Blog posts tagged passwords
Can Microsoft Research predict your passwords?
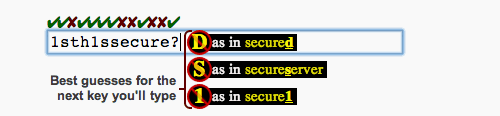
Here's a nice little tool that can keep you occupied this Friday afternoon and help you understand how hackers go about guessing passwords.
It's called Telepathwords, and it's been created by a team at Microsoft Research. It tells you how bad your passwords are by trying to guess the next letter as you type.
It uses real-world data — including passwords that have been made public by security breaches, and phrases commonly used online — to provide three 'best guesses' each time you enter a letter.
This reflects the kind of technique hackers might use when trying to guess passwords with brute force (basically, trying loads of passwords until they find one that works).
Once you've typed your whole password, you can see how many characters Telepathwords was able to guess. Five or more ticks above your password shows that it's reasonably strong.
More advice about passwords:
Are you using one of the world's worst passwords?
 Here's a list that might jolt you out of complacency if you're a bit lax when it comes to choosing and changing passwords.
Here's a list that might jolt you out of complacency if you're a bit lax when it comes to choosing and changing passwords.
SplashData, a leading provider of password management solutions, has put together a list of the 2012's worst passwords.
The list was compiled by analysing millions of compromised passwords that were posted online by hackers, and identifying the most common. It contains few surprises, but certainly underlines that we can all be far too slapdash when securing our online accounts.
Here are the top 10 worst passwords of 2012:
- password
- 123456
- 12345678
- abc123
- qwerty
- monkey
- letmein
- dragon
- 111111
- baseball
See any passwords you recognise? Change them, now. Because if you don't, it'll be child's play for a hacker to get in to your account.
Remember: the strongest passwords are as long as possible and use upper and lower-case letters, numbers and symbols. I like to choose a song lyric, take the first letters and then substitute in symbols and numbers where they're easy to remember.
For instance, the Rolling Stones' classic lines You can't always get what you want / But if you try sometimes you just might find can become:
- YcagwywB1yt$yjmf
See five other ways to create strong passwords you can remember >>
Five ways to create strong passwords that are hard to crack
 Hardly a week goes by without one company or another being hacked and user passwords being made public on the internet. Do we have any hope of keeping our passwords safe?
Hardly a week goes by without one company or another being hacked and user passwords being made public on the internet. Do we have any hope of keeping our passwords safe?
Actually we do have some hope, but we all have to play our part and choose strong passwords.
Hopefully, the websites we have online accounts with are doing their utmost to protect our personal information, and in particular our passwords. But even if they are, that’s not the end of the story as simple passwords can be cracked quite easily by hackers.
We need to do our bit by making sure we have strong passwords that are hard to crack. Here are five ways.
1. Think of a word and a number
Word: Olympics
Number: 1066
All you need to do is mix these up a bit to come up with a good password. For example:
10Olympics66
Olym10pics66
1Ol0ym6pi6cs
Top tip: make sure you mix it up. The password Olympics1066 is not as strong as the others.
2. Think of a lyric, name and a number
Lyric: She was more like a beauty queen from a movie scene
Name: Michael Jackson
Number: 1983 (Song released in this year)
Choose the first letter from the phrase and mix the initials and number in. For example:
SwmlabqfamsMJ1983
MJSwmlabqfams3891
M19Swmlabqfams83J
Top tip: once you decide how you want to mix it up, stick with it. If the mixing it up part could confuse you then you could write down a memory jogger – read on to find out how.
3. It doesn’t have to be too long
Phrase: Just like that
Name: Tommy Cooper
Number: 1921 (his birth year)
Password:
JltTC1921
You get the idea!
4. Write down a memory jogger
We all need help remembering things so why not write down something to help jog your memory? It is very unlikely that someone will be able to decipher a decent memory jogger, because you can write things down in a way that makes perfect sense to you but is useless to anyone else.
Lets take the Tommy Cooper example. You could have ‘Tommy’ written down in your address book, followed by a memory jogger, like this:
Tommy: Idp-pdI
In this case the memory jogger stands for initial-date-phrase-date-initial
Using this would give a password of:
T19jlt21C
5. And finally…
Remember, that really need to change your passwords every so often, because you can never be quite certain if your password is in the wrong hands.
The biggest problem most of us face is that we have so many online accounts that we forget what they are. Give yourself a fighting chance and keep a list somewhere. As you join new shopping sites, social sites and other sites, add them to the list. If you want to change a password, you will at least know where to look!
Friday Donut tip: generate unique, memorable passwords for any website

Passwords and website security breaches seem to be in the news constantly. Yet people still insist that passwords are generally a nuisance, and would rather have simple ones or use the same one for every website.
But that's risky. Having just one of those passwords revealed could potentially allow an attacker to access many of your other online accounts.
One really simple way to ensure you have a unique password is to use the name of the website in the password itself.
Come up with a password (or better yet, a passphrase) that you will remember. For example:
Ilikepineapples
That will be the base for your other passwords. For your Google account, you would use the password:
IlikepineapplesGoog
For your YouTube account you would use:
IlikepineapplesYout
Easy! You can obviously make the passwords as complex as you like, using numbers, symbols and both upper and lowercase letters.
Bonus tip:While browsing through the settings for my Gmail account, I spotted two-step verification. This is an excellent way to secure your Google account using your mobile. Every time you sign in on a new device, Google will call or text you a code which you must enter on the website. You won’t have to do this again for 30 days, unless you select otherwise. This way you’ll also know if anyone is trying to break into your Google account, as you will get an unexpected automated phone call from the big G. |
NB: I would recommend including numbers, symbols and capitals in your password. I didn't here for simplicity.
Previous Friday Donut tips:
Friday Donut tip: securing LinkedIn passwords
This week, online services LinkedIn, eHarmony and Last.fm all suffered security breaches which saw users' passwords fall into the hands of hackers. It's not the first time something like this has happened and it won't be the last: previous victims have included Gawker and Twitter.
I've mentioned before that I think passwords are broken. But they're here to stay, at least for the foreseeable future. So for this Friday's Donut tip, we explain what you should do if you have an account with one of the affected services.
Secure your account
To begin with, be wary of any emails you receive warning that your password has been leaked. They might be genuine, but there are lots of phishing attempts going round too, so you're better off just deleting them.
The next step is easy: PANIC!
Actually, I'm just joking. You definitely don't need to panic. It's counterproductive and unnecessary, because it's actually pretty easy to secure your accounts:
- Go to the website of the service you use (LinkedIn, eHarmony or Last.fm)
- Log in using your normal username and password
- Use the change password option to make your password something completely new
(Don't just change a single letter or number of your old password - use something totally different. At this stage it's a good idea to make sure your password is nice and strong. I've put some tips below)
That's it, unless - like most people - you use the same or a similar password for other things. You see, scammers aren't stupid, and they know that if you use that password for your LinkedIn account, perhaps you also use it - or something similar - for more important services, like your email.
This means you also need to change any identical or similar passwords that you use on other services. You should really have a different password for each one.
Creating strong passwords
You've probably seen the usual advice about creating strong passwords. Use upper and lowercase letters, numbers and symbols, don't use words you'd find in the dictionary, and so on. But these passwords can be devilishly hard to remember.
I like the song lyrics trick: take a memorable line from a song, pull out the first letters of each word, then wrap it in a number that you can remember.
For instance, a Rolling Stones fan might choose the first line from Sympathy for the Devil: 'Please allow me to introduce myself'. And he might be able to remember 1960, because that's the year he was born.
Shortened, it becomes 19Pamtim60. Not bad.
Alternatively, you can use a tool like LastPass to generate and remember super-strong passwords for you. John Sollars talked more about keeping passwords safe in a recent post over on Startup Donut.
Previous Friday Donut tips:
How hackers target your passwords
 When you enter a gym’s locker room, there are hundreds of lockers. Each has its own combination lock. Without giving it too much thought, you open your locker using the combination only you know, which is the same combination you provided when you signed up at the gym.
When you enter a gym’s locker room, there are hundreds of lockers. Each has its own combination lock. Without giving it too much thought, you open your locker using the combination only you know, which is the same combination you provided when you signed up at the gym.
Similarly, a password is a shared secret between a user and a service. When the user wants to connect to the service, they identify themselves with their username and prove that identity with the password.
The service checks the password. If it matches, the user is allowed to access the service.
We can think of the service as the locker, the username as the locker’s number and the password as the lock’s combination.
Problems occur, of course, if someone else has your combination. It could be that you use a very popular combination, or someone saw you using the same combination on your bag.
Alternatively, it could be that someone broke into the gym and saw the list of locks and combinations. Let’s take a look at these aspects in the virtual world.
How hackers break your passwords
On the internet, some passwords are more common than others. Hackers use lists of the most common passwords to increase their chance of guessing a user’s password quickly. The hacker tools used to guess these passwords are called crackers. Two types of crackers exist - online and offline:
- Online crackers use trial and error to break into a service, testing different passwords until the right one is found. The speed at which they can test passwords is limited by the speed at which the service accepts and handles requests. In many cases, online crackers can only try a few passwords because most services lock accounts after a certain number of incorrect passwords have been entered.
- Offline crackers are used when passwords are stolen from an online service, but are stored in a digested format. This means the service stores a mathematical transformation of the password rather than the password itself – it’s an extra security precaution. An offline cracker repeatedly chooses different passwords, transforms them to their digested format and compares them to the list. Offline crackers can run incredibly fast, depending on the power of the computer running the cracker.
To reduce the effectiveness of offline crackers, many services add a step to the process called salting. Using a salt, a different digest is created each time, even if the password is the same. So although salted passwords are not completely hack-proof, they’re much harder to guess.
How to secure passwords in your business
So, that’s how passwords get cracked. Now, how do you stop that happening to your business?
On an individual level, always use strong passwords – and don’t use the same password on different websites. Think about what information the password is protecting. You want a really strong one for your online banking, PayPal and other online services you consider sensitive.
Use a really strong password for your email too, as getting access here can allow a hacker to wreak havoc by resetting your passwords on lots of other sites.
In your business, it’s important to realise that you can’t trust your users to choose strong passwords themselves. If you give them the choice, they’ll simply choose weak passwords. In fact, two years ago a database containing 32 million passwords was leaked to the web. Analysis of these passwords showed that 20% of users chose the same passwords from a pool of 5,000 words.
It’s up to you – or your IT administrator - to keep the passwords secure. Here’s how
- Enforce strong password policies. Force passwords to have a minimum length, ban common passwords and require a mix of characters (digits, letters, uppercase, lowercase, etc).
- Make sure passwords are not transmitted in the clear. Passwords are vulnerable to interception if they’re transmitted across networks or the internet. Always use encryption, or use a technique that ensures the password itself never travels through the network.
- Don’t store passwords in plain text. Doing so means that if a hacker breaks into your systems, they can just grab and make off with your passwords. Salt and digest a password before storing to the database.
- Detect and block brute force attacks. Put obstacles in the way to stop online crackers trying lots of different passwords for user accounts. Use CAPTCHAs and restrict the number of times people can retry their passwords.
- Force people to change passwords regularly. Many businesses require users to change passwords every couple of months, or when they suspect an account has been compromised.
- Allow and encourage passphrases instead of passwords. That means using sentences instead of passwords. Although that may be longer, they’re easier to remember. And because they’re longer, they’re more difficult to break.
Implementing many of these precautions will require help from your IT staff or IT supplier. But if you’re going to maintain the security of your systems and website, it’s vital you think carefully about enforcing a strong password policy.
Noa Bar-Yosef is Senior Security Strategist at Imperva.
Why you need a security policy

Not a secure way to store passwords. (Image: Nina Matthews Photography on Flickr.)
News just in. Your computer system has been broken into! Yes, your impregnable firewall, amazing anti-virus and 99.9% secure password have all been breached. How could this be? Step forward your company employees.
Recent studies have compounded old research highlighting the astounding ignorance and negligence of employees when it comes to security. Read on to see three ways your employees can undo all your investment in security, and to find out where you may be at risk.
Strangers in the office
A Computer Weekly survey reported that only 4% of employees would challenge a stranger walking into their office and sitting down at a computer. What's more, only 3% would actually ask them for identification.
I'd hope those figures would be higher in smaller businesses, where it's more common for everyone to know everyone else who works there. But it still demonstrates why you need a system of identification of authority - like ID cards - in the office.
Passwords are key
Password security is another key aspect. Aside from the oft-discussed need to use upper and lower case letters, numbers and other random symbols in passwords, it’s how your employees remember logins that can fall short.
A common approach is to write passwords on post-it notes, then stick them under phones or keyboards. Worse, some people stick them in plain view. This gives any intruder a reasonable chance of gaining access with no tools or knowledge of your systems.
One reason passwords are such an issue is that people don't see them as being particularly valuable. One survey found 90% of commuters were happy to exchange their passwords for a free pen!
Sure, some passwords may have been fakes to get a free pen. But the statistics still show a lack of understanding about the damage even a low level user’s password can do in the wrong hands.
Approve all hardware and software
A Valentine's Day study provided random workers with CDs, claiming they contained a promotion to win a romantic holiday. In reality, the CDs sent people to a website promoting security.
The point of the exercise was that the people behind the CD were able to run unauthorised software on computers situated within a company's IT system. According to the study, 75% of people ran their CD.
And a more recent study by the US Department of Homeland Security involved leaving unmarked pen drives and CDs in company car parks, then letting curiosity do the work.
Again, no malicious code was run, but the potential for wrongdoing was there. CDs and pen drives were inserted by 60% of people. If the CD or pen drive had a logo on it, that figure rose to 90%. Scary stuff.
Get your security policy right
I hope these stories have opened your eyes to how even the simplest, most innocent notions can compromise your company’s security. Have you been hit by negligent employees? Do you think you’re at risk? Leave a comment below to let us know.
John Sollars is MD of Stinkyink.com



