract in place that - if possible - places financial liability for data breaches on their shoulders.
2. Don't Play with your data
Hugely-successful Jersey-based online retailer Play.com suffered embarrassment last month when users reported receiving junk email to addresses they'd only ever used on the site. It soon emerged that a company responsible for some of Play.com's marketing communications had suffered a breach.
What we can learn: spotted the pattern yet? Just as with the Epsilon breach, although Play.com customers were affected, the leak actually occurred at another company.
However, Play.com's subsequent customer communications are an exercise in good damage limitation. They apologised quickly, explained what went wrong and described the possible consequences for customers.
3. Losing data the old-fashioned way
York City Council adequately demonstrated that you can lose data without turning to high-tech hackers. All you have to do is print it out and then send it to the wrong place. The council was criticised this week for accidentally posting personal information to a third-party.
What we can learn: hard copies can cause problems too, especially when left lying around. If you have to print out sensitive information, grab it from the printer quickly, then keep it somewhere it can't get mixed up with other paperwork. Once you're done with it, shred it.
Ten ways your printer can ruin your day
Printers: Laser or inkjet, every business has one. They're essential and, to be fair, they behave themselves most of the time. So why, when you come to print something important, do you know full well that your printer is going to play up?
Here are ten ways your printer can ruin your day, plus one that seems unique to me.
- Printer ink is low. You installed a new cartridge a week ago and haven't used it since. How can it possibly be low? Maybe it's because the printer purges all four cartridges each time you clean a nozzle. It feels like a get-rich campaign by cartridge makers.
- You can't print in black and white, because you've run out of colour. You only want to print an important letter. So why does it matter that you don't have any yellow ink left?
- When empty isn't empty. Dear Mr. Printer, it's great that you let me know when you'd run out of ink. I just wish you'd waited until the cartridge actually was empty. Yours, the owner of ink-stained clothing / carpet / other ruined items.
- Paper jams. Some days you can get a paper jam even when no paper is loaded. Now that is one heck of a jam! And it usually means poking around inside your printer until the error message goes away.
- No paper at all. If you used the last piece of paper in the printer, you'd replace it, wouldn't you? Unfortunately, not all office staff are so considerate. But don't fret; the printer will queue up all print requests ready for a print-fest once new paper is loaded.
- Update your printer driver. Surely in today's plug-and-play world, your printer driver should be able to update itself. No? Ok, but at least the manufacturer will have released a new driver for the latest operating system? No? Sigh.
- Phantom printer. 'No printer detected'? Well, how come it appears in my list of printers? And in my devices list? Anyway, I can see from here that it's plugged in to my computer. Only one solution: the hammer.
- My borderless print has a border. Why come with a borderless setting if, in actual fact, it's not borderless? False hope is not endearing. Be honest and say you'll 'print with 0.5cm border'.
- Randomly-changing paper size, orientation and scaling. You're almost certain you tried to print an email on A4 paper in size 12 font. So why has it come out at 6" x 4" in huge letters? Oh, right, the default settings have changed in that single piece of software.
- Why does restarting only fix things for five minutes? If you're going to break, at least have the decency to malfunction properly. Printing a few pages before you have to restart again is not helpful.
However, my favourite error is this last one. Maybe it's just me. I send a print job to my new Epson printer, as shown here:
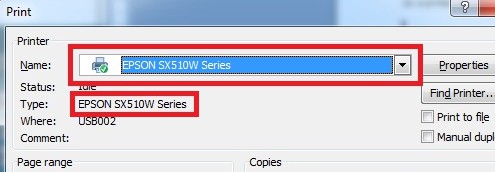
Does it print? Not exactly. Instead, I get this wonderful message:

I don't know why this happens, and haven't managed to fix it yet. Maybe I should try sending the print job to my mouse.
John Sollars is MD of Stinkyink.com
What are your humourous or frustrating printer problems?
The changing face of IT management
This is a guest post from tech blogger Jason Slater. Read his blog or follow him on Twitter.
The first business computer in the UK was LEO (Lyons Electronic Office). Designed and built for J. Lyons and Co, a catering and food company, it ran its first real program in 1951. LEO was based on the EDSAC computer (Electronic Delay Storage Automatic Calculator) which was essentially a large calculator that could run pre-designed programs.
 In those days a computer easily filled a room and ‘bugs’ were real bugs which would creep in and overheat the delicate vacuum tubes.
In those days a computer easily filled a room and ‘bugs’ were real bugs which would creep in and overheat the delicate vacuum tubes.
In fact, computers were few and far between, so queues to use them were a common sight.
Even into the 1960s (with machines such as the GEC 4000) and the 1970s (with the Xerox Sigma-5), the computing team was primarily engineering based.
The dawn of the desktop
In the ‘80s, many of us witnessed the dawn of the desktop computer. And it really was the desktop computer; it was pretty much tied to the user’s desk by a cable which needed to be plugged into a wall data socket. In those early days you couldn’t even move the computer without ‘parking’ the hard disk heads first.
The desktop computer created a need for IT departments full of people who knew the ins and outs of computers. They were the heroes who could rescue your work after you decided to lift the computer to clean up split coffee, without realising the movement would cause the hard disk heads to mash up the magnetic surface they were meant to be reading. (Should have parked them first.)
The changing IT department
IT departments are more devolved now. They’re more distributed and closely aligned with business strategy. You don’t see IT staff walking around with screwdrivers in their top pocket. They may not even have formal IT qualifications, particularly if IT support functions are outsourced or operated from a central location.
Computer issues are different today and they require different responses. Take the constantly shifting landscape of security threats. This is one of the most challenging areas for IT management.
In the mid-80s the biggest problems often came from users themselves. But now, now problems come from the outside - and they don’t stick to office hours. For instance, dealing with incoming spam email can be a headache.
In the past, the IT department may have been able to watch for specific words or phrases in emails, or spot spam by the address it was sent from. Spammers are more sophisticated now and make it a constant struggle.
Zero-day threats are a major problem too. No matter how up-to-date you keep your security software, you won’t necessarily be protected from threats that haven’t made it into the security software’s list yet.
Now we work everywhere
With the rise in mobility and cloud computing, people are being encouraged to work from anywhere at any time. Out of office hours (and often even during office hours) they use their own equipment – from broadband lines through to smart phones, tablet computers and printers.
It’s hard to provide support when everyone’s using different equipment. And you have to think differently about where your data actually resides. The IT department (or your IT person or IT supplier) needs to think strategically. It is almost impossible to provide a complete support and governance package with such diverse equipment and standards in operation.
(The National Museum of Computing at Bletchley Park is planning to rebuild the EDSAC computer. If you have a particular interest in EDSAC you could take a look at the EDSAC Simulator from the University of Warwick.)
(Image from Flickr user armaggesin under a Creative Commons attribution licence.)



