Posts for November 2013
IT for donuts: what's the best mobile device for working on?
IT for donuts is our regular Friday feature where we explain a tech term or answer a question about business IT. This week, find out which sort of mobile device is best for working on the move.
There are lots of different ways to work on the move. But there are only three main types of mobile device that you can work on. Each is good in different situations, so here's our guide to when and where each is best.
1. A smart phone
 Smart phones are small but powerful. You can slip one in your pocket to get online anywhere.
Smart phones are small but powerful. You can slip one in your pocket to get online anywhere.
Because they're always switched on and to hand, smart phones are great when you need to look up information in a hurry.
However, a small screen size makes them less-than-ideal for extended use or working on documents.
- Good for: sending and receiving email, checking social media, viewing maps, looking up information online and getting on the internet when space is tight (like crowded trains).
- Not so good for: working on documents or using for extended periods.
- Use when: you're out and about and just can't wait to perform a task online. Smart phones are best carried at all times and used on the hoof.
- Secret weapon: powerful smart phone apps enable you to extend the capabilities of your device. For instance, you may be able to send invoices on the go.
2. A tablet computer
 These touch screen devices have no keyboard, but are small enough to carry in your bag all day. They provide a good compromise between the portability of a smart phone and the power of a laptop.
These touch screen devices have no keyboard, but are small enough to carry in your bag all day. They provide a good compromise between the portability of a smart phone and the power of a laptop.
- Good for: sending and receiving email, social media, viewing websites, watching video and doing tasks that don't require much typing.
- Not so good for: anything that requires lots of typing or precise mouse work (there's no keyboard or proper mouse).
- Use when: you need to catch up on work between meetings or on a journey. Tablets can be used comfortably for a few hours at a time and have big, bright screens for reading and reviewing documents.
- Secret weapon: connect a portable keyboard to make writing and editing documents much easier.
3. A laptop
 Nothing beats a laptop when it comes to capabilities, because it's a full-on computer that you can use to run all your usual software. Microsoft Word, Excel ... they're all there to use on the go.
Nothing beats a laptop when it comes to capabilities, because it's a full-on computer that you can use to run all your usual software. Microsoft Word, Excel ... they're all there to use on the go.
However, laptops are heavier than other options and tend to have worse battery life.
- Good for: doing everything you do in the office — like working on documents, presentations and spreadsheets.
- Not so good for: instant internet access (you have to wait while it boots up), working in tight spaces, carrying on the off-chance you'll have ten minutes to fill with work.
- Use when: you're going to be away from the office for a while and will have a desk or table to work on.
- Secret weapon: you can use a laptop as your main business computer too. Just plug it into a separate screen, keyboard and mouse when you're at your desk.
Already have a laptop?
Many people already have laptops for business use — and companies are increasingly issuing them to employees as standard.
If you're happy carrying your laptop when you need to work on the move for extended periods, a smart phone should be your other device. It's ideal for getting online in a hurry to look up information or check your email.
In this sort of situation it's harder to justify a tablet computer too.
However, if you have a main desktop computer back at base then a tablet is a great mobile option — especially if you want a device you can carry 'just in case' you decide to get some work done.
Is virtualisation a magical way to cut your costs?
 Modern computers and servers are so powerful that many businesses tend to only use only a small percentage of their full capabilities.
Modern computers and servers are so powerful that many businesses tend to only use only a small percentage of their full capabilities.
For instance, if a server is only being used to store files and share internet access then much of its processing power is going to waste.
In recent years, more companies have started using virtualisation to help harness some of that untapped power. So, what is virtualisation and why should it matter to your business?
Virtualisation: many servers, one box
Virtualisation involves sharing computing resources so your business can get more bang for its buck. This clever technology allows one physical server to function as several servers.
That’s why they’re called virtual servers: although they behave like individual servers, they all run on the same piece of hardware.
For example, instead of running your each of your in-house applications (email server, accounting system, CRM system etc) on its own physical server, you can ‘virtualise’ one big server and run the whole lot on that.
Doing so means you only have one physical server to maintain. Virtualisation is also handy when different applications can't run together under the same operating system. For example, perhaps your accounting software runs on Windows but your website requires Linux.
Power when you need it
These days, you can take advantage of virtualisation without actually owning any hardware yourself. Instead, you rent your virtual servers from another company, often a web hosting or cloud computing firm.
In this situation, you’ll never see the physical server on which your virtual servers run. It sits safely in a data centre where it may be shared by other businesses too.
The beauty of this approach is that the resources needed to run your applications can be spread across a number of virtual servers, which are all shared between companies.
This means that there’s lots of computing power on tap should you need it — yet you don’t have to invest in expensive hardware yourself.
To spread the load, many virtualisation services split computing power between customers in different time zones, so there’s always enough spare capacity to go round.
Is sharing servers safe?
One of the first questions businesses have about sharing servers in this way is: ‘Are our applications and data safe if we’re sharing with other companies?’
Usually, the answer is yes, as long as you are dealing with a reputable provider. If they are a European firm and covered by EU data protection laws then that gives you extra reassurance. In general, you should ask the same questions of your provider as you would of any other cloud computing company.
Virtualisation is all about sharing the cost of computing resources. If more businesses can share a single resource, that resource becomes cheaper for each individual business. And that’s why virtualisation should matter to you.
- How much computing power is wasted in your business?
- Q&A: do more with your network server
- How we replaced our stretched servers with virtualisation
This is a guest post from John Paterson, CEO of Really Simple Systems
Five tips and tech tools to stay focused
 Raj Dhonota is an entrepreneur and former contestant from The Apprentice who’s seen many business owners try and fail to do everything at once.
Raj Dhonota is an entrepreneur and former contestant from The Apprentice who’s seen many business owners try and fail to do everything at once.
In this guest post, he provides some simple advice to stay focused and in control.
Multi-tasking is inevitable
Even though we all know that trying to do more than one thing at a time makes us less focused and less productive, we still try to get away with it.
That’s because having to deal with more than one thing at once is inevitable in the real world. There’s never just one task to take up our attention.
1. Use a good task list manager to plan ahead
This is absolutely essential to staying in control. Keep a task list of anything and everything that you need to do and keep updating it as new tasks arise.
Prioritise these tasks into must-do, should-do, could-do and won't-do categories. Above all, keep in mind your strengths and delegate tasks that don’t fit these.
Also, understand what you can realistically achieve in one day. A clear list of tasks, combined with some discipline, will make a big difference to your mindset and productivity.
There are lots of good tools to manage your task list electronically. Try Any.do or Remember The Milk.
2. Find other tools that can help
There are tools your can use to improve your overall focus.
I use Asana to set my goals, targets and tasks. It also enables me to share and delegate jobs to other members of my team. Mind mapping software is helpful in defining goals and targets that you can prioritise and focus on.
Of course, tools are only as effective as the person using them, so make sure you have adopted the right mindset and implemented the best processes before you resort to these.
3. Change your surroundings
Environment is a key factor in improving focus. The more comfortable your work environment, the greater your ability to concentrate.
I find that purposefully changing my location during a long day, for example, from my home office to the sunroom, helps introduce a new impetus to my work. You could try working in a café or another public location.
4. Remove distractions
It sounds obvious, but removing and avoiding as many distractions as possible is one of the best ways to improve your focus. It's astounding how personal issues can creep into your work zone.
Adopt ‘digital do not disturb’ by turning off your mobile phone. Close your email and chat programs and deal with them later. Try using Cold Turkey (for Windows) or SelfControl (for Mac) to block distracting software and websites.
5. Know your energy levels
You know when you're at your best, whether it is early morning or late at night when you have peace and quiet.
Do the hardest tasks when you're most alert and leave less-intensive jobs until later on in the day when you have less drive.
- Four easy ways to stay focused while you work
- Can the sounds of a café increase your creativity?
- Three IT tips to get you more organised
This is a guest post from Raj Dhonota, entrepreneur and former contestant on The Apprentice.
IT for donuts: what on earth does RAM mean?

To replace our long-running series of Friday tech tips, we've invented a new feature. Appropriately, we're calling it IT for Donuts.
Starting today, every Friday we'll explain a tech term or answer a question about business IT. We'll stick to jargon-free language, so you can actually understand what we're on about.
To kick things off, we answer the question: what does RAM mean?
Ok then, what does RAM mean?
You'll have seen the term RAM in adverts for computers. You might also have noticed it mentioned in messages on your computer screen, or in the largely-incomprehensible system requirements printed on the side of software boxes.
RAM stands for random access memory. (Don't confuse it with the Daft Punk album, Random Access Memories.)
Think of RAM as your computer's short-term memory. RAM provides space for information that your computer needs to have readily available.
For instance, when you open a piece of software, all the data relating to that software is moved to your computer's RAM. This makes it easy for your computer to get at it quickly, which means the software runs nice and fast.
In its physical form, RAM is a bunch of chips inside your computer, as pictured above.
How RAM is used by your computer
Ok, here's an example. Imagine you've just turned your computer on and no programs are running. Then you double-click a Microsoft Word document to open it.
At that point, the document will be moved from your computer's hard drive (its long-term memory) into the RAM (its short-term memory). This is because it's much quicker to access data when it's held in the RAM.
As you edit the document, the data in the RAM changes. And when you hit save, the data in the RAM is copied back over to your hard drive.
Why you need plenty of RAM
As you open more files and programs on your computer, it loads more data into the RAM. If it gets to the point where the RAM is full, your computer will slow down, because it has to shuffle data on and off the hard drive more frequently.
That's why the amount of RAM you have is important.
RAM is measured in gigabytes (GB). You don't really need to know what a GB is, but the more you have the better. If you're buying a new computer, 4GB should be fine for everyday use, but paying a little extra for 6GB might be wise in the long run.
If your computer is starting to show its age, adding more RAM is one of the most cost-effective ways to speed it up. Most computers have space inside for extra RAM, which you can buy and install yourself.
Still confused about the cloud? You're not alone
 What is the cloud? You’ll get a very different answer depending on who you ask that questions.
What is the cloud? You’ll get a very different answer depending on who you ask that questions.
That’s because ‘cloud’ is a fluffy term that has been blown around endlessly, used by different people and organisations to mean different things. There’s never been any consensus about what it actually does mean.
Some people argue it simply refers to the internet. Others suggest it’s just a manufactured term that means absolutely nothing.
In general, consumers are most aware of Amazon Cloud Drive or Apple iCloud. Often they feel as if the rest of the cloud computing industry has been thrown into the mix to confuse them.
The ‘official’ definition of cloud
The most widely accepted definition of cloud computing comes from the US National Institute of Standards and Technology. It states:
“Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
Now that’s all well and good, but if you’re a business owner embroiled in running and growing a company, it probably doesn’t make a lot of sense. You just want a straightforward solution that’s going to support your business as it grows.
Cloud in a simpler form
The company I work for — Names.co.uk — offers cloud services. When we talk about the cloud, we are referring to a cluster of servers. These work together, providing one large platform that can be sub-divided up into smaller chunks to do useful jobs like hosting your website or running a customer database.
Each user has an isolated virtual server, with its own operating system, control panel and software. They also get a guaranteed share of network resources, giving them confidence that the cloud will perform for them.
The cloud is about flexibility
One of the biggest benefits of the cloud in this form is flexibility. Users can increase and decrease their computing power as and when they want, only paying for what the need.
More and more businesses are moving to the cloud because they like the idea of not paying for services they don’t use. It’s like buying a mansion when you only need a one-bedroom flat, with the option of upgrading to two bedrooms if you need to.
But if you’re still struggling with the question: ‘what is the cloud?’, why not see some more answers? We asked some people what the cloud means to them. See their answers in this video.
This is a guest post from Names.co.uk.
The last rites of traditional IT security
 Anti-virus software has been one of the standard weapons against online threats for the past two decades. But as the nature of online dangers changes, anti-virus software is starting to look past its sell-by date.
Anti-virus software has been one of the standard weapons against online threats for the past two decades. But as the nature of online dangers changes, anti-virus software is starting to look past its sell-by date.
Nowadays, it’s not worries over traditional viruses that keep IT professionals awake at night. Their number one concern is more likely to be the targeted attack. Online criminals will stealthily approach your business, gaining access to critical systems, leaving virtually no trace.
Factor in clever new malware delivered via phishing or social engineering and you start to realise that anti-virus software is near-useless against this new generation of threats.
Professional online criminals
Professional online criminals are often behind these new threats. From stealing valuable intellectual property to coordinated attacks on bank accounts, the online attack model of today is a world away from the loud-mouthed internet vandals who used to dominate the headlines.
Today’s attacks are carried out by groups, rather than individuals, are designed to steal valuable data — and often leave no trace.
What’s more, online attackers are patient. An analysis of what’s known as advanced persistent threat (APT) incidents by Mandiant revealed the average period over which attackers controlled a victim's network was one year.
That’s a long time for online criminals to have access to your data without you realising.
Additionally, many of these breaches are inside jobs, where authorised users (often company employees) load malware or password-capturing software onto company systems.
Anti-virus was never enough
In all honesty, anti-virus software has always had its weaknesses. It has to be updated daily and cannot effectively prevent against new threats until they have been identified and an antidote created.
This model was flawed when most viruses were noisy and high-profile. But today, threats are silent and stealthy. With fewer organisations affected, there are fewer opportunities for the virus to be identified and neutralised.
What should we use instead?
If anti-virus software isn’t enough, then what are the options?
First off, organisations need to address any complacency that exists and start implementing security processes that are key to effective defence.
Getting the basic principles of security right is a good place to start. Creating a security checklist is relatively straightforward with help from an IT professional or supplier. Doing so gives you a clear list of recommendations and will help you identify any weaknesses in your business.
File integrity monitoring
However, you also need an infallible way to detect malware if it does manage to bypass security defences.
File integrity monitoring (FIM) is an excellent way to do this. It radically reduces the risk of security breaches by warning when a change has been made to underlying, core file systems.
Flagging changes in this way makes it harder for threats to take hold because you get immediately notified if changes happen that could indicate a stealth attack.
A combination works best
File integrity management works best when combined with strong change management processes. This means your business needs to keep tight control on who is allowed to make changes to core software and when they may do so.
It’s not a silver bullet that will make your business impervious to online threats. But as a core plank of your security strategy, file integrity management can effectively protect your data and dramatically reduce the risks your business faces.
- Most small businesses have had a security breach. Have you?
- Save your business from a security threat
- How to perform an IT security risk assessment
This is a guest post from Mark Kedgley, CTO at New Net Technologies,
The end of Windows XP: what you need to know
 Microsoft recently reminded Windows XP users that this venerable operating system is being retired in April 2014.
Microsoft recently reminded Windows XP users that this venerable operating system is being retired in April 2014.
Windows XP has just passed its 12th birthday, and on 8 April next year Microsoft will end support for it. If you’re still using it, this means you will no longer receive security patches or updates — and Microsoft won’t be able to provide you with any sort of support for Windows XP.
Time to ditch Windows XP
Because Microsoft will no longer be updating Windows XP to guard against new security threats, it’s important to move away from the software before April next year.
This may pose a challenge for any companies still using Windows XP — and there are plenty of those. Despite just passing its twelfth birthday, according to Net Market Share Windows XP is still the second most popular operating system, with a significant 31% market share.
XP has been a great choice for businesses. It was relatively easy to pick up because it feels familiar to many users and supports a lot of bespoke business software. As a result, many businesses have been reluctant to upgrade.
Software has moved on
However, desktop software has come a long way since Windows XP was released in October 2001. So has hardware. In fact, Microsoft released three new versions of Windows over those 12 years: Windows Vista, Windows 7 and Windows 8.
Vista never really gained a foothold with businesses, but Windows 7 now enjoys considerable market share.
How to cope with the end of XP
If you currently use Windows XP on any of your business computers, it’s time to take action. Don’t put it off — once Microsoft drops support for Windows XP, so will many other software companies. You could soon find you’re unable to run some of your key business software.
More worryingly, in six months time you will be at an increased risk from malware and viruses, as hackers begin to target the unmaintained operating system. Consider your options now and plan to replace Windows XP before the deadline.
Upgrading Windows XP: your options
The most recent Microsoft operating system is Windows 8. It has a significantly different interface compared to its predecessors and has attracted some criticism for this, so you may be more comfortable upgrading to Windows 7, with its familiar look and feel.
There are also hardware factors to consider when you upgrade. A computer running Windows XP is likely to be as dated as the operating system itself.
Even if it can handle a newew operating system, it’s likely to be considerably slower than Microsoft intended — and this could hit your productivity. The end of Windows XP could therefore be a good time to replace your business computers, too.
Can we keep using Windows XP?
On the morning of the 9 April, your Windows XP computers will still start up as they have done for the past decade. However, the lack of support and updates — not to mention the increased threat of malware — should be enough to put you off of doing so.
Quite simply, after 8 April, the longer you hold on to Windows XP, the greater the chance you’ll suffer some sort of problem or catastrophe from which it’s hard to recover.
Microsoft is keen to see businesses upgrade, as this allows it to focus resources on developing new software, rather than maintaining older versions. However, it costs to upgrade, so there’s certainly a commercial incentive too.
In all, Windows 8 is a considerably more advanced and future-proof operating system than Windows XP. If you’re currently persevering with this old software, there’s no better time to make the leap and upgrade.
- Does your business need Windows 8?
- Will you have to upgrade to Windows 8?
- ISS it time to ditch Microsoft Windows altogether?
This is a guest post from Adrian Case, technical director at Akita IT support in Kent.
Friday tech tip: a hassle-free way to send large files by email
Sharing a folder with Box.
Trying to send big files by email is fraught with difficulty. Many email systems block large attachments, and big files can crash or slow email software.
So, for this Friday's tech tip, we show you a better way to send big files using a service called Box that provides online storage space for files. Once you've uploaded files there, you can share them with other people by just sending a link in an email.
It's quick and easy, and — unlike many similar services — doesn't require the recipient to sign up to Box too.
It's a good idea to use a method like this any time you're trying to send email attachments totalling more than 5MB (megabytes) or so.
Get signed up
To get started, you need to sign up for a free account with Box. There are a range of paid-for packages, but the free option is fine unless you need to send a really large volume of data:
- Fill in the sign up form on the Box website.
- Check your email for the Box activation message.
- Select the Verify Email button to finish signing up.
Create a folder
To keep things organised, create a folder for the files you want to send:
- Go to the Box website and sign in
- Select the New button (top right), then choose Folder.
- Enter a folder name and select Create Folder. Don't change any other settings.
- Open your new folder by clicking or tapping it (if you're using a touch screen).
Upload your files
Next, you should upload all the file(s) you want to share.
The quickest way is to drag the files from your computer to where it says Drag and drop files from your desktop.
Alternatively, select the file browser option, choose the file(s) and then hit Open.
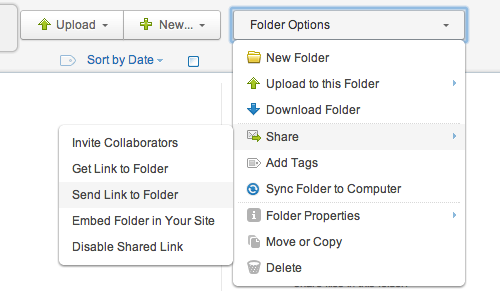
Share the folder
With your files safely uploaded into the folder you created, all you need to do is to share the folder with the recipient:
- Select Folder Options near the top right of the screen.
- Choose Share, then Send Link to Folder (see screenshot above).
- A box will appear. Enter the email address of the recipient.
- You can also enter a message to accompany the link to your shared folder.
- When you're ready, select Send.
The person you're sending the data to will receive an email containing a link to your shared folder. When they select it, they'll see the contents of the folder and can download the files they need.
It's much easier than trying to send large amounts of data in an email attachment.
The three downsides of cloud computing
 Cloud computing has had a huge impact on business technology in recent years. It is capable of offering on-demand computing power, email services, collaboration tools, disaster recovery systems and security, often at a lower cost compared to on-site hardware and software.
Cloud computing has had a huge impact on business technology in recent years. It is capable of offering on-demand computing power, email services, collaboration tools, disaster recovery systems and security, often at a lower cost compared to on-site hardware and software.
The cloud is still growing fast, but before your company embraces it wholeheartedly, it’s worth looking beyond the hype to check out the possible downsides.
Like most technologies, the cloud does have some disadvantages. Here are three important ones.
1. Availability
When using cloud computing services you are heavily reliant on the availability of your internet connection and of the cloud service itself. Investing in a robust internet connection with a backup will ensure things are reliable at your end.
It’s also important your cloud provider’s servers are located in more than one data centre. This ensures they can continue providing you with access to files and data, even during problems at one of their data centres.
2. Security and privacy
Who can access your data? Is it safe on your cloud provider’s servers? Could it be stolen?
Every reputable cloud provider should meet all relevant data protection legislation and operate robust, encrypted networks. But even if you’re confident about your provider’s security precautions, the biggest dangers may lie elsewhere.
More specifically, those dangers may lie within your own business. Because using the cloud will enable your staff to access company data from anywhere, you need to work harder to make sure it stays within your business.
3. Accountability
Moving to the cloud does not mean liability falls into someone else’s hands. You still have full responsibility for your business operations, yet using the cloud means you’re effectively outsourcing some of your IT systems.
It is vital that you have a contingency plan to overcome any potential risks. For instance, how would you cope if your internet connection failed or your cloud provider went bust?
Get professional advice
If you’re considering a move to the cloud but want to proceed with caution, it’s important to seek a provider that can offer you advice and solutions tailored to your business.
It can be a good idea to identify a supplier that offers IT consultancy, support and traditional in-house expertise alongside cloud services. Moving everything into the cloud at once isn’t usually practical, but you can strategically move services when it’s right for your business.
- Cloud computing: a new horizon for small firms
- Q&A: cloud computing security
- How do businesses use cloud computing?
This is a guest post from Leia Solanki, Marketing Executive; Tegen Ltd
Do you need to secure your smart phone?
 If you own a smart phone, you’re carrying a powerful computer around in your pocket. And, like all computers, it’s a potential target for malware, online criminals and hackers.
If you own a smart phone, you’re carrying a powerful computer around in your pocket. And, like all computers, it’s a potential target for malware, online criminals and hackers.
Never given your smart phone security more than a passing thought? You’re not alone. Technology analysis firm Juniper Research has found more than 80% of company and personal smart phones will remain unprotected at the end of 2013.
Mobile risks are increasing
The report — Mobile security: BYOD, mCommerce, consumer and enterprise —found that security risks are on the rise due to an explosion of mobile malware over the last two years.
Cyber criminals are switching focus, targeting PCs less and mobile platforms more. These findings support Trend Micro data showing that that there are already more than a million different pieces of malware and high-risk apps for Android devices alone.
We’re more aware of mobile security
It’s not all doom and gloom though. The report identified that although adoption rates remain low, awareness that mobile security products exist is growing. So, if more of us know that there are tools to protect our smart phones, why aren’t we using them?
Well, perhaps the risks are less obvious than on our desktop computers. After all, have you, or anyone you know, been affected by malware on your smart phone? The dangers are growing, but aren’t yet high-profile enough to encourage mass adoption.
BYOD and security
The report claims that the low level of adoption of security software can be attributed to a number of factors, including the relatively low awareness about attacks on mobile devices and a widespread perception that the price of security products is excessive.
However, with BYOD (bring your own device) — where employees use their own mobile devices for work — becoming more common, it’s important that your business starts thinking about mobile security.
Using mobile security software may be a start, but really you need to step back, taking a broader look at how you use mobile devices and where the risks lie. Then you can create a mobile security plan to keep your data, your employees and your business safe.
Friday tech tip: stay connected on holiday without getting overwhelmed
 Some people aim to stay as out of touch with work as possible while on holiday.
Some people aim to stay as out of touch with work as possible while on holiday.
However, if you run your own business, you're more likely to take a 'worliday', staying up-to-date with important issues while leaving everything else until you're back at work properly.
If you fall into that camp, for this Friday's tech tip we bring you a list of six ways to stay in touch while you're away — without letting work take over your break:
- Take your smart phone, but not your laptop. It's all you need to stay up-to-date with email, but the lack of a proper keyboard will deter you from getting into other pieces of work.
- Make sure your mobile will work at your destination. If going abroad, check that you have international roaming. Some countries have mobile networks that operate on a different frequency, meaning you may need a tri- or quad-band phone.
- Set automatic out of office messages. Make sure people who email you receive an automated reply letting them know when you'll be back. Change your voicemail to say the same thing. If possible, include details of someone else who can help.
- Keep your phone off during the day. Don't let business callers interrupt your holiday. You can check your voicemail and respond to any messages each morning or evening.
- Learn how to access your voicemail from abroad. You may need to set a PIN or call a different number to listen to your messages. Find out before you go. If you have a pay-as-you-go phone, make sure you know how to top up your credit too.
- Don't turn on data roaming. Using mobile internet while overseas is expensive. It'll save money if you rely on connecting to Wi-Fi in your hotel, cafes, bars and restaurants.
Do you stay connected while you're on holiday? Share your tips below.
Who's been reading your email?
 Think your email is safe and private? Think again. Most emails sent over the internet travel in plain, unencrypted form. That means anyone who knows where to look could theoretically intercept and read your most private missives.
Think your email is safe and private? Think again. Most emails sent over the internet travel in plain, unencrypted form. That means anyone who knows where to look could theoretically intercept and read your most private missives.
So, who could be reading your email?
Google, for a start
Google has revealed that it does scan the emails that pass through its Google Mail service. The tech giant has has stated this in submissions aiming to dismiss a class action lawsuit that accuses it of breaking wiretap laws.
Its position regarding the reading of our emails goes like this:
"Just as a sender of a letter to a business colleague cannot be surprised that the recipient's assistant opens the letter, people who use web-based email today cannot be surprised if their communications are processed by the recipient's ECS (electronic communications service) provider in the course of delivery."
This analogy fails to acknowledge the fact that when an assistant opens their boss’s mail they do so with agreed or implicit prior consent and they are subject to confidentiality agreements.
I have always maintained that writing to someone via email is akin to sending a postcard. The content of the email, just like a postcard, can be read en-route.
Securing your email
Securing your email is easy: you just need to encrypt it. This scrambles every message you send so it can't be understood by people other than the intended recipient.
These days you don't need detailed technical knowledge to use email encryption. Many companies offer email encryption products that handle the technical side of things for you. However, the key is to find one that doesn’t require your recipient to have installed software to decrypt your message and then send you an encrypted reply.
You might also want to find a service run by a UK company and hosted on servers in the EU. This means that UK and EU privacy law will apply — you don't risk getting caught up in the US Patriot Act, which many argue is a good reason to avoid US-based services.
My company offers an email encryption service called Egress Switch.
How to get started
You'll need to decide whether you want a pay as you go encryption service, or something more substantial.
It's also worth looking for a scalable service. You might start out as someone who will use encryption infrequently, for the odd highly-sensitive email. But over time you may decide you want to use encrypted email for all of your business communications.
In the end, though, it’s up to you: if you don’t mind risking Big Brother reading your email then you can do nothing. But if you'd prefer your private messages to stay that way, it's a good idea to adopt email encryption.
- Why you need to archive your email
- Send sensitive information in a self-destructing message
- How to prevent data breaches
Blog provided by Paul Simms of Reflect Digital on behalf of Egress Software Technologies.



